What is a Zero Trust Security Architecture?
Learn how a combination of EDR, NDR, and SIEM/UEBA provides a comprehensive view of an ever-changing threat landscape.
- What is a Zero Trust Security Architecture?
- How does Zero Trust work in practice?
- Why is Zero Trust important? What challenges does it help security teams address?
- Why is Zero Trust difficult to implement?
- What do you need to implement Zero Trust effectively?
- Take a step towards Zero Trust with Open NDR

The Zero Trust (ZT) concept of cybersecurity received a tremendous boost as result of the rapid acceptance of remote and hybrid work environments over the past several years in the wake of the coronavirus (COVID-19) pandemic.
Today Zero Trust is much more than a slogan: It is a bonafide security architecture. It also is an imperative for enterprises that are adapting to the new world of perimeter-free, identity-focused cyber defense. That said, its practical applications are still evolving, and even the most mature use cases require constant monitoring and updates as security teams adapt their existing security and network architecture.
Let’s dive into the concept of Zero Trust—what it is, why it’s important, what challenges it helps security teams address, what challenges it presents, and how network visibility and telemetry plays a crucial role in a strong Zero Trust approach and deployment.
What is a Zero Trust Security Architecture?
The foundation of Zero Trust is just what the name implies: There is no implicit trust anywhere, it is assumed the network is breached and each request must be verified as though it originates from an open network. Every device, user, or request for access is considered untrusted until a multi-step verification process confirms its identity and legitimacy. In a Zero Trust Architecture (ZTA) it is assumed that every device, user, and access request represents a potential threat.
“CISA has been acutely focused on guiding agencies, who are at various points in their journey, as they implement zero trust architecture,” said Chris Butera, Technical Director for Cybersecurity, CISA. The updated maturity model provides a gradient of implementation across the five distinct ZTA pillars to facilitate implementation, allowing agencies to optimize their zero trust architecture incrementally. The five pillars of the Zero Trust Maturity Model are depicted below.
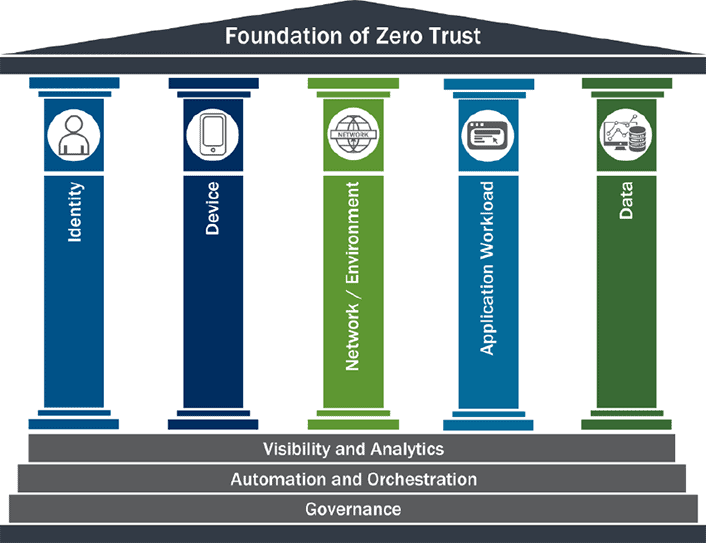
Source:Cybersecurity & Infrastructure Security Agency (CISA)
While there are anywhere from 5 to 7 pillars described in Zero Trust Architectures, the main principles underlying it include:
- Least privilege access. A Zero Trust framework will provide legitimate users with only the privileges needed to complete a specific task. This security posture is enforced by specific policies, and, in most cases, leverages multi-factor authentication (MFA) to identity proof users.
- Identity authentication (rather than location). Zero Trust focuses on the identity of a person or certain device attributes to determine their legitimacy.
- Containment. Microsegmentation of the network is a design goal used to implement additional security controls and minimize the potential spread of a cyber breach or reduce the blast radius.
- Continuous monitoring of the network and other systems. The concept of Zero Trust Architecture (ZTA) extends beyond initial access to include user behavior. Network telemetry can make user behavior visible to the security team in real time, which helps create a baseline of normal network activity and surface anomalous actions that may be evidence of a cyber event.
How does Zero Trust work in practice?
Zero Trust Architectures combine a variety of security best practices and assumes universal adoption, ongoing policy management, continuous monitoring, and regular tuning as the organization learns where its weak spots are in the organization. Of particular importance is an identity and access management (IAM) policy that requires every user, no matter what their role, to employ multi-factor authentication (MFA) such as biometrics or behavioral signatures. A key design feature of ZTA is the inclusion of device control information in the access decision making process. Device controls can include asset ownership, software integrity, and compliance checks in addition to the use of behavioral patterns as previously seen in UEBA (User Entity and Behavior Analytics) solutions. ZTA policy based decisions combine these two signals to form a more accurate picture of trust.
Once validated, user and device activity can be granted or restricted through well-defined least-privilege protocols. This may mean controlling access to data, applications, services, and company infrastructure via microsegmentation, adding layers of authentication, and policies that govern access. Throughout the Zero Trust journey requirements will change, so the access policies need to be adaptable to support the evolving ZTA.
Zero Trust also depends on best practices it shares with other security concepts, most notably Secure Access Service Edge (SASE). Created by Gartner, SASE is a broader model that incorporates Zero Trust along with other security tools, including firewall as a service, secure web gateway, software-defined wide area network, data loss prevention, and cloud access security broker. While Zero Trust and SASE cover much of the same territory, they are distinct concepts that can be used in conjunction with each other, as well as in concert with other methods, such as data encryption, and tools that enable continuous monitoring of endpoints (e.g. Endpoint Detection and Response — or EDR ), cloud environments, and the network (Network Detection and Response — or NDR).
It’s worth noting that a robust Zero Trust Architecture requires a large number of tools to provide a high level of auditing and enforcement. Most security teams will need to implement an integration and coordination solution, such as a security orchestration, automation, and support (SOAR) platform, to keep the overall solution automated and manageable.
Why is Zero Trust important? What challenges does it help security teams address?
Zero Trust represents a clean break from the traditional perimeter defense, which assumes that everything that happens on an organization’s internal network is legitimate and can be trusted. Given the expansion (or disintegration) of traditional perimeters due to: remote and hybrid work; migrations to the cloud; the proliferation of IoT devices; the evolving tactics of malicious actors; and ongoing insider threats, relying solely on this traditional perimeter defense model simply is no longer effective for the security of most enterprises.
The adoption of Zero Trust Architecture tenets is a timely response to the increased acceptance of remote and hybrid work environments over the past several years that has helped dismantle the traditional perimeter defense. With employees on the move, third parties requiring access, growth in cloud applications, and the popularity of mobile and BYOD device policies, enterprises need to harden access at every level.
The escalating threat posed by criminal and state-sponsored cyber attacks has been another factor in Zero Trust adoption. A May 2021 executive order included a specific recommendation for government agencies to adopt a Zero Trust Architecture based on an adoption strategy outlined by the National Institute of Standards and Technology (NIST); the U.S. Cybersecurity & Infrastructure Security Agency (CISA). Additionally, CISA has created a Zero Trust maturity model that aims to assist agencies in the development of zero trust strategies and implementation plans. The CISA Zero Trust Maturity Model is one of many roadmaps that agencies can reference as they transition towards a zero trust architecture.
In the day-to-day, a Zero Trust Architecture and adherence to its principles can benefit security teams that are tasked with protecting more systems, devices, and access points than ever before. In the event of a breach, the microsegmentation of networks and devices, coupled with least privilege, can help restrict an attacker’s lateral movement, and minimize the “blast radius” of a breach.
Why is Zero Trust difficult to implement?
While Zero Trust Architectures are well-established as a concept and a valued objective, implementing a defined architecture is still a significant challenge for many organizations. One reason is that there is no one-size-fits-all approach: Every organization must undertake a distinctive approach, based on the needs of its employees and business model, risk tolerance, and reliance on assets it does not fully control (i.e., cloud deployments, IoT devices, or systems controlled by partner organizations). Before implementing a ZTA there should be a careful analysis that focuses on the most important data, applications, and systems, around which the Zero Trust Architecture should provide the strongest security defenses. This will be an iterative process that will need to be revisited and updated regularly throughout the organization’s security journey.
Additionally, some organizations may find it challenging to generate support for a ZTA, especially if employees perceive that more rigorous access controls may create extra steps and slow down workflows.
For instance, a company currently uses a virtual private network (VPN) for remote access, but recently the security team learned that the VPN identity management capabilities are insufficient and malicious actors could exploit credentials to gain remote access. Furthermore the VPN does not have intrusion detection for authenticated users, so the security team has no means to defend against this attack vector. Changing the security posture and introducing the more rigorous Zero Trust Architecture principles may be difficult.
What do you need to implement Zero Trust effectively?
Monitoring on the level required to approach a robust Zero Trust Architecture depends on network visibility. The key to enabling a high standard of authentication, authorization, and auditing is compiling sufficient data to provide security with enough context to evaluate any action or request—and respond in real-time.
A Network Detection and Response (NDR) solution can help a security team lay the groundwork for a Zero Trust Architecture by providing a foundation for auditing using a unified data format and data collected specifically for security purposes and interoperability. Importantly, the network data is immutable and it provides an ultimate source of audit about activity within the organization that can enable rapid response and future analysis.
The network data cannot “lie,” since what is communicated, parsed, and recorded over the wire cannot be altered. This telemetry, in turn, can provide strong support for a Zero Trust approach.
Take a step towards Zero Trust with Open NDR
Corelight is the only NDR solution on the market that provides a commanding view of all devices that log onto your network—with access to details such as SSH inferences, DNS query/response, file hashes, TLS connection details, and HTTP content.
Corelight’s Open NDR Platform takes an evidence-based approach that combines the most flexible, community-driven metadata—widely-used open-source Zeek® and Suricata— with smart packet capture (SPCAP) to create an environment for complete network visibility that can dramatically improve mean time to respond (MTTR) to attacks. Security teams utilizing Corelight Open NDR can replace a patchwork of sources (like Netflow or firewall logs) with a single, comprehensive source of rich network telemetry, whether the environment is on-premises, hybrid, or multi-cloud.
Book a demo
We’re proud to protect some of the most sensitive, mission-critical enterprises and government agencies in the world. Learn how Corelight’s Open NDR Platform can help your organization tackle cybersecurity risk.






















