INSIGHT, WITHOUT DECRYPTION
Getting visibility into encrypted traffic can seem impossible, but by ignoring it, you provide attackers an ideal hiding place. The Encrypted Traffic Collection turns network data flows into rich evidence and useful insights—without decryption—so you can understand and mitigate risk. Combining observable elements, like timestamps and packet sizes, with known behavior of protocols, the ETC offers a practical approach to visibility that lets you see and act on what matters. It also avoids the heavy financial, privacy, and performance costs of decryption. Read more on the blog.
Corelight Collections are detection sets included with your Corelight subscription and can be activated depending on your needs.
VPN, DNS, and encryption detection
VPN insights
Detect and identify the endpoints that are using VPN connections. Reveal the country the VPN(s) are connecting to and evaluate their appropriateness. Discover when VPNs are unexpectedly being used, at unusual times, or from unexpected systems.
DNS over HTTPs (DoH) detection
Reveal when DNS queries are made to known DNS over HTTPS (DoH) providers to provide insight into DNS traffic that would otherwise be hidden.
Custom encryption detection
Detect connections that are already encrypted without an observed handshake, which can indicate custom or pre-negotiated encryption.
Expected encryption detection
Identify unencrypted connections running on ports where encryption is expected.
RDP authentication inferences
Generate inferences about the method of authentication used by the RDP client.
RDP brute force detection
Reveal when an RDP client makes excessive authentication attempts and also succeeds.
RDP client inferences
Generate inferences about the type of an RDP client used.
RDP excessive channel join detections
Reveal when an RDP client exceeds a set threshold for the number of channel joins.
SSH stepping stones
Determine and log when related SSH connections are seen on the network using statistical analysis.
SSH agent forwarding detection
See when SSH agent forwarding occurs between clients and servers, which may indicate lateral movement where adversaries have compromised SSH credentials.
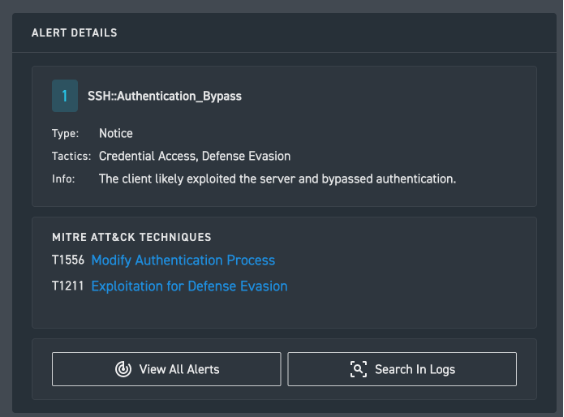
SSH authentication bypass detection
Reveal when a client and server switch to a non-SSH protocol.
SSH client brute force detection
Reveal when an SSH client makes excessive authentication attempts.
SSH client file activity detection
Reveal when a client transfers a file to a server or vice versa.
SSH client keystroke detection
Reveal an interactive session where a client sends user-driven keystrokes to the server.
SSH fingerprinting (HASSH)
Create a hash of every SSH client and server negotiation for use in threat hunting or intel feed matching.
SSH MFA detection
See when SSH connections use multifactor authentication (MFA), which can help analysts rule other explanations for observed timing discrepancies in SSH connections, and help teams monitor external SSH servers for MFA compliance.
Non-interactive SSH detection
Reveal when SSH connections do not request an interactive terminal, but instead use SSH as a port forwarding tunnel, which may indicate malicious SSH tunneling.
SSH reverse tunnel detection
Reveal when a client connects to an SSH server and sends the server an interactive terminal, establishing a reverse SSH tunnel that may indicate malicious SSH tunneling.
SSH scan detection
Infer scanning activity based on how often a single service is scanned.
SSL certificate monitoring
Track expired and soon-to-expire certs, newly issued certs, self-signed certs, invalid certs, change-validation errors, old versions, weak ciphers, weak key-lengths, and bad versions (e.g., TLS 1.0).
SSL fingerprinting (JA3)
Create a hash of every SSL/TLS client and server negotiation for use in threat hunting or intel feed matching.
How it works
The Encrypted Traffic Collection offers unique insights into SSL, SSH, RDP, DNS, and VPN connections, along with top encrypted insights from the Zeek® community like JA3/S, HASSH—all without decryption. It employs Zeek to analyze the timing, sizes, flow direction, and other characteristics of network traffic, and integrates the results into Corelight’s comprehensive suite of evidence and analytics.
ANALYTICS
Corelight Collections
Collections are targeted categories of detections, inferences, and data transformation that provide deeper visibility into adversary activity. They cover encrypted traffic, command and control activity, entity activity, ICS/OT visibility, and more. Detections are viewable through Corelight Investigator, or via a SIEM, XDR, or other analytics platform.