- What is an intrusion detection system?
- A brief history of intrusion detection systems
- Intrusion detection system examples
- The different behaviors of IDS, IPS and firewalls
- The limitations of intrusion detection systems
- How IDS can complement—and be complemented by—a strong security stack
- Conclusion: Invest in the right combination of IDS and more advanced tools

What is an intrusion detection system?
An intrusion detection system (IDS) is an alert-based system that monitors and analyzes network traffic for evidence of malicious or unauthorized activity. When it detects anomalous behavior, such as attempts to gain access to areas without proper authorization or exploit vulnerabilities in an endpoint or application, security teams receive a notification, which leads either to direct response or further investigation. An intrusion detection system cannot remediate a security event on its own. Historically, intrusion detection systems have worked in conjunction with intrusion prevention systems (IPS), which can actively block traffic or network packets, modify access control, or undertake other mitigation tactics.
Important as these capabilities are, many experts find traditional intrusion detection system capabilities too limited to handle the ever-increasing volume and speed of network traffic. While still executing important functions, their limitations necessitate the add-on of tools that can handle the disintegration or expansion of network perimeters, the increase in encrypted traffic, and the increasingly stealthy post-compromise activity of attackers who have learned how to evade IDS alerts.
Close the gap between alert and answer
Knowing which alerts are dangerous, and which aren't, isn’t easy. Here's why:
- The average SOC gets 10,000 alerts per day.
- Most SOCs have only 2 to 10 analysts reviewing events.
- There are only 480 minutes in an 8-hour shift
- 1,000 alerts / analyst = ~2 alerts per minute
Close the gap between alert and answer to lower response times and reveal attack impact quickly.
![]()
A brief history of intrusion detection systems
The IDS journey started thirty years ago when increasing enterprise network access spawned a new challenge: the need for user access and user monitoring. As day-to-day operations grew increasingly dependent upon shared use of information systems, levels of access to these systems and clear visibility into user activity was required to operate safely and securely.
Much of the initial headway on IDS was made within the U.S. Air Force. In 1980, James P. Anderson, a pioneer in information security and member of the Defense Science Board Task Force on Computer Security at the U.S. Air Force, produced “Computer Security Threat Monitoring and Surveillance,” a report that is often credited with introducing automated intrusion detection systems. Soon after this report was released, the first model was built, born out of the same methods used by anti-virus applications: rule-based systems that constantly scanned and compared network traffic against a list of known threats.
During the late 1980’s, with a growing number of shared networks, enterprise system administrators all over the world began adopting intrusion detection systems. However, IDS presented a couple problems. First, it could only alert on known issues that had been categorized as threats on a signature list; zero-day attacks could compromise a network’s security. Second, the constant scanning and updating of a signature list was cumbersome and significant resource drain.
Intrusion detection system examples
In most cases, an intrusion detection system is either a network-based intrusion detection system (NIDS), monitoring all network traffic, or a host-based intrusion detection system (HIDS), in which it deploys on a single, protected device. It can also be deployed to monitor protocols between devices and servers, application-specific protocols, cloud-environments, or some combination (known as hybrid IDS) of these capabilities.
IDS monitoring is outside of the network, and often utilizes a TAP or SPAN port to analyze traffic in real time. It looks for any activity that is anomalous or carries signatures of established attack methods. It inspects packets for any evidence of malicious action, such as network or port scans, and attempts to exploit known network vulnerabilities. Whenever any suspicious or known attack activity is detected, the IDS generates an alert or log data.
The detection methods of an intrusion detection system typically are orientated in one of two ways:
- Signature-based, in which the system searches for pattern evidence of known attack signatures. The limitation of this method is evident when we consider the reality of zero-day attacks that do not match any known signatures.
- Anomaly-based, which leverages machine-learning capabilities to create more sophisticated models of normal network traffic and behavior. This can be a more effective method for detecting novel attack methods. However, it can also generate more false positives, since the anomalous behavior it detects may be unusual, but not illegitimate.
The different behaviors of IDS, IPS and firewalls
Since intrusion detection systems are passive systems that alert security teams but take no remedial action, they are often used in conjunction with intrusion prevention systems (IPS) and firewalls.
Firewalls, whether they are hardware or software, monitor north-south traffic, but also apply a set of security rules to block malicious or unauthorized activity. They apply filters and reject any traffic that runs afoul of preconfigured rules.
IPS and IDS are sometimes talked about as being two parts of one system, but it’s helpful to distinguish their basic functions.
IDS monitors network traffic for suspicious activity and alerts when such activity is discovered. While anomaly detection and reporting are the primary functions, some intrusion detection systems are capable of taking actions when malicious activity or anomalous traffic is detected, including blocking traffic sent from suspicious Internet Protocol (IP) addresses.
An IDS can be contrasted with an IPS, which monitors network packets for potentially damaging network traffic, like an IDS, but has the primary goal of preventing threats once detected instead of just detecting and recording threats.
Like firewalls, IPS is designed to prevent security threats by identifying and blocking malicious traffic, network packets, or connections, or modifying access control rules if there is evidence of attempted unauthorized access. Unlike IDS, it’s a proactive function.
IPS and firewalls can work in conjunction with intrusion detection systems to bring the proactive mitigation capabilities IDS lacks. Like IDS, they have become more sophisticated over time. Modern IPS also leverage machine learning and behavioral analysis to combat more sophisticated and novel attacks. Next-generation firewalls are capable of packet capture and deep-packet inspection, and can integrate with advanced threat intelligence systems. Learn more about the differences between IDS vs. IPS here.
The limitations of intrusion detection systems
What an IDS does, it generally does well, but it’s important for security teams to recognize its limitations, how attackers can outmaneuver its detection capacities, and how it might make the security operations center’s (SOC) work more challenging.
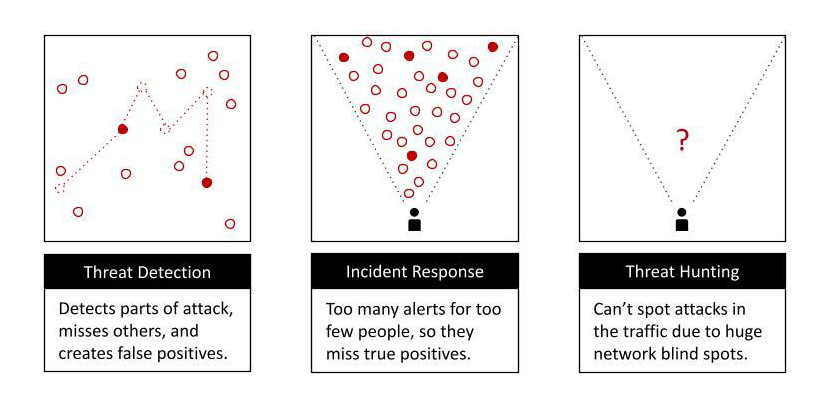
Among the potential issues there are:
- False positives and false negatives. False positives result in alarms, which do not necessarily mean that normal functions will be impacted. But SOCs are obligated to investigate them, which can waste precious time and resources when there is smoke but no fire. The false negative simply means the intrusion detection system failed to detect the malicious activity.
- Attackers can defeat or circumvent intrusion detection systems. Malicious traffic can be disguised or shielded to avoid IDS detection. Packets can be broken into fragments that elude intrusion detection systems and then are reconstituted at the IP or application layer. There are methods for flooding network protocols with an excess of traffic that makes it exceedingly difficult for the IDS to detect the malicious traffic amidst the noise. Program code can be made unreadable, also resulting in IDS evasion. Additionally, attackers have learned how to leverage advanced encryption protocols that intrusion detection systems are not able to read.
- Network complexity. With traffic increasing and network topologies, protocols and applications becoming increasingly complex, many intrusion detection systems are not able to keep pace with the data flows. At the same time, an IDS can be extremely resource intensive in terms of processing power, storage, IT budgets, and the capacities of security teams, who must be trained to use the system and take the time to respond to alerts.
- Reliance on known knowns. In the case of signature-based IDS, effectiveness is restricted to known attack patterns. It is ineffective against novel and unknown threat signatures. What’s more, attackers can modify the characteristics of known attacks to evade intrusion detection systems.
Corelight’s suite of network security analytics can help your enterprise achieve defense-in-depth and reveal known and unknown threats. Learn more about Corelight’s analytics & detections.
How IDS can complement—and be complemented by—a strong security stack
Intrusion detection systems are still an important part of most enterprises’ cyber defenses. They can assure that communications are legitimate, help identify non-malicious bugs, ensure compliance, and hold the line against established malicious attack patterns. But given the rapid evolution of cyberattacks and network complexity, it’s important to use an IDS in conjunction with other tools. Firewalls, IPS, and antivirus software can all be part of the package, but more advanced solutions are combining the features of all these tools while adding more robust capabilities that can generate more granular and targeted network analysis.
In particular, network detection and response (NDR), leverages machine learning and other advanced analytics to augment IDS’s network monitoring capacities.
NDR can harden and extend IDS capabilities in several directions, including:
- Detection of novel threats. NDR has the capacity to analyze network traffic in its entirety, rather than focusing on specific, known malicious signatures. It can be seen as an extension and improvement on anomaly-based intrusion detection systems.
- Provide alert context. Security teams waste valuable time and energy chasing false positives. NDR can present analysts comprehensive context that includes which devices are trying to communicate, which ports are being used, and how much data is included in a transfer. The added context can help reduce the number of false positives by excluding more anomalous, but legitimate, traffic from SOC analysis.
- Insights into encrypted traffic. The most advanced NDR will monitor encrypted traffic by leveraging network security solutions, such as Zeek®, to analyze its timing, size, flow direction and other characteristics. Combined with advanced analytics, security teams can give defenders means to spot attack characteristics and methods without necessitating encryption, which is often cost-prohibitive.
- Bundle and streamline capabilities. Strong NDR can include platforms and dashboards that integrate feeds from disparate security tools and simplify SOC workflows. This can give back time and resources to overworked teams by helping them prioritize tasks and respond efficiently to legitimate threats.
Invest in the right combination of IDS and more advanced tools
Intrusion detection systems remain an important part of the security stack for most enterprises. It provides a solid baseline for network behavior, regulatory compliance, reliable redundancy for other security technologies, and solid analytics that can help SOCs pinpoint operational problems and known attack patterns.
For an advanced threat detection and protection solution, intrusion detection systems are a complementary piece of a defense-in-depth approach that layers in technologies such as next-generation firewalls, IPS, and particularly NDR, which supplies the advanced analytic capacities that can keep SOCs in front of known and unknown threats, even before they gain a foothold on the network.
Corelight’s Open NDR Platform is deployable on premises and in SaaS formats, and transforms activity into evidence via advanced IDS and Smart PCAP solutions. Learn more about Open NDR.
Book a demo
We’re proud to protect some of the most sensitive, mission-critical enterprises and government agencies in the world. Learn how Corelight’s Open NDR Platform can help your organization tackle cybersecurity risk.





.jpg?width=1000&height=561&name=An%20alert%20has%20fired.%20Now%20what_%20final%20(1).jpg)
