CLOUD SECURITY SOLUTIONS
Cloud environments are rapidly expanding. Learn about what you need to protect, and how network detection and response can support a comprehensive cloud security strategy.
Why are cloud security solutions essential?
Cloud security solutions combine technology, processes, threat intelligence, and policies that are developing rapidly as organizations move more operations to their multi-cloud environments. They are essential to maintaining safe work environments and protecting organizations’ most critical data and assets from misuse or compromise by malicious actors.
Cloud adoption has generated huge windfalls for service providers. The utility, cost savings, and increased functionality offered by cloud capabilities all but ensure that organizations in every industry and in the public and private sectors will continue to invest in this infrastructure.
Rapid adoption has also brought complexity, security challenges, and increased cybersecurity risk. Organizations need to take steps to visualize and secure their cloud deployments, protect data, user identities, and counter emerging threats.
Gartner predicted global spend on public cloud services would reach:
Different cloud types
Hybrid cloud
combination of private and public cloud
Virtual private cloud
private cloud hosted within a public cloud
Multi-cloud
using services from more
than one public cloud provider
Why is cloud security a challenge? The cloud is a target-rich, dynamic ecosystem with a malleable threat landscape
Security teams are scrambling to understand cloud environments that can be rapidly deployed, expanded, and destroyed.
At the same time, threat actors are exploiting vulnerabilities and misconfigurations that even advanced cybersecurity teams can easily overlook. The challenge of visualizing, understanding, and protecting dynamic cloud ecosystems requires adaptability and innovation. Security teams also need tool sets that help them manage the complexities of hybrid and multi-cloud deployments.
More sensitive data moves to cloud environments every quarter
Data protection is still a work in progress. Much of cloud-stored data lacks sufficient encryption protection, even in some of the most highly regulated industries.
Malicious actors are exploiting cloud security solutions
Configuration errors, lack of oversight, and the adoption of insufficiently secured cloud applications expands the attack surface organizations as they move to cloud environments.
Cloud security solutions are also evolving rapidly. But do they address your organization’s challenges?
Choosing the right combination of cloud security solutions and strategies requires a comprehensive understanding of the challenges that all cloud security teams face—as well as the unique issues presented by each specific cloud deployment.
Challenges to cloud security
Cloud service providers (CSPs) such as AWS, GCP, and Azure provide some cloud security features for their cloud infrastructures.
The shared responsibility model model requires customers to take a proactive approach to securing their applications, permissions, workloads, and connections between their cloud services, while also ensuring compliance.
In many cases, cloud users introduce security blind spots when they lose sight of the boundary between their provider’s coverage and their own.
Even when the shared responsibility model is well understood, organizations face a variety of other challenges that complicate or undermine security in their cloud deployments:

| Cloud SECURITY Challenge | Context | Pain Point |
|---|---|---|
|
Visibility gaps |
New cloud environments and workflows can spin up or dissolve rapidly depending on need. Containers, hosts, servers, traffic, IP addresses, and other parts of the environment do not remain static, as in traditional network architectures. |
Attaining and maintaining visibility in this environment requires investment in cloud security solutions that are built to manage the dynamism of the cloud. |
|
Configuration management |
A key advantage of cloud environments is their scalability. Organizations can quickly add resources, virtual machines, applications and storage throughout their cloud architectures. Each deployment needs to be configured at the cloud and host layer and properly integrated with any connecting systems. |
Given the rapid rate of change in these environments, configurations require regular assessment and maintenance. Misconfigurations are common. Those introduced by improper use of infrastructure as code (IaC) tools, which automate and simplify cloud provisioning, can be particularly harmful. |
|
Credential and access |
Identity and access management (IAM) and privileged access management (PAM) are essential to cloud deployments and typically the responsibility of cloud users. |
IAM and PAM can become challenging when cloud environments scale rapidly, involve new APIs or introduce complexity to management systems. It can also be difficult to apply these processes across multiple cloud environments. In some cases, users may sacrifice the security of a robust IAM process for ease of use and deployment. |
|
Tool sprawl |
Organizations can adopt more capabilities, workloads and databases. |
Organizations may often adopt more capabilities, workloads, databases and monitoring tools than they can effectively manage. They may also need to consider the implications of shadow IT that skirts cloud management policies and systems. |
|
Compliance |
As more critical and sensitive data moves to cloud environments, organizations increasingly must ensure that certain data storage and cloud-based networks are properly segmented to stay compliant with industry or government regulations. |
The rapid adoption of new cloud capabilities and a lack of visibility increases the likelihood that architectures are not in full compliance. |
|
Skill gaps |
Public cloud infrastructures vary from provider to provider, and they are different from private cloud infrastructures. Developers and security teams need a full understanding of each type of infrastructure they deploy and the skills and experience to maintain compliance and security. |
As with many aspects of cybersecurity, many organizations lack analysts and developers with sufficient knowledge of cloud deployments, IaC and configurations. There is also a pressing need to provide security teams with tools that automate processes and streamline workflows and alerts to accelerate detection of security threats and improve cloud protections. |
Cloud-native security solutions
Security teams depend on vendors to assist them with cloud complexities and challenges. Cloud-native security solutions have matured in tandem with organizations’ digital transformations. Depending on an organizations’ needs and the skills of its security teams, combining tools and capabilities can provide a baseline for cloud security.
In general, cloud security solutions and processes should enable security operations centers (SOCs) to identify security threats, prevent intrusions or misconfigurations, analyze potential threats and mitigate existing vulnerabilities or breaches across their cloud deployments.
A partial list of security tools for cloud environments includes:
- Cloud workloads may include virtual machines, containers, applications, software components, storage functions and more.
- CWPP tools or platforms help analysts visualize their workload deployments and uncover vulnerabilities introduced by misconfiguration, improper use or other factors.
- CWPP should help organizations unify their view of their cloud deployments and scale their operations as needed.
- CSPM helps organizations evaluate their security SaaS, IaaS and PaaS and other parts of cloud infrastructure in terms of security risk, security policy requirements and usage practices.
- It can also detect potential misconfiguration and enhance continuous monitoring capabilities across the infrastructure and improve incident response times.
- Cloud workloads are connected to and supported by an increasing number of applications.
- CNAPP solutions pull together a variety of tools that streamline and secure app development, production and deployment.
- They may extend to cover APIs, containers and channels used by DevOps teams.
- Most cloud security solutions include tools or processes and frameworks that help IT teams manage access and privileges (e.g., IAM and PAM), data loss protection, and management of policies regarding use of applications and data.
Network detection and response is a tool well-suited to cloud security
Network detection and response (NDR) provides a critical complement to the cloud security stack for many organizations, especially those for whom migration to cloud environments is a new or ongoing process.
The process of shifting workloads to cloud environments leaves most organizations working to integrate and secure on-premises networks as well as their scaling cloud networks. In many cases, deploying a NDR solution that extends to cloud and complements cloud security solutions is the key to attaining a unified visibility necessary to modern security.

NDR’s core value is that it can extract and deliver in-depth, enriched detail of activity that occurs within dynamic and rapidly evolving cloud networks and across the cloud’s control and data planes. Packet mirroring and traffic cloning help make NDR’s telemetry analysis capabilities as relevant to cloud environments as it is for on-premises networks.
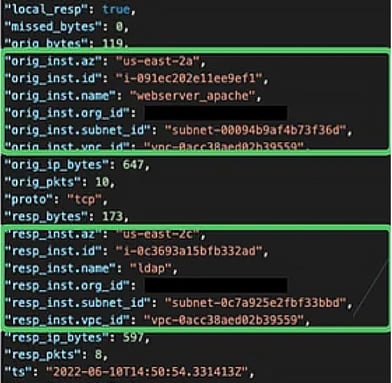

Many organizations find that flow logs tell an incomplete story of how data travels across their networks, how users interact with it and how developers are configuring new environments.
A best-in-class NDR solution can deliver a number of benefits to the cloud security stack compared to cloud native solutions:
| Cloud Native | NDR | |
|---|---|---|
|
Enhanced visibility and monitoring of multiple cloud components |
Specific to each control plan, container, virtual network or serverless environment. |
With advanced analytics, NDR can detect many active threats and vulnerabilities that other tools can miss. Network telemetry can reveal lateral movement by malicious actors, abnormal or improper user behavior and other risks. |
|
Threat hunting and incident response |
Longer MTTD and dwell times |
The analytical insights provided by NDR can reduce mean time to detect and respond to threats. They can also provide advanced analysts with a powerful combination of historical data and real-time analytical capability that can fuel proactive threat hunting that can uncover network inconsistencies or evidence of malicious actors that automated detection tools may miss. |
|
Compliance monitoring and validation |
Shared responsibility unique to each environment. |
NDR helps analysts confirm or document policy or regulatory compliance within their cloud environments and identify areas where controls are insufficient or violated. |
|
Scalability |
Single source analysis, no synthesis and disparate data flows. |
NDR platforms with full cloud capabilities will scale with cloud deployments and maintain connections between network data and cloud control plane data. They should also be capable of analyzing network data from any source. As organizations build new cloud deployments and destroy others, NDR should keep pace and help security teams synthesize disparate data flows. |
What to look for in an NDR cloud security solution
While every organization will have unique requirements, they can measure the performance and potential value of an NDR platform in terms of a few metrics:

Why choose Corelight for your NDR cloud security solution?
Corelight is an established partner with the main cloud service providers. Our sensors for GCP, AWS and Azure transform cloud traffic into comprehensive, correlated evidence that helps organizations attain the complete visibility needed to keep pace and alert as cloud deployments evolve.


Based on the network monitoring platform Zeek, Corelight’s Open NDR is an agnostic compiler of network traffic, L7 metadata, Smart PCAP, extracted files and formats that can work with any SIEM or cloud-based security apparatus, including CWPP, CSPM, CNAPP and more.
Zeek monitors traffic and allows defenders to passively observe traffic patterns endpoint detection and cloud-based detections often miss.
Corelight’s embrace of the open source community delivers the most up-to-date threat intelligence to analysts and informs our commitment to transparency around the use of data in our ML-based detection models.

Ready to learn more? Visit our Cloud Solutions page, learn about our Cloud Sensors, or schedule a demo today.
Book a demo
We’re proud to protect some of the most sensitive, mission-critical enterprises and government agencies in the world. Learn how Corelight’s Open NDR Platform can help your organization mitigate cybersecurity risk.












