CORELIGHT + MICROSOFT SECURITY
- Maximize attack visibility
- Prioritize security alerts
- Streamline and accelerate investigations
- Enable Zero Trust initiatives
Corelight pre-correlates network logs with endpoint data from Microsoft Defender.

SUPERCHARGE MICROSOFT SECURITY OPERATIONS PLATFORM WITH POWERFUL NETWORK EVIDENCE
Corelight transforms network traffic into comprehensive, protocol-rich evidence that Microsoft unified SecOps customers can use to optimize their threat detection and response capabilities. By correlating metadata from over 50 protocol logs, Corelight gives SOC teams a clear picture of all network activity across their organization, including all IT, IoT, and ICS networks, so they can find and respond to threats quickly and easily. By pre-correlating Corelight logs with unique device IDs provided by Microsoft Defender for Endpoint, SOC teams can pivot seamlessly between NDR and EDR data, as well as identify unmanaged endpoints in real-time. Powered by Microsooft Security Copilot, Sentinel customers can elevate their security posture and prevent attacks while providing more automation and intelligence.
- Complete network visibility across hybrid environments, including IT, IoT, and ICS
- Quickly pivot between pre-correlated network telemetry and endpoint data
- Simplify investigations with risk-based alert prioritization
- Boost analyst productivity with real-time contextualized alerts
Corelight for Microsoft security operations platform
Rich Corelight network evidence powers the Microsoft unified SecOps platform through its common data model and user experience.
CORELIGHT FOR MICROSOFT SENTINEL
Along with native data integration, the Corelight App for Microsoft Sentinel includes pre-defined workbooks (dashboards), sample queries, and analytics rules that make SOC teams more efficient and effective.
CORELIGHT FOR MICROSOFT DEFENDER
Simplify investigations and prioritize alerts according to real-time risk to the enterprise with pre-correlated network, endpoint, and vulnerability data.
Gain control of the cloud
Corelight Cloud Security Solutions provide complete network visibility in the cloud by transforming cloud traffic into security-centric evidence that can fuel your global threat detection and response program.

Modernize your SOC with an advanced SOC Visibility Triad foundation
Integrating Corelight network evidence into Microsoft Sentinel enables security analysts to start their SOC modernization journey by pairing innovative, Zeek-based NDR with Microsoft’s industry-leading Defender platform. By enriching Corelight logs with Defender endpoint and vulnerability data directly in the Corelight Sensor, SOC analysts can streamline and accelerate investigations, while prioritizing threats based on current risks to the environment. Extending this with Microsoft Sentinel and Security Copilot can further simplify complex and time-consuming daily workflows with the power of AI.
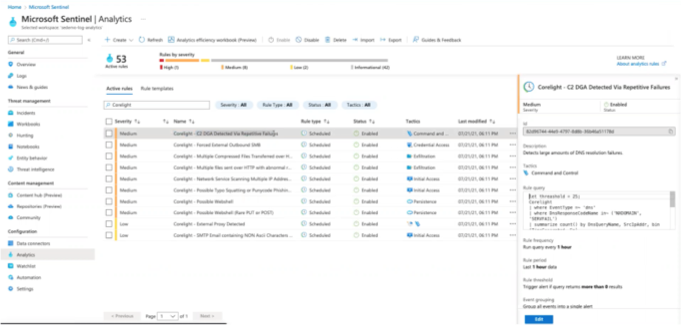
Network Asset Discovery & Inventory
Enhance visibility and security for devices across diverse networks by combining Microsoft Sentinel with Corelight’s Open NDR platform. Our Entity Collection and ICS/OT Collection help you discover and inventory IT and OT assets—whether managed or not.

Detect and disrupt cloud-specific threats
Securing multi-cloud environments presents significant challenges due to the expanding attack surface and constant evolution of cyber threats and ever-changing network topology. See how to effectively mitigate limited visibility, missed detections and inefficient response times.