Corelight + Microsoft Security
- Maximize attack visibility
- Streamline and accelerate investigations
- Prioritize security alerts
- 1-click endpoint isolation
Corelight pre-correlates network logs with endpoint data from Microsoft Defender.
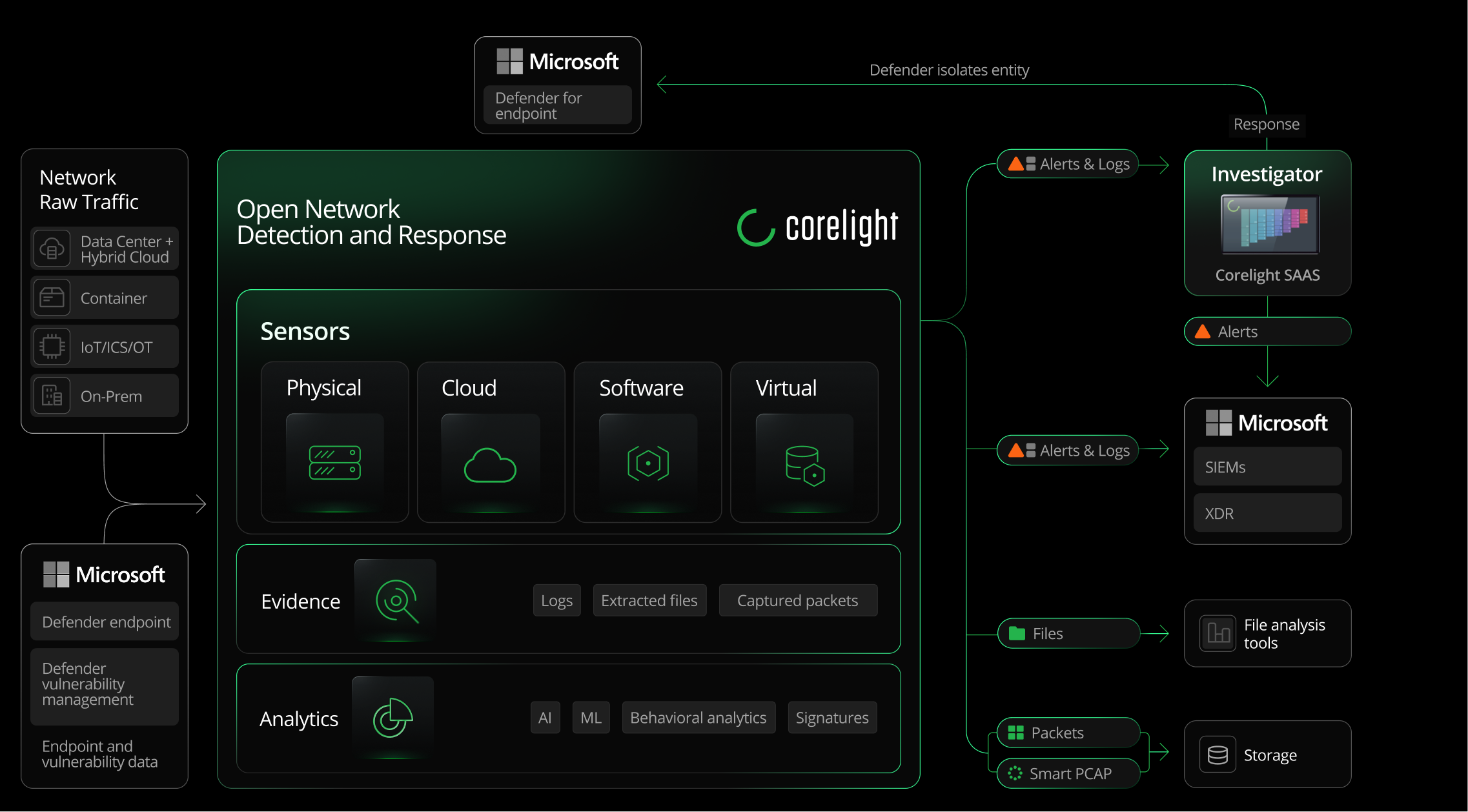
Supercharge Microsoft security operations platform with powerful network evidence
By transforming all network traffic into rich comprehensive evidence, Corelight gives security teams using Microsoft Sentinel the visibility to understand exactly what is happening across the enterprise. Along with native integration with Microsoft Sentinel, Corelight also integrates with Microsoft Defender for Endpoint and Microsoft Defender Vulnerability Management to help streamline investigations, accelerate responses, and remediate incidents quickly and easily.
For instance, Corelight pre-correlates its logs and detections with endpoint and relevant vulnerability data from Defender directly at the sensor, so organizations can better understand and prioritize the most vulnerable endpoints across the enterprise. Going one step further, this unique integration enables fast and easy isolation of those endpoints that show signs of compromise, such that when Corelight detects a compromise, analysts can use Corelight Investigator to quickly assess the threat and isolate devices with a single click.
- Complete network visibility across hybrid environments, including IT, IoT, and ICS
- Quickly pivot between pre-correlated network telemetry and endpoint data
- Simplify investigations with risk-based alert prioritization
- Easily identify and isolate vulnerable and compromised hosts with one click

Corelight for Microsoft Security operations platform
Rich Corelight network evidence powers the Microsoft unified SecOps platform through its common data model and user experience.
Corelight for Microsoft Sentinel
Along with seamless data integration, the Corelight App for Microsoft Sentinel includes intuitive dashboards, pre-defined workbooks , sample queries, and analytics rules that make SOC teams more efficient and effective.
Corelight for Microsoft Defender
Simplify investigations and prioritize alerts according to real-time risk to the enterprise with pre-correlated network, endpoint and vulnerability data. Easily isolate vulnerable hosts with one click.
Azure Virtual Desktop (AVD)
Designed to meet the security compliance requirements of U.S. Federal agencies and commercial organizations deploying Microsoft’s Azure Virtual Desktop environments.
Gain control of the cloud
Corelight Cloud Security Solutions provide complete network visibility in your Microsoft Azure cloud by transforming cloud traffic into security-centric evidence that can fuel your global threat detection and response program.

Modernize your SOC with an advanced SOC visibility triad foundation
Integrating Corelight network evidence into Microsoft Sentinel enables security analysts to start their SOC modernization journey by pairing innovative, Zeek-based NDR with Microsoft’s industry-leading Defender platform. Intuitive dashboards provide at-a-glance views of an organization's security posture and visual insights into potential threats using real-time network telemetry. With summary charts, counters, and maps, SOC analysts can quickly discern trouble spots and drill down into details to validate threats. This clarity and guidance provides focus where it's most needed, ultimately accelerating investigations and response times while streamlining workflows.
By enriching Corelight logs with Defender endpoint and vulnerability data directly in the Corelight Sensor, SOC analysts can streamline and accelerate investigations, while prioritizing threats based on current risks to the environment. Extending this with Microsoft Sentinel and Security Copilot can further simplify complex and time-consuming daily workflows with the power of AI.

Extended network asset discovery & inventory
Enhance visibility and security for devices across on-premise, multicloud, Operational Technology (OT), and Internet of Things (IoT) environments. Corelight’s extensive visibility of all network activity helps identify unmanaged and unknown endpoints across the environment that can then be inventoried and managed by Microsoft Defender for Endpoint. Corelight’s ICS/OT Collection helps discover and inventory IT and OT devices unable to support an agent as an ideal complement to Defender for Endpoint.
Detect and disrupt cloud-specific threats
Securing multi-cloud environments presents significant challenges due to the expanding attack surface and constant evolution of cyber threats and ever-changing network topology. See how to effectively mitigate limited visibility, missed detections and inefficient response times.
