Read the Gartner® Competitive Landscape: Network Detection and Response Report
Read the Gartner® Competitive Landscape: Network Detection and Response Report
START HERE
WHY CORELIGHT
SOLUTIONS
CORELIGHT LABS
Close your ransomware case with Open NDR
SERVICES
ALLIANCES
USE CASES
Find hidden attackers with Open NDR
Corelight announces cloud enrichment for AWS, GCP, and Azure
Corelight's partner program
10 Considerations for Implementing an XDR Strategy
Corelight for the everywhere cloud
January 17, 2023 by Ed Amoroso, founder and CEO of TAG Cyber (guest)
Editor's note: This is the first in five-part series authored by Ed Amoroso, founder and CEO of TAG Cyber, which will focuses on how the Corelight platform reduces network security risks to the so-called Everywhere Cloud (EC). Such security protection addresses threats to devices and assets on any type of network, including both perimeter and zero-trust based.
As virtualization continues to drive enterprise computing design, the need for security extends to a concept we refer to as the Everywhere Cloud (EC). This new designation for hybrid computing obviously requires protection of workloads deployed to public clouds. But it also demands protection of applications accessible via SaaS infrastructure, as well as legacy resources that reside behind a perimeter.
While this evolution drives improved application flexibility and lower operating costs for enterprise IT teams, existing security infrastructure is no longer capable to providing sufficient security and compliance. Establishing visibility into workloads, for example, is greatly complicated when hosting is shifted from a data center accessible directly over a flat local area network (LAN) to a public cloud infrastructure requiring external access.
In this series of articles from TAG Cyber’s Ed Amoroso, the use of the Corelight platform is examined in the context of this new EC. The Corelight platform is shown to support visibility, analytics, investigation, and threat hunting required by security teams. These functions are necessary to protect the legacy, cloud, and SaaS-based components of their EC network – as well as the devices that are used to connect to applications.
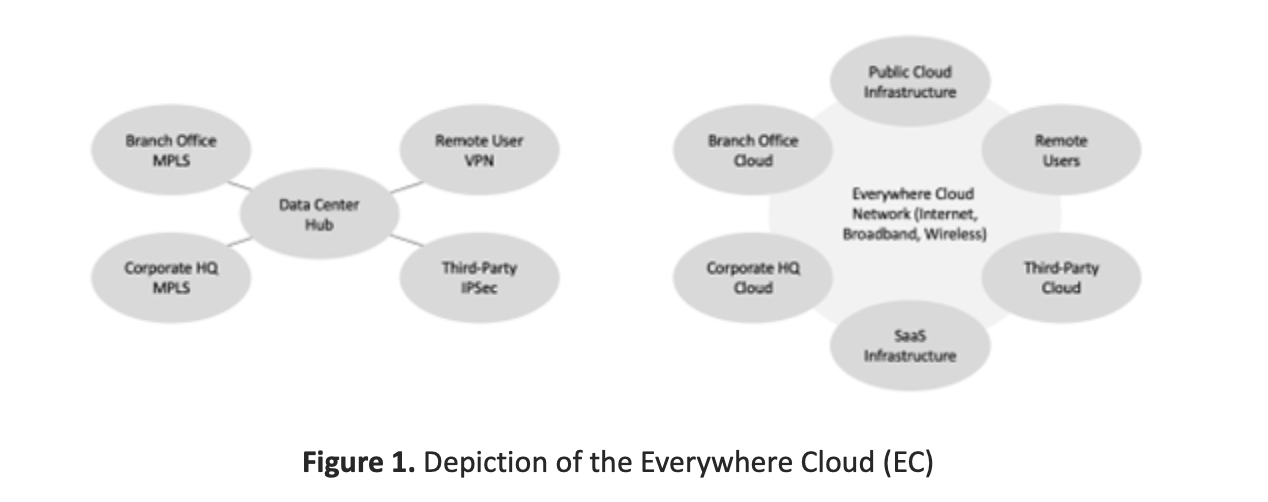
Introduction to the Everywhere Cloud
The so-called Everywhere Cloud (EC) designation references the growing diversity of new enterprise computing services and associated network infrastructure that require advanced cyber security protections. It includes the data, applications, systems, services, and workloads that are now hosted in virtual operating systems located primarily in public cloud.
The EC corresponds closely to the evolution in networking that is on-going today. Traditional hub-and-spoke networks supported a data center-centric view of hosting and securing resources. Most service providers have offered multi-protocol label switching (MPLS) for branch and corporate offices and virtual private networks (VPNS) for remote users and third parties.
This is replaced in the EC with a more open architecture where the network ties together public cloud, remote users, third parties, software as a service (SaaS), and branch offices. The network services supporting EC connectivity include the Internet, broadband (fiber), and modern wireless infrastructure (4G, 5G).
Across this new EC, support for visibility, analytics, investigation, and hunting is complicated by zero trust advances which change the perimeter-based model that has served the security industry for the past twenty years. When EC workloads are hosted in AWS, Azure, GCP, or other public cloud services, perimeters are of no security utility.
Commercial cybersecurity vendor Corelight offers a suite of network security solutions that effectively addresses these functional requirements across the various aspects of hybrid infrastructure with full support for zero trust. Corelight has evolved its toolset to support the EC, which enables its deployment and use in modern network set-ups.
Role of the Network in the Everywhere Cloud
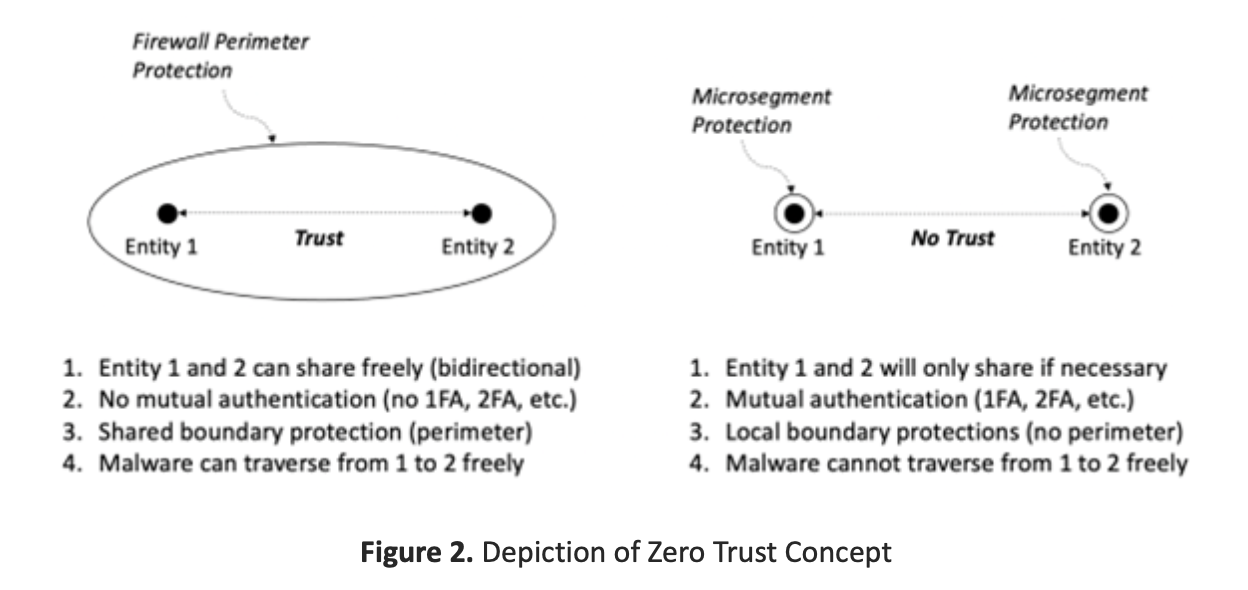
The conventional view of emerging cloud infrastructure usually follows the concept of zero trust. What this means is that sessions established between end-user devices and applications hosted in cloud cannot rely on intermediate perimeter protections. This makes sense because devices can be anywhere, and cloud applications are accessible over the Internet.
Zero trust replaces traditional perimeters, where two entities communicate in an environment of boundary protection. The advantage of this familiar approach is that bidirectional communication is done freely between entities in an enterprise, with no need for one factor or two factor authentication (1FA, 2FA). Unfortunately, malware can also traverse freely.
With zero trust, the two entities must communicate across a network without boundary protection. Mutual authentication is likely required, but this approach highlights the importance of the network to offer security. In fact, with zero trust, the network emerges as an essential security protection to replace prior reliance on perimeters.
This important role of the network has not always been recognized by security practitioners to date. As cloud infrastructure is rolled out to the enterprise, they’ve often focused more on the communicating entities – users and applications – than on the medium that supports and controls such communication, sharing, and dependency.
As a result, many security architects have tended to design their cloud protection approach based on the use of endpoint and application security. The rise of endpoint detection and response (EDR) and cloud security vendors illustrates this emphasis. The problem is that it ignores one of the most fundamental aspects of any remote session – namely, the network.
It follows that the modern enterprise network – with all its technical complexities, access paths, broadband connections, Internet dependencies, and different support models – must be included in any security scheme designed to avoid threats to the emerging EC. Avoidance of network issues results in an incomplete security risk model.
Importance of Network Security for the Everywhere Cloud
The discussion above highlights the role that modern networks play in securing the emerging Everywhere Cloud (EC). This includes wide area infrastructure using carrier fiber, local broadband networks connected to endpoint locations, and the full range of local and carrier-based wireless services. As a result, the security model that applies best to the EC must now include networks, in addition to the existing components as listed below:
- Endpoint Security – Zero trust sessions are initiated by an endpoint PC or device.
- Network Security – The network is now an essential component for EC security.
- Cloud Security – Cloud protection is obviously native to all EC design and operation.
- Application Security – Applications drive EC usage for business and individuals.
- Data Security – The data is the essence of value in any EC-based infrastructure.
These five components comprise the new approach to cloud-based networking the replaces traditional hub-and-spoke set-ups. As one would expect, the need for innovation from commercial vendors is essential – and Corelight offers a range of important security-related features and functions for any organization working to create a transition to the use of EC for its own infrastructure support.
By Ed Amoroso, founder and CEO, TAG Cyber
About the author:
Ed Amoroso is an experienced CEO, chief security officer, chief information security officer (second person to hold the CISO position in history), university professor, security consultant, keynote speaker, computer science researcher, and prolific author (six published books) with a demonstrated history of working in the telecommunications industry beginning at Bell Labs and leading to SVP/CSO position at AT&T. Skilled in cybersecurity, network architecture, wide area network (WAN), managed services, and network design. Strong entrepreneurship professional with PhD in computer science from the Stevens Institute of Technology, and also a graduate of Columbia Business School. Directly served four presidential administrations in cybersecurity, and now serves as a member of the M&T Bank board of directors, senior advisor for the applied physics lab at Johns Hopkins University, adjunct CS professor at the Stevens Institute of Technology, CS department instructor at New York University, and member of the NSA Advisory Board (NSAAB).
Tagged With: network detection response, network security, cloud security, TAG Cyber
Recent Posts