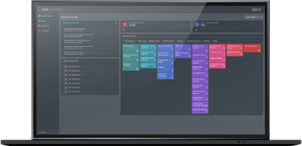
ANALYTICS & DETECTIONS
An evidence-based approach to understanding your environment.
THREAT DETECTION
Illuminate and disrupt attacks hidden in your network. Corelight Open NDR gives you unmatched network visibility and precision-crafted detections that catch what EDR misses. Backed by AI and automation, you move from alert to action—faster.
MULTI-LAYERED DETECTIONS
Corelight delivers a comprehensive suite of network security analytics that help organizations identify more than 100 adversarial TTPs across the MITRE ATT&CK® spectrum. Corelight collects and analyzes contextual data and applies a multi-layered detection strategy that combines AI and machine learning, behavioral analytics, curated signatures, along with threat intelligence to deliver prioritized aggregated alerts based on risk.
- Find insider and LoTL attacks that evade EDR
- Improve overall threat coverage
- Accelerate threat detection and response

The Corelight difference
- Backed by forensic-grade network telemetry, enabling complete visibility into attacker behavior
- Targeted detections for high-value threat behaviors like lateral movement, C2 communication, encrypted traffic misuse, and exfiltration
- Built on open frameworks so you can create or extend detection logic
- Supported by curated community-contributed behavioral detections used by the world’s leading SOC teams
WEBINAR
Why the right network data matters for detecting evasive threats
Register to watch ESG Principal Analyst John Grady and Corelight Field CTO Vincent Stoffer explain how security teams can use network detection and response (NDR) to combat EDR-evasive threats.


AI for threat detection
AI-augmented detections
Corelight applies machine learning and expert-driven models to identify threats like lateral movement, DNS tunneling, and C2 behaviors. Detections are evidence-backed and explainable, enabling faster analyst validation.
AI-enabled ecosystem
Corelight provides structured, context-rich network data that feeds seamlessly into SIEMs, data-lakes and even your own custom-built AI/ML models. Tailor threat profiles to your environment, integrate with threat intelligence, and adapt detections over time without vendor lock-in.
AI-powered SOC
Corelight blends ML-enhanced detections with expert-authored logic and rule sets, delivering alert and activity summaries to maximize clarity and accelerate decisions so you can reduce triage time by 50%. See how it works.
Move from alert to action—faster
EDR BYPASS AND ENCRYPTED TRAFFIC COVERAGE
Detect post-exploitation behavior and threats that evade endpoint controls—such as credential access, DNS tunneling, or anomalous SMB usage. See and detect across east-west traffic, unmanaged devices, and encrypted sessions, where EDR often has blind spots.
HIGH-FIDELITY, LOW NOISE ALERTS
Targeted detections for high-value threat behaviors like lateral movement, C2 communication, encrypted traffic misuse, and exfiltration that are precise and context-aware - dramatically reducing false positives.
FASTER TRIAGE, QUICKER RESPONSE
Corelight enriches detections with AI-driven automations - providing evidence-backed summaries, guided triage, and analyst-ready workflows to accelerate investigations. See the "why" behind every threat, so you can validate and investigate faster.
Top 5 reasons why modern SOCs need multi-layered detections
Faced with increasing attacks, a complex threat landscape, a larger attack surface, and pressure to optimize resources, modern SOCs need multi-layered detections as part of their network security.
Read the top 5 reasons why a multi-layered detection is needed in your framework.

Open NDR - Integrated Analytics Capabilities
Network security monitoring with Zeek®
A complete view of every connection for analysis, investigation, and hunting