SOFTWARE SENSOR
Get all the benefits of the full Open NDR Platform capabilities in places that you couldn't otherwise reach.

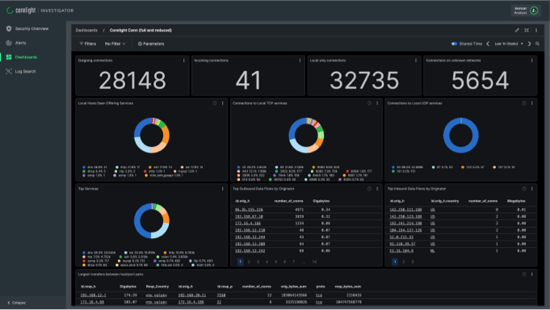
COMPLETE VISIBILITY, EVERYWHERE
The Corelight Software Sensor can be deployed on your existing hardware to provide uniform network evidence across hybrid, multi-cloud, and distributed environments.
- Deploy and scale in minutes
- Focus on evidence, not instances
- Built-in detection, monitoring, and enrichment
- 50-80% reduction in log volume
How it works
The Corelight Software Sensor parses dozens of network protocols and generates rich, actionable telemetry for threat hunting and incident response. Our solution allows customers to get network visibility where they cannot install vendor appliances, providing uniform network evidence across hybrid, multi-cloud, and distributed environments.