What Is Incident Response? 3 Steps to Accelerate Response
Learn what cybersecurity incident response is, including industry frameworks that support incident response, common challenges with incident response, and three steps to accelerate response.
What is incident response?
Cybersecurity incident response refers to the process of identifying, investigating, containing, and resolving any type of cyberattack. It involves a coordinated effort by an organization’s security team to validate the alert, identify the scope of an incident, mitigate the incident’s impacts, prevent further damage from the incident, and restore systems and services to normal operations.
With effective incident response, enterprises can:
- Minimize damage and disruptions to business operations
- Meet compliance requirements and avoid penalties and fines
- Build trust and confidence with customers, partners, and stakeholders
Who is responsible for incident response?
Depending on the enterprise’s size, structure, and industry, incident response may fall to a single team or become a responsibility shared by multiple stakeholders. In many cases, these stakeholders are part of a Security Operations Center (SOC), which may include security analysts, an incident response team, a legal team, a communications team, and threat hunters. Ultimately, however, the responsibility for incident response rests with the organization as a whole, and all employees have a role to play in preventing and responding to security incidents.
Frameworks that support incident response
There are a number of incident response frameworks that can help responders take a timely, effective, and systematic approach to potential and actual cyber incidents. Two frameworks commonly referenced are the NIST Incident Response Framework and SANS Incident Response Process. From there the incident response plan will often feed into business continuity processes, which may pull in non-security teams to manage impacts on operations or communications. In some cases that involve compliance or regulatory oversight, the enterprise legal teams may also play a role in the response framework, although in most cases this team’s role is confined to post-incident response.
(1)
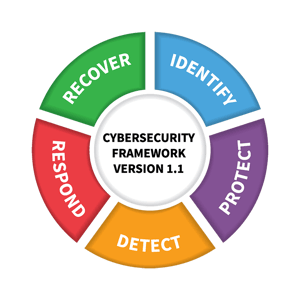
NIST Incident Response Framework
The National Institute of Standards and Technology (NIST) Incident Response Framework provides guidelines and best practices for organizations to prepare for, detect, respond to, and recover from cybersecurity incidents. The NIST incident response framework consists of four key phases: Preparation; Detection and Analysis; Containment, Eradication and Recovery; and Post-Incident Activity.
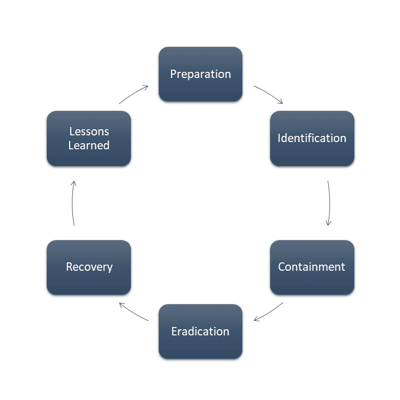
SANS Incident Response Process
The SANS Incident Response Process provides a step-by-step approach to incident response. The framework consists of six phases, including Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned.
(2)
Tools that support incident response
There are a wide variety of legacy, standalone tools that may initiate or support incident response and prevention, such as Endpoint Protection, email filtering, user notification, Intrusion Detection Systems (IDS), Intrusion Prevention Systems (IPS), or SIEM. In some cases forensic tools may also factor into incident response, although they typically come into play in post-incident analysis.
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS and IPS both monitor network traffic and analyze traffic patterns for evidence of potential security threats (e.g. suspicious IP addresses or unusual traffic volume). The primary difference between an IDS and IPS is that security teams can use IPS tools to take action to remediate some threats (such as blocking suspicious IP addresses).
SIEMs and log correlation tools
Log analysis tools are used to analyze and correlate logs from different sources, such as applications, servers, NDR, and EDR. The analysis helps identify security incidents and generate alerts that are sent to the incident response team for further investigation.
Endpoint detection and response (EDR)
EDR can deploy on any endpoint, and can deploy intelligent sensors that automate incident detection and enable response. These tools also generate relevant log data and timelines that can be scanned in later forensic investigations. In many environments, EDR represents a strong frontline defense that integrates well with network detection and response (NDR), SIEM, and XDR.
Digital Forensic tools
Digital forensic tools are used in specialized circumstances, and in most cases they are not part of routine incident response. However, in certain cases a specialized forensic team may use forensic tools to analyze disk images, and other data to identify indicators of compromise (IOCs) and determine the scope of the incident. Incident response teams use forensic tools to identify the root cause of incidents and to provide evidence for legal and regulatory purposes.
Many response teams make use of toolsets and processes that pull incident response and digital forensics into a more holistic task. Security researchers and vendors increasingly approach digital forensics and incident response (DFIR) as a unified field in cybersecurity that can assist in threat hunting as well as remediation and forensic analysis.
Tactics and techniques for post-mortem investigation
The great majority of minor incidents do not require a post-mortem investigation. However, in those incidents that do typically involve a specialized team that may leverage a variety of tools, including SIEM and log correlation tools. Leveraging resources such as the MITRE ATT&CK Framework can help the forensic team set a work agenda that focuses on the incident timeline, what parts of the enterprise have been affected, and ownership. High-impact or unique incidents may require a specialized team to undertake the root cause investigation, which may also involve specialized tools and examination of logs in SIEM, EDR, or XDR.
Incident response challenges
Incident response can be a complex and challenging process. One of the biggest headaches faced by incident response teams is the lack of evidence and relevant data to validate and investigate alerts. Security Operations Centers often reckon with bottlenecks when triaging noisy alerts that require more context, which can easily lead to their wasting precious time chasing false positives or leaving them with open-ended investigations. We can source much of the problem to poor-quality alerts. In many cases, a unique identifier (UID) may generate multiple alerts in multiple tools or logs, leading to inefficient, time-intensive, manual correlation responses.
Additional challenges that can crop up during the incident response process include the complexity of IT environments, a lack of skilled resources, increasing sophistication of threats, and advancing regulatory and legal requirements. The high cost of storing endpoint and network telemetry can also leave SOCs without sufficient context for qualifying incidents and establishing a “normal” baseline, against which they can evaluate alerts and more quickly identify genuine threats.
3 steps to accelerate incident response
In today's rapidly evolving cybersecurity landscape, speed and accuracy of response are critical to mitigating cyber risk. Organizations need to implement effective measures to accelerate their response time to minimize damages caused by cyberattacks. Such measures include the following:
- Upgrading to a comprehensive Network Detection & Response (NDR) and EDR solutions – A standalone IDS or next generation firewall (NGFW) primarily detects intrusions at network perimeters based on predefined rules and signatures. This means that they do not provide visibility into all points of entry into the network, leading to network blind spots. However, with the combination of EDR and a comprehensive NDR solution, incident response teams can get full visibility into all entry points, from perimeter traffic, to data center traffic, to cloud traffic, thus eliminating network blind spots and accelerating incident response by preventing dead end investigations due to a lack of evidence. In terms of incident response, an EDR + NDR deployment creates synergies that can make the process more streamlined and authoritative.
- Ensure incident responders have full context for every alert – To perform effective incident response tasks and threat-hunting missions, the security team must have the context they need to answer the who/what/where/when investigative questions quickly and confidently. A comprehensive NDR solution can provide this context by collecting and generating network evidence, such as protocol logs, extracted files and PCAP, and pre-correlating it to security alerts so analysts have fast and ready access to context.
- Consolidating tools, data and alerts in a SIEM/EDR/XDR environment - Even if security analysts have the full context, response times can be negatively impacted if the contextual data and alerts are scattered across disparate systems and UIs. Organizations should work to consolidate point solutions and strive to consolidate the evidence and alerts generated by their tools in a single data lake, such as those provided by a SIEM or XDR platform. The combination of EDR, NDR, and XDR or SIEM — commonly referred to as the SOC Visibility Triad — can take incident response to an even higher level by delivering blocking and logging capacity while creating a consolidated environment in which responders can get fast answers to their questions.
Corelight’s Open NDR Platform accelerates response
Time is everything in incident response. Incident response teams must be able to quickly determine which incidents are dangerous, which are not, and which actually happened, so they can quickly address the most severe threats before the scope of damage expands.
Using a comprehensive Network Detection & Response (NDR) solution that combines high-performance signature-based alerts with network context, such as Corelight’s Open NDR Platform, can help speed up incident response processes. Corelight's Open NDR Platform fuses machine learning, behavioral analytics and signature-based IDS alerts from Suricata with Zeek® network evidence. This correlated package of alert and evidence is then delivered to your SIEM, XDR, or Investigator—Corelight’s SaaS analytics solution. Learn how Open NDR integrates high-performance signature-based alerts with network context—lowering response times and revealing attack impact.
Book a demo
We’re proud to protect some of the most sensitive, mission-critical enterprises and government agencies in the world. Learn how Corelight’s Open NDR Platform can help your organization tackle cybersecurity risk.












