Corelight ECS mapping: Unified Zeek data for more efficient analytics
I’m pleased to announce that Corelight sensors now support the Elastic Common Schema (ECS) via our Corelight ECS Mapping.
At Corelight, we’re always striving to make the life of threat hunters and security analysts a little easier. It’s the reason we developed our Open NDR Platform that provides comprehensive, correlated network data and forensic evidence about everything happening on the network. If you’re familiar with Corelight, you probably already know that.
What you might not know, however, is that we published a Threat Hunting Guide a couple of years ago that offers a variety of helpful tips aligned with the MITRE ATT&CK framework, a knowledge base of adversary tactics and techniques based on real-world observations.1 Our aim with that guide was to provide a useful resource for security teams to elevate their detection capabilities and improve their threat hunting programs.
Well, we recently updated the guide with a variety of special tips and queries that we developed with our strategic partner CrowdStrike for Falcon LogScale, Falcon Insight XDR, and Falcon Complete customers. This post kicks off a new series highlighting some of those tips on how you can hunt for some of the more popular and dangerous ATT&CK tactics that we cover more thoroughly in the guide.
If you’re familiar with the ATT&CK framework, you know that “Initial Access” is one of the most important pillars within the framework since this is where adversaries try to establish an initial foothold to burrow deeper into the victim’s network. The various techniques can be quite simple yet very effective and often appear as routine processes and harmless files or weblinks to the untrained eye. But to the keen threat hunter, they are the digital fingerprints of an intruder, the telling signs of an attacker seeping into the environment.
One commonly used technique is “Drive-By Compromise.” This is where a target is tricked into downloading a harmful file from a compromised website controlled by the adversary. An easy way to detect this is to monitor all employee downloads from external websites with an eye toward suspicious files. To do this, an analyst could simply inspect the Corelight ‘http log’ within the LogScale dashboard for downloads of executable files or file extension and mime-type mismatches that might look questionable.
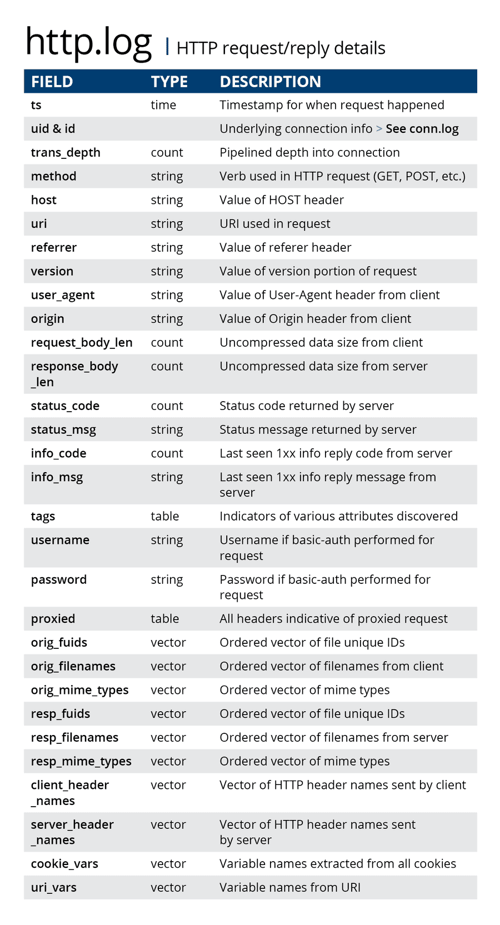
The http log can be used to find suspicious executable files that have been downloaded from external websites and file extension and mime-type mismatches that might look suspicious.
'External Remote Services' is another common technique cybercriminals use to establish initial access on a target system. With this method, an adversary uses your company’s own remote services capabilities secretly against you to establish a connection from an external system that they control. To detect these instances, you’ll want to start by compiling a list of all the remote services you currently have in operation. Once these are identified, you can shift your focus to the Corelight ‘conn log’ entries in Falcon LogScale or Falcon Insight XDR to spot the services and servers accepting connections from outside the organization. Then you can review them to determine whether they are legitimate connections.
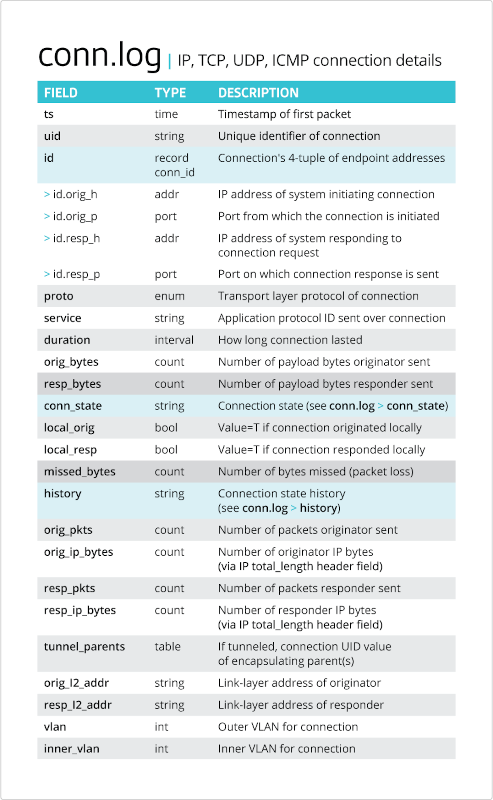
The conn.log provides foundational data about every connection on your network—the who, what, when, and where of your packets.
Keep in mind that there are also remote services that function in reverse, reaching out from inside your network to external servers. So it’s important to also monitor the conn log for outbound connections.
Another common Initial Access technique is ”Spear-phishing Attachments,” where adversaries send malicious attachments to specific individuals or groups in what appear to be harmless email messages that, once clicked, infect the user’s system. By keeping a close eye on the Corelight ‘smtp log’ for suspicious attachments, a threat hunter can easily detect potential spear-phishing attempts and take action to stymie the effort.
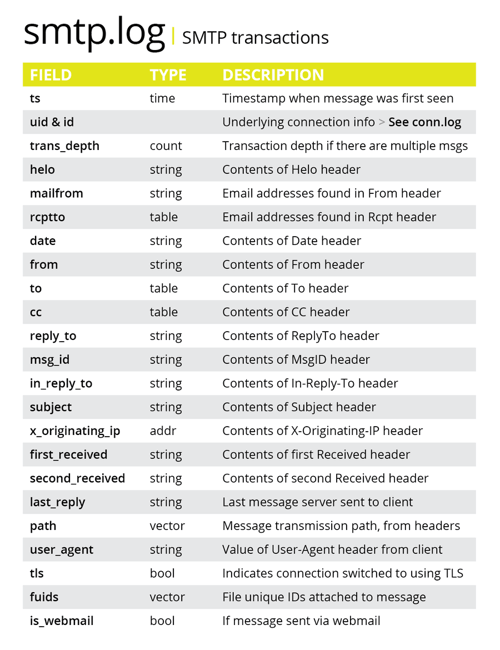
The smtp log can be used to detect potential spear-phishing attempts.
“Spear-phishing Links” is another common technique, but instead of sending malicious file attachments in bogus emails, adversaries simply include a carefully disguised link within the email to deliver their payload. If you’ve even been “rickrolled,” you know what I’m talking about. You can see telltale signs of these threats by carefully inspecting the Corelight ‘smtp_links’ logs and identifying links that you suspect might be leading to harmful destinations.
Initial Access is only one of the fourteen tactics MITRE defines in the ATT&CK framework. The new Corelight for CrowdStrike Threat Hunting Guide gets much more granular on these and other tactics cybercriminals use to access your systems and steal your data. You can read more about these other tactics in our upcoming blog posts in the series.
Until then, stay vigilant and trust your instincts. When you see any sign of activity that just doesn’t seem right, follow the clues because even if you don’t find a bad actor crawling around in your environment, every threat hunt reveals something important. It might reveal clues of suspicious behavior or misconfigured systems that can lead to a compromise if left undetected. And be sure to download Corelight's new Threat Hunting Guide for CrowdStrike Falcon LogScale users for tips on a more complete view of tactics and techniques outlined by MITRE.
I’m pleased to announce that Corelight sensors now support the Elastic Common Schema (ECS) via our Corelight ECS Mapping.
Learn how to use Corelight’s rich network telemetry in CrowdStrike’s Next-Gen SIEM to expose defense evasion and lateral movement inside your network.
Learn about the benefits of Corelight DNS logs, and how Splunk Enterprise Security can reach a new level of functionality through integration with...