Corelight’s recent contributions to open-source Bro
I want to take the opportunity here to talk about a few of our more recent contributions to open-source Zeek (formerly Bro).
It’s hard to beat a mission like transforming government for the 21st Century. That’s what I’ve been doing for more or less my entire professional life. From building information systems in New Orleans both before and after Hurricane Katrina in 2005 to my latest role as Chief Data Officer of San Francisco, my professional life has been dedicated to public service.
So why the private sector? Why now? Why Corelight?
I first met Greg Bell during a meeting in 2011 when he was a division director at Lawrence Berkeley National Laboratory (Berkeley Lab). At that meeting, he turned an aimless discussion into a structured troubleshooting session. I gravitated towards him as a mentor.
Once he became CEO of Corelight, I started to watch closely because I knew that this company had three fundamental ingredients for success that made it worth joining:
Also in 2011, I first heard about open source Bro, the technology that Corelight is built on, when I had to describe how it worked as part of a job interview at Berkeley Lab. My immediate thoughts were a) awesome interview technique b) this technology sounds magical and c) why hasn’t someone built a company on top of it?
I spent the next few years working closely with the cyber team at Berkeley Lab and in that time I learned how real cybersecurity works. I discovered that it is something that extended far beyond compliance, checklists and appliance management and into a living system of dynamic response, continuous evolution, and learned resilience.
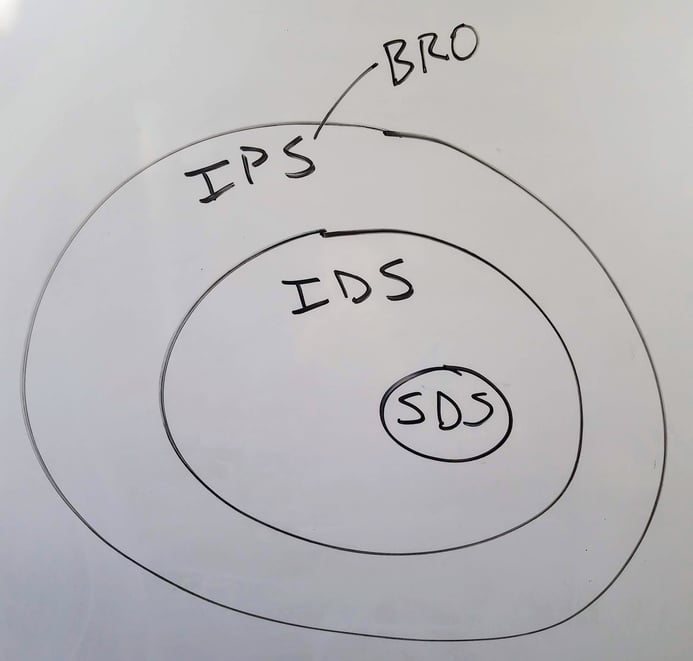
Bro empowered all of this. Whenever I try to describe Bro, I draw the following diagram. Bro extends well beyond signature based detection (SDS) to behavioral based detection and then to a proactive response. Bro is adaptive and scalable.
Cyber threats are a daily news item. Bro, deployed at scale and with the reliability and ease of Corelight’s solution, is uniquely positioned to help our institutions solve the ever mutable threat of cybersecurity so prevalent in our world today. It’s a mission with a global scale.
Peter Drucker is quoted with saying “culture eats strategy for lunch.” When interviewing at Corelight, it was like a case study in how NOT to be a stereotypical “Silicon Valley” startup (You may have seen the popular HBO show…this isn’t that).
Yes, the Corelight team is insanely smart with world-class engineers and one of the founders is Vern Paxson, the inventor of Bro. But that’s not the whole story. The ethos of Corelight is meaningful collaboration and low ego. This philosophy is set at the top and reinforced throughout the team. Everyone jumps in and helps. Below are just two emblematic images from my first week at the job.


When Greg asked me to help ensure this culture stuck at scale, I could hardly resist. Culture and organizational health are key differentiators in our modern world, where talent is both discerning and mobile.
Corelight’s tagline is “illuminate your network.” Merriam-Webster’s dictionary defines “illuminate” as ‘to supply or brighten with light, to make luminous or shining.’ Fundamentally, Corelight is about offering a set of tools that empower cybersecurity professionals to do their jobs more effectively and efficiently.
So much of cybersecurity marketing and branding is dominated by fear-mongering: “Do this or you will be in TROUBLE. Bad things are lurking EVERYWHERE. You CAN’T FIX this alone – you need us and we will solve this for you.” In contrast, Corelight is about acknowledging the challenge and empowering you to solve it.
Corelight does this by providing our customers with elegant, beautifully structured, comprehensive data for analysis and response (and much more soon). We don’t conceal the data to create a dependence on Corelight for insights. Instead, we expose it to the professionals who need it – reflecting our open source heritage in the very nature of our product.
The above ingredients added up to a recipe that I could not refuse. I am thrilled to be joining the Corelight team – a team with the talent and skills to continue to build a technology that will empower enterprises around the world. So if you want an amazing, challenging mission PLUS a healthy and empowering culture, join us! We’re always hiring!
I want to take the opportunity here to talk about a few of our more recent contributions to open-source Zeek (formerly Bro).
I’m kicking off this series with an update about the company, but future posts will be a lot more technical.
I am excited to announce Corelight’s v21 release, which delivers dozens of powerful C2 detections, extends analyst visibility around RDP connections,...