Streamlining security investigations with real-time enrichment of Corelight Open NDR and SentinelOne Singularity
Corelight’s integration with SentinelOne is a game-changer for security teams looking to stay ahead of evolving cyber threats.
Through our newly announced partnership with CrowdStrike, Corelight customers will be able to incorporate CrowdStrike’s best-in-class threat intelligence into Corelight Sensors to generate actionable alerts and network evidence. In addition, by connecting Corelight to Humio (a CrowdStrike company), security operations teams can respond to incidents more quickly and run more streamlined investigations. Pairing Corelight and CrowdStrike enables incident responders to quickly triage alerts, rapidly pivot to the most relevant evidence, and drive down the mean time to resolution for incidents.
Today’s endpoint detection and response (EDR) solutions have helped narrow the focus for security operations center (SOC) teams, pointing out high-fidelity detections and incidents in customer environments. At the same time, there has been an expansion of the attack surface, fueled by an increase in remote work, cloud adoption, and software-as-a-service (SaaS), and that has transformed the modern enterprise landscape into one with many potential blind spots beyond the reach of the endpoint.
Many customers may instinctively turn to their security incident and event management (SIEM) systems. But why start there at all, when you can immediately correlate your endpoint detection against network evidence using Corelight’s open NDR platform?
Utilizing the de facto network monitoring standards of Zeek® and Suricata as the building blocks, Corelight can examine and correlate events with proprietary insights into network traffic, assessing and finding evidence of many TTPs described in the MITRE ATT&CK framework – directly from network traffic at the source. Our Open NDR solution does this enrichment and correlation work at the point of observation (within the network), taking the guesswork out of trying to work your way backwards into data that has been boiled down to a standardized log format that you are viewing post-detection, and much later in a SIEM.
The combination of Corelight’s Open NDR solutions enriched by CrowdStrike’s threat intelligence, plus the power of the Humio platform, is a strong foundation for enterprise customers to improve their defensive security infrastructure. Monitoring network traffic using Zeek and Suricata should be a fundamental part of any enterprise’s SOC and strategy, and is complementary to an EDR deployment.
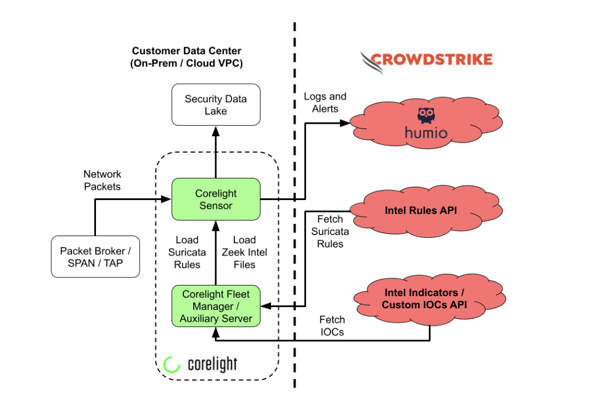
All of this boils down to faster investigation, detection, and response – saving customers time and frustration. To learn more about Corelight and Crowdstrike, check out our joint solution brief, on-demand webinar and executive town hall. For more information about Corelight, visit https://corelight.com/products/.
Corelight’s integration with SentinelOne is a game-changer for security teams looking to stay ahead of evolving cyber threats.
Reduce time to triage by up to 50% with Corelight's new Guided Triage capability.
Streamline alert triage and reduce alert fatigue with Corelight's Microsoft Defender integration, enabling faster, smarter decisions across your SOC.