Translating query into action
Sigma is an open-source project that provides a generic signature format for SIEMs. Here are the benefits of Sigma, and how to get these threat...
The Corelight Labs team prides itself on the ability to create novel Zeek and Suricata detection content that delves deep into packet streams by leveraging the full power of these tools. However this level of additional sophistication is not always required: sometimes there are straightforward approaches that only require queries over standard Zeek logs. It’s always valuable when developing detections to keep in mind that “sometimes simple does just fine.”
In recent times we’ve seen several instances that exemplify this concept. In this blog we show how following an evidence based detection strategy can enable high quality detections in near real time and, possibly even more importantly, for retrospective investigations. We show this by using only logs produced by standard out-of-the-box Zeek.
We’ll look at three APT toolsets that have been linked to five threat actors, detecting each using relatively simple search logic.
|
Threat Actor |
Tool |
Writeup |
| Iranian APT35/ Charming Kitten |
HYPERSCRAPE |
Google TAG blog |
| TA423/Red Ladon |
SCANBOX |
Proofpoint / PWC blog |
| UNC2447 Lapsus$ Yanluowang ransomware group |
KOLOBKO |
Talos blog on Cisco’s cyber attack. |
Google’s TAG team published an excellent analysis of a post-compromise data extraction tool that harvests data from Gmail, Microsoft and Yahoo! accounts. They reported that the tool has been used by Iranian government-backed groups APT35 AKA “Charming Kitten” since December 2021. We will describe three detection strategies - highlighting key components in red - and then provide a SIEM search that encompasses all three.
When launched, HYPERSCRAPE communicates with its C2 with the following GET request (the {C2} component below is a placeholder/variable):
|
GET http://{C2}/Index.php?Ck=OK HTTP/1.1 Host: {C2} Accept-Encoding: gzip Connection: Keep-Alive |
If the C2 responds with “OK” the tool continues to Stage 2, otherwise it terminates. This allows the attacker to remotely disable implants on startup, perhaps based on the IP address of the victim.
If the implant receives an “OK” from the C2 during stage 1, it displays a form which allows the attacker to select an email provider to target, and other options including an identity for the victim.
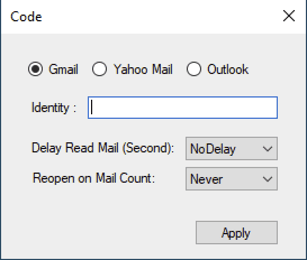
Image of implant form: provided by Google TAG
The identity field is then sent to the C2 in a GET request, and is represented for the purpose of this blog as {identity} below:.
|
GET http://{C2}/Index.php?vubc={identity} HTTP/1.1 Host: {C2} Accept-Encoding: gzip |
Once again, the implant expects a response of “OK” from the C2, and will then proceed to Stage 3.
After finding and extracting emails, the implant places them in the local Downloads directory, and sends a status message back to the C2 via a POST which contains metadata related to the extraction (REDACTED as appropriate).
|
POST http://{C2}/?Key={GUID}&Crc={Identifier} { "appName": "Gmail Downloader", "targetname": "{Email}", "HostName": "REDACTED", "srcUserIP": "REDACTED", "actionType": "First", "timeOccurrence": "REDACTED", "OS": "REDACTED", "OSVersion": "REDACTED", "SystemModel": "REDACTED", "SystemType": "REDACTED", "srcName": "REDACTED", "srcOrgName": "REDACTED" } |
Note that while outside the scope of this blog, in addition to the standard Zeek http.log, we can also inspect the content (blue contents) in various ways:
This simple SIEM rule searches the standard Zeek http.log for each of the three elements described above:
|
#path = "*http*" (method=GET (uri="*.php?Ck=OK*" OR uri="*.php?vubc=*")) OR (method=POST uri="*/?Key=*&Crc=*") |
In a joint research piece, PWC and Proofpoint released an excellent analysis on a malware campaign that was assessed with moderate confidence to be conducted by China-based espionage-motivated APT group “APT TA423” AKA “Red Ladon”. The campaign was said to target local and federal Australian government agencies, Australian media organizations, and heavy industry manufacturers that maintain wind turbines in the South China Sea.
The campaign began with phishing emails that included links to a website which impersonated Australian media entities “australianmorningnews[dot]com”. The intent of the phish was to entice victims to visit the site, where they would be infected with SCANBOX malware. We encourage you to read the blog by PWC and Proofpoint which describes the campaign in great detail.
One of the first questions that a concerned organization may ask is “who clicked on the link to the phishing site?” Luckily it’s one of the easiest to answer, as Zeek’s HTTP logs can simply be searched for “australianmorningnews”.
|
#path = "*http*" host= /australianmorningnews/ |
After having asked “who clicked on the links?” a follow-on question would be “who was infected?” As shown in the PWC/Proofpoint analysis, several communications occur between the implant and the C2 over HTTP, as summarized in the following table:
|
URI path |
Functionality |
|
/i/v.php?m=b |
Sends victim information to C2 |
|
/i/c.php?data= |
Loads a specified child JavaScript object |
|
/i/k.php?data= |
Creates/replaces an iframe |
|
/i/p.php?data= |
Executes a ScanBox plugin |
|
/i/v.php?m=a&data= |
Heartbeat to the C2 server |
|
/i/v.php?m=p&data= |
Sends plugin information |
|
/i/v.php?m=plug |
URL that plugins send captured data to |
To detect this activity, once again we can search Zeek’s standard HTTP logs. We can do this on a per-URI basis, or a regex search which encompasses all of the patterns, as the example below shows. Note that the regex incorporates what is likely a campaign marker in the URI (i.e., the /i/ leading the URIs above) so that if this changes to another alphabetic character, the regex will still work.
|
#path = "*http*" uri = /\/[a-z]\/[vckp]\.php\?[md]/ (uri = /data=/ OR uri = /=plug/ OR uri = /=b/) |
The following SIEM rule uses the standard Zeek http.log, which encompasses the phishing and post-infection stages as described above:
|
#path = "*http*" ( host= /australianmorningnews/ OR (uri = /\/[a-z]\/[vckp]\.php\?[md]/ (uri = /data=/ OR uri = /=plug/ OR uri = /=b/)) ) |
In August, Cisco Systems disclosed a cyber attack that targeted its corporate IT infrastructure systems. In a further technical blog Talos (Cisco’s threat intelligence arm) made the following assessment on attribution:
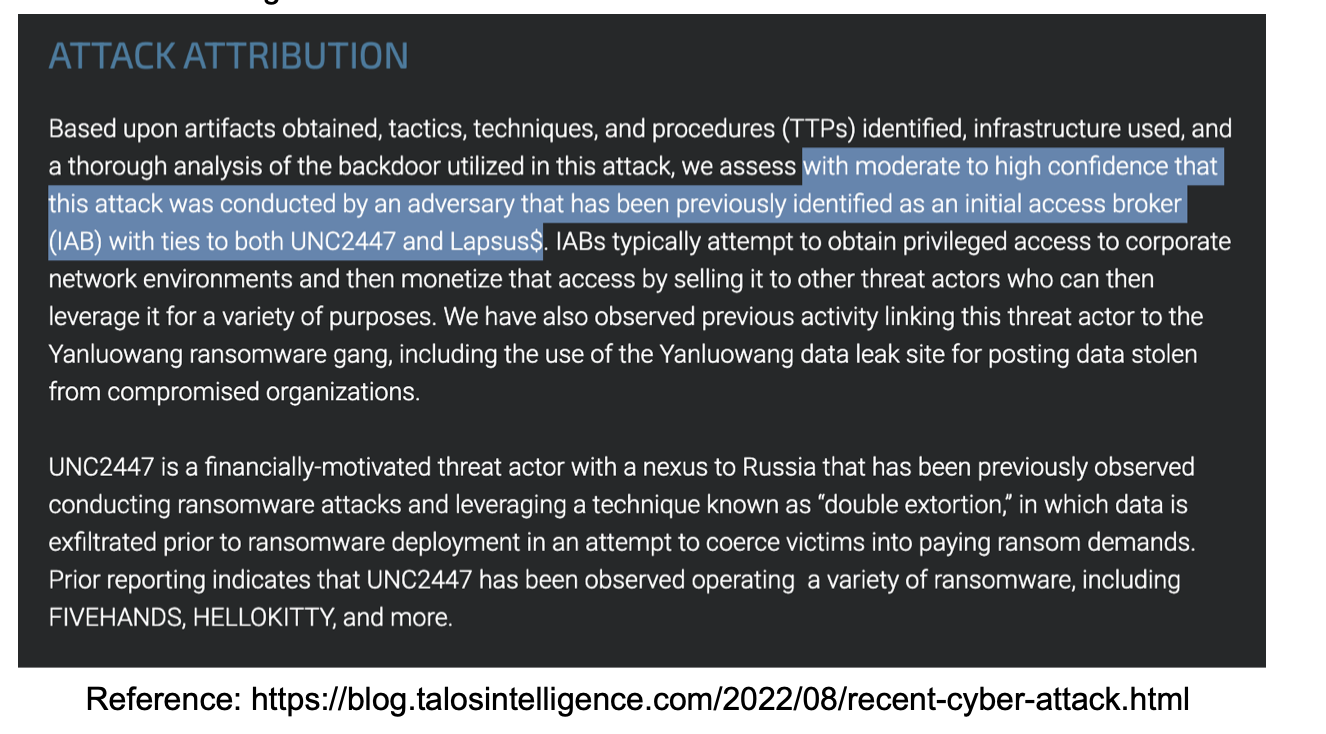 Talos then shared a detailed analysis of the threat actor’s activities, which are described as “consistent with pre-ransomware activity, commonly observed leading up to the deployment of ransomware in victim environments.” Talos also shared some network indicators that can be used to detect the backdoor tool known as Win.Backdoor.Kolobko-9950676-0.
Talos then shared a detailed analysis of the threat actor’s activities, which are described as “consistent with pre-ransomware activity, commonly observed leading up to the deployment of ransomware in victim environments.” Talos also shared some network indicators that can be used to detect the backdoor tool known as Win.Backdoor.Kolobko-9950676-0.
Commands retrieved from the C2 use HTTP GET requests in the following formats:
/bot/cmd.php?botid=%.8x
/bot/gate.php?botid=%.8x
We can simply search Zeek’s standard http logs for evidence of this activity with this SIEM search:
|
#path = "*http*" (uri="*.php?botid=*") |
Following the initial infection, Talos reported additional requests were made every 10 seconds with this user agent:
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.51 Safari/537.36 Edg/99.0.1150.36 Trailer/95.3.1132.33
We’ve confirmed from our Polaris data that the Trailer/ component is relatively rare in operational traffic, and the 95.3.1132.33 version component even rarer - in fact we did not find a single instance of that version. To further guard against false positives, we can also tighten the search up with a URI constraint of php.
|
#path = "*http*" user_agent="*Trailer/95.3.1132.33*" uri="*.php?*" |
Timing-based detection of beacons falls outside the scope of this blog, but as a secondary detection element, if this activity is seen to occur every 10 seconds - or any reasonably consistent periodicity - then this would be a further indicator.
Combining these three simple searches together in a single rule, we have:
|
#path = "*http*" ( uri="*gate.php?botid=*" OR uri="*cmd.php?botid=*" OR user_agent="*Trailer/95.3.1132.33*" ) |
We’ve shown that detecting modern network attacks can sometimes be as simple as looking for patterns within logs already provided in standard Zeek output. These examples show that even in its simplest form, an evidence-based security strategy allows for both ongoing detection, and retrospective/forensic analysis. This latter is particularly important: very often when analyzing activity that occurred in the past, prior to us knowing what to look for, the only available avenue is to mine previously gathered evidence along the lines of what we’ve sketched here.
By Corelight Labs Team
Sigma is an open-source project that provides a generic signature format for SIEMs. Here are the benefits of Sigma, and how to get these threat...
Corelight recently teamed up with SOC Prime, creators of advanced cyber analytics platforms, to add support for the entire Zeek data set into Sigma.
Corelight's data aggregation reduces SIEM ingest by 50-80% compared to legacy network security monitoring tools.