Investigating the effects of TLS 1.3 on Corelight logs, part 3
We reproduce our experiment using TLS 1.3. Remember that we have been visiting the Web site enabled.tls13.com, first without encryption, then with...
Editor’s note: This post is the result of the author’s work at the International Computer Science Institute where she works as a senior researcher.
In the last months, the major web browsers (Safari, Firefox, Edge, Chrome) announced their intent to disable support for TLS 1.0 and TLS 1.1 in the first quarter of 2020. What exactly does this mean, and what are the consequences of this change? Let us take a short step back and take a look at the history of TLS a bit.
Historic Notes
Today TLS is omnipresent on the Internet – it is used to encrypt web traffic, email traffic, chat messages, etc.
Netscape developed the original SSL protocols, which are the predecessor of TLS. SSL 1.0 was never publicly released. SSL 2.0 was released in 1995. It had a number of flaws and was quickly superseded by a completely redesigned SSL 3.0 in 1996. TLS 1.0 was the first version of the protocol that was standardized through the IETF standards process and released in 1999. It was an evolutionary step from SSL 3.0, with a smaller set of changes. The same is true for TLS 1.1 (2006) and TLS 1.2 (2008), which make the protocol more robust against different attacks. The recently released TLS 1.3 (2018) is a larger change from earlier protocol versions and redesigns many parts of the protocol.
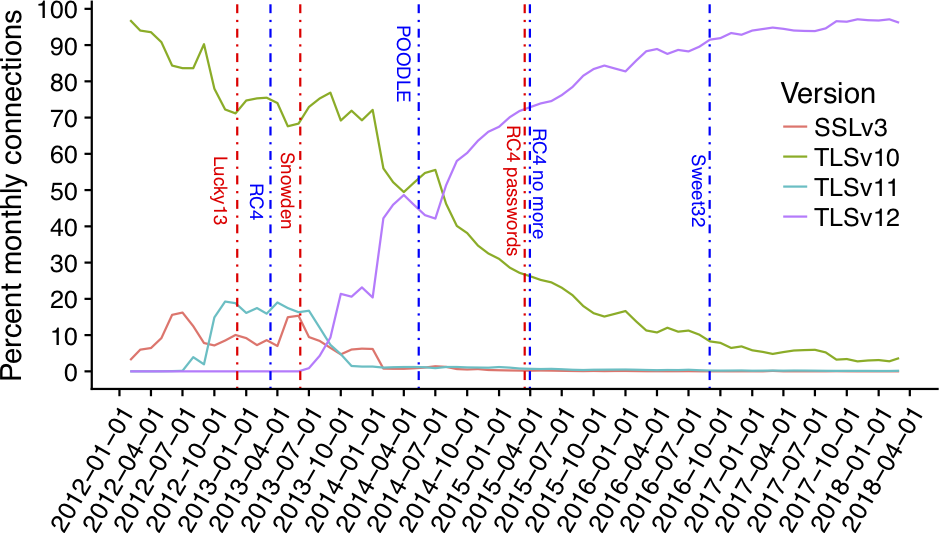
In 2012, we started the ICSI SSL Notary (web page, design document), an effort to monitor how SSL and TLS are being used in practice. When our project started in 2012, the majority of TLS connections were still using TLS 1.0 – even though TLS 1.2 has been standardized 5 years before. Back then encryption was often less of a priority and not as ubiquitous; older versions also were still seen as adequately secure. It wasn’t until mid 2014 that TLS 1.2 was used more than TLS 1.0. During this time a number of security issues were found in older protocol versions and ciphersuites. Our paper “Coming of Age: A Longitudinal Study of TLS Deployment,”* which was published at the Internet Measurement Conference (IMC) 2019 shows the timeline of security issues and following protocol changes in depth. The following plot (Figure 1 below) from the paper shows the SSL/TLS versions we saw being used in the traffic we analyzed from 2012 to 2018; vertical lines show attacks.
Consequences of Disabling TLS 1.0 and 1.1
The plot indicates that TLS 1.1 never found much adoption; we saw significant use for a short period of time in 2012/2013, and only negligible use since then. One probable reason is that this is caused by a lot of software moving directly from supporting only TLS 1.0 to supporting TLS up to 1.2, skipping the phase where only 1.1 was supported. The widely used OpenSSL library is an example of it; it added TLS 1.1 and 1.2 support in version 1.0.1 (March 2012).
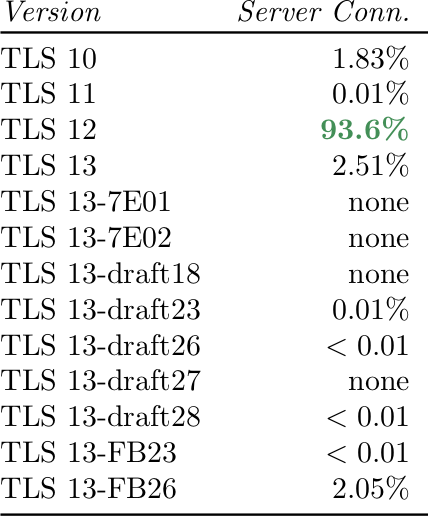
Our data also shows that today the vast majority of connections are using TLS 1.2. In a 2019 paper, we show that in April of this year only ~1.84% of all connections were using TLS 1.0 or 1.1; the remaining ~98.17 of connections use TLS 1.2 or 1.3. (link to paper, also note the table in Figure 1 below from the paper showing the TLS versions in established connections in April 2019.)
I expect that the majority of users will see no impact when TLS 1.0 and 1.1 are disabled. While there still are a number of sites on the Internet that do not support TLS 1.0/1.1 – these are typically small pages with low number of visitors. Furthermore, most of these pages should be able to support TLS 1.2 with only a small configuration change.
The situation gets a bit more complicated when looking at hardware devices. Some devices – like printers, server configuration interfaces, internet routers, etc. – might not support TLS 1.2 and it might be impossible to update them now. Since these devices are typically not reachable from the Internet, it is hard to guess how many users might be impacted.
I assume that browsers disabling TLS 1.0/1.1 will not impact the majority of users – just like when SSL 3.0 was disabled by browsers in 2014 (Firefox: https://blog.mozilla.org/security/2014/10/14/the-poodle-attack-and-the-end-of-ssl-3-0/, others: https://disablessl3.com/safari.html). For impacted users, it will probably remain possible to re-enable old versions of TLS through configuration options for some years.
Dropping support for TLS 1.0 and 1.1 will make the Internet a safer place – TLS 1.2 is strictly better, and dropping support for older versions of TLS that are mostly unused removes the danger of downgrade attacks (attacks that trick clients/servers to use an older version of TLS that can be exploited).
*This paper was awarded the Distinguished Paper Award by the Internet Measurement Conference (IMC) in 2019.
We reproduce our experiment using TLS 1.3. Remember that we have been visiting the Web site enabled.tls13.com, first without encryption, then with...
In part 1, I showed how Corelight would produce logs for a clear-text HTTP session. In part 2, I perform the same transaction using TLS 1.2.
In this first of three parts, I will introduce TLS and demonstrate a clear-text HTTP session as interpreted by Corelight logs.