The Art of Team Building: Blueprints from the Black Hat NOC
Here are my learnings from participating in NOCs at Black Hat Asia and Black Hat Las Vegas in 2023.
Corelight Investigator furthers its commitment to delivering next-level analytics through the expansion of its machine learning models. Security teams are now enabled with additional supervised and deep learning models, including:
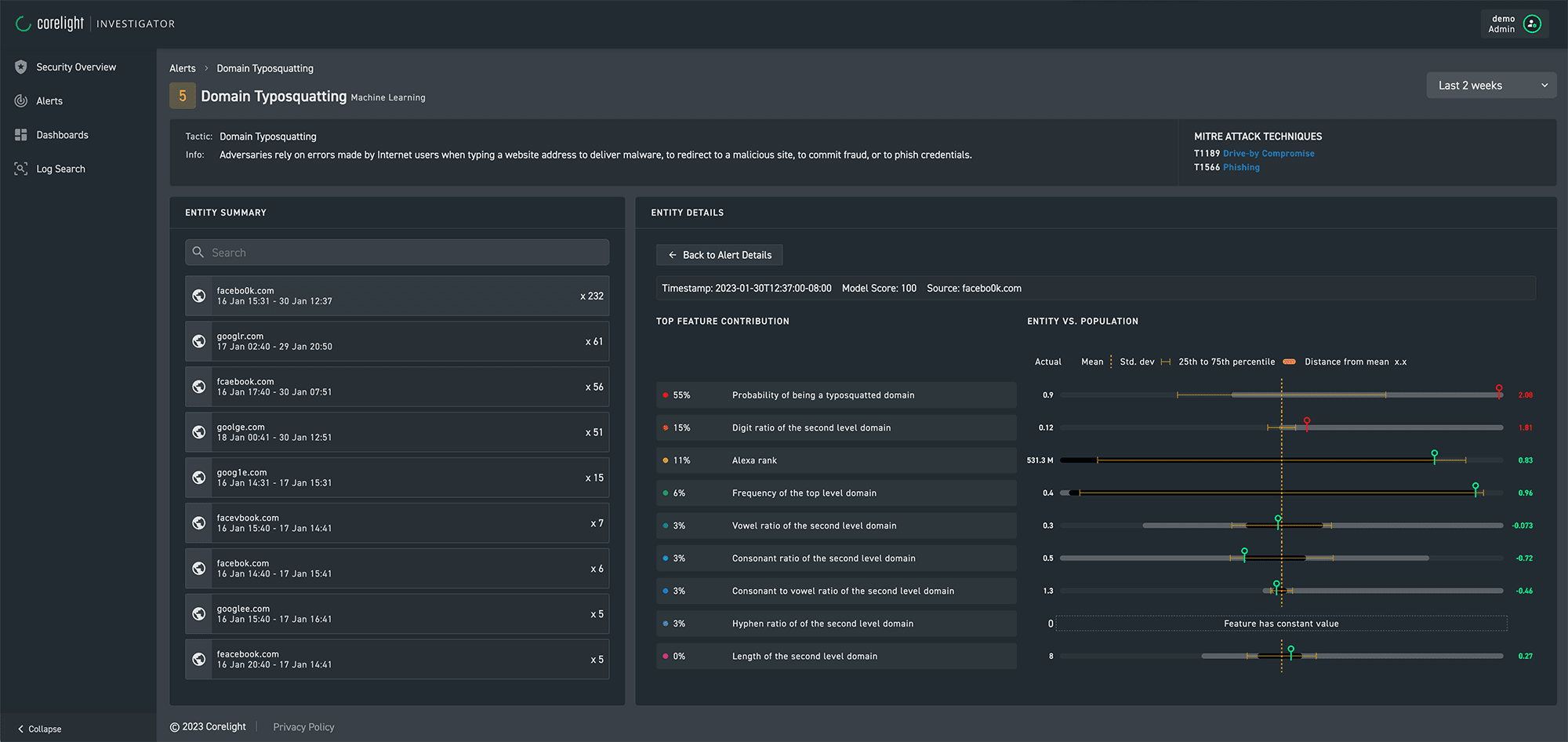
We continue to provide complete transparency behind our evidence -- showing the logic behind our machine learning models and detections, allowing analysts to quickly and easily validate the alerts.
SOC teams taking an evidence-first approach to threat hunting and incident response understand the importance of evidence quality because it determines their analytic outcomes. Corelight has developed a suite of analytics based on three pillars.
Investigator combines machine learning, threat intel, behavioral analysis, continuous community detections from Suricata, Zeek, and Sigma, and new analytics from the Corelight Labs team to deliver the most effective alert aggregation and toolset and dataset consolidation.
Not to be missed, we are happy to announce that we have completed attestation for GDPR – enabling us to extend the power of Investigator to the European market. Corelight customers and prospects can contact sales directly for pricing information or reach out to their preferred Corelight reseller in Europe.
To learn more about our evidence-first approach and how Investigator enables teams to upskill their analysts and improve SOC performance metrics, contact us today to get a demo and learn how to get a trial.
Here are my learnings from participating in NOCs at Black Hat Asia and Black Hat Las Vegas in 2023.
Recapping our learnings from being in the Black Hat NOC at Black Hat USA 2023
Recapping our learnings from the Network Operations Center (NOC) at Black Hat USA 2024. Using historical network logs to detect threats during the...