How to use Corelight and Zeek logs to mitigate RDS/RDP vulnerabilities
CVE-2019-0708 is a serious vulnerability awaiting exploitation. Learn how to use Corelight and Zeek logs to mitigate RDS/RDP vulnerabilities.
CVE-2021-1675, also tracked in CVE-2021-34527, is a remote code execution vulnerability that targets the Windows Print Spooler service. In a nutshell, there is a Distributed Computing Environment / Remote Procedure Call (DCE/RPC) that allows authenticated users to add printer drivers to the spooler service. A malicious DLL instead can be included, which allows a user to take over the machine running the spooler. In the event this machine is also the domain controller, the implications are worse, as the included code will run at a higher level of privilege.
Existing approaches for detection rely on hunting for Windows events or system-level artifacts, but detecting on the network presents unique challenges. The attack relies on adding a printer driver using the DCE/RPC commandsRpcAddPrinterDriver or RpcAddPrinterDriverEx. Unfortunately, there are legitimate uses of this, so relying fully on this command completing successfully as a detection could be error prone. To make matters worse, one POC in the wild wraps the DCE/RPC calls in SMB3 encryption. Compare the first screenshot that clearly shows the relevant RPC call versus the second from the aforementioned POC that only shows encrypted payloads.

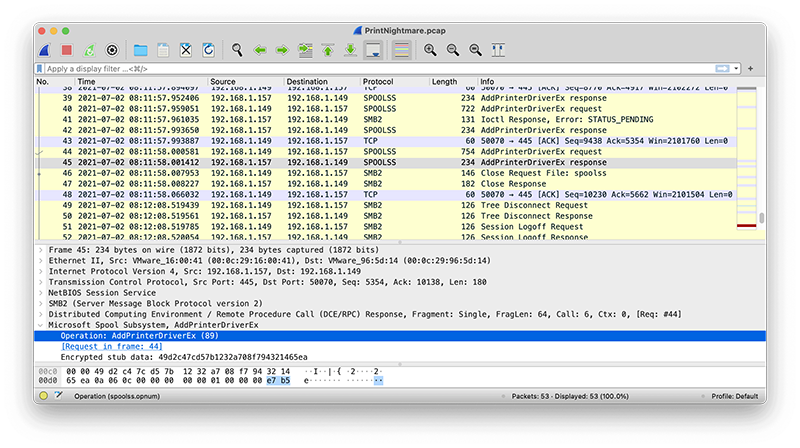

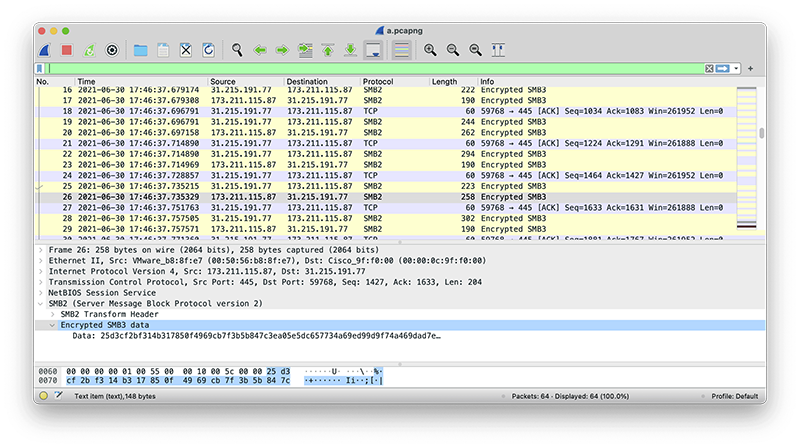
So in order to identify the DCE/RPC commands, one must either somehow intercept and decrypt the payloads or somehow infer the commands from encrypted communications, as we have done with other protocols.
Given the severity of the issue, we are releasing a Zeek package that identifies printer driver additions that occur in the clear over DCE/RPC. While this isn’t guaranteed to only identify this exploit, the command appears to occur rarely on our test networks. Your mileage may vary, however. We hope this helps the NDR community identify potential instances of the exploit and as always, we appreciate any comments or feedback you may have. As of July 6 Microsoft has released additional patches to address this issue, as well as other mitigations if updating a system is not feasible.
CVE-2019-0708 is a serious vulnerability awaiting exploitation. Learn how to use Corelight and Zeek logs to mitigate RDS/RDP vulnerabilities.
Researchers at wiz.io found vulnerabilities in Windows OMI; Corelight has open-sourced a Zeek package for the most severe of these vulnerabilities.
On 1-14-2020, the world learned of the vulnerability CVE-2020-0601. This post is about how leveraging the power of the Zeek community can benefit...