ALL PRODUCTS
See all of the products that power our Open NDR Platform, from our sensors to open-source and proprietary evidence collections to our analytics and SaaS solutions.

OPEN NDR PLATFORM
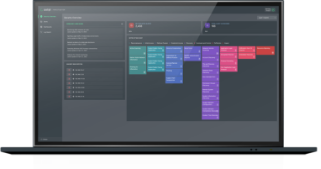
Investigator
The only evidence-first threat investigation platform. Investigator is a SaaS-based network detection and response solution that dramatically simplifies Tier 1 workflows, accelerating triage and resolution.
Zeek
The standard for network traffic monitoring and proactive data-first defense, Zeek® is foundational to the Open NDR Platform.
IDS
The best-in-class open source alerting engine—Suricata IDS—deeply integrated into the Open NDR Platform.
Smart PCAP
Capture just the packets you need for investigations, and store months—not minutes—of traffic history.
Static File Analysis
Detect malware threats with pattern-based detection through YARA rules, the standard in malware analysis.
C2 Collection
50+ detections and insights into known command and control activity, as well as MITRE ATT&CK® C2 techniques for finding novel attacks.
Core Collection
Proprietary packages that help sensors scale in high-throughput environments, combined with curated insights from the Zeek community.
Encrypted Traffic Collection
Dozens of insights into SSL, SSH, and RDP connections enhanced with community contributions like JA3—all without decryption.
Entity Collection
Allows easy searching and grouping on entity inventory, including identification of subnets and 80+ applications.
AP 200 Series Appliance Sensors
Throughput: 2 Gbps | Support for copper and/or optical modules at 100M and 1G
AP 1000 Series Appliance Sensors
Throughput: 25 Gbps | Support for copper and/or optical modules at 1G and/or 10G
AP 3000 Series Appliance Sensors
Throughput: 50 Gbps | Support for copper and/or optical modules at 1G and 10G or 40G
AP 5000 Series Appliance Sensors
Throughput: 100+ Gbps | Support for optical modules at 8 x 10G, 2 x 40G or 2 x 100G
VIRTUAL SENSORS
Corelight's Hyper-V and VMware NDR virtual sensors transform network traffic into high-fidelity data for incident response, intrusion detection, and more.
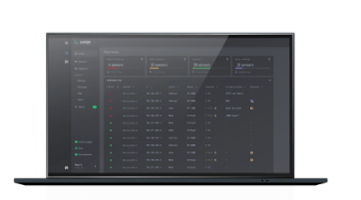
Fleet Manager
Corelight Fleet Manager gives you the ability to manage your entire fleet of sensors from one user-friendly GUI console. Create custom configuration templates in minutes to manage individual sensors, groups, or your entire fleet.