Corelight Sensors detect the ChaChi RAT
Recently Blackberry analyzed a new GoLang Remote Access Trojan (RAT) named “ChaChi.” Here's how Corelight Sensors can detect the ChaChi RAT.
Recently Blackberry analyzed a new GoLang Remote Access Trojan (RAT) named “ChaChi.” This sample was interesting in that it tunnels information over DNS as its preferred command and control (C2) mechanism. We downloaded two PCAPs from the malware samples at the following VirusTotal links:
If you download these PCAPS* and you run them through Wireshark, you will see DNS traffic matching the explanation in the BlackBerry blog:
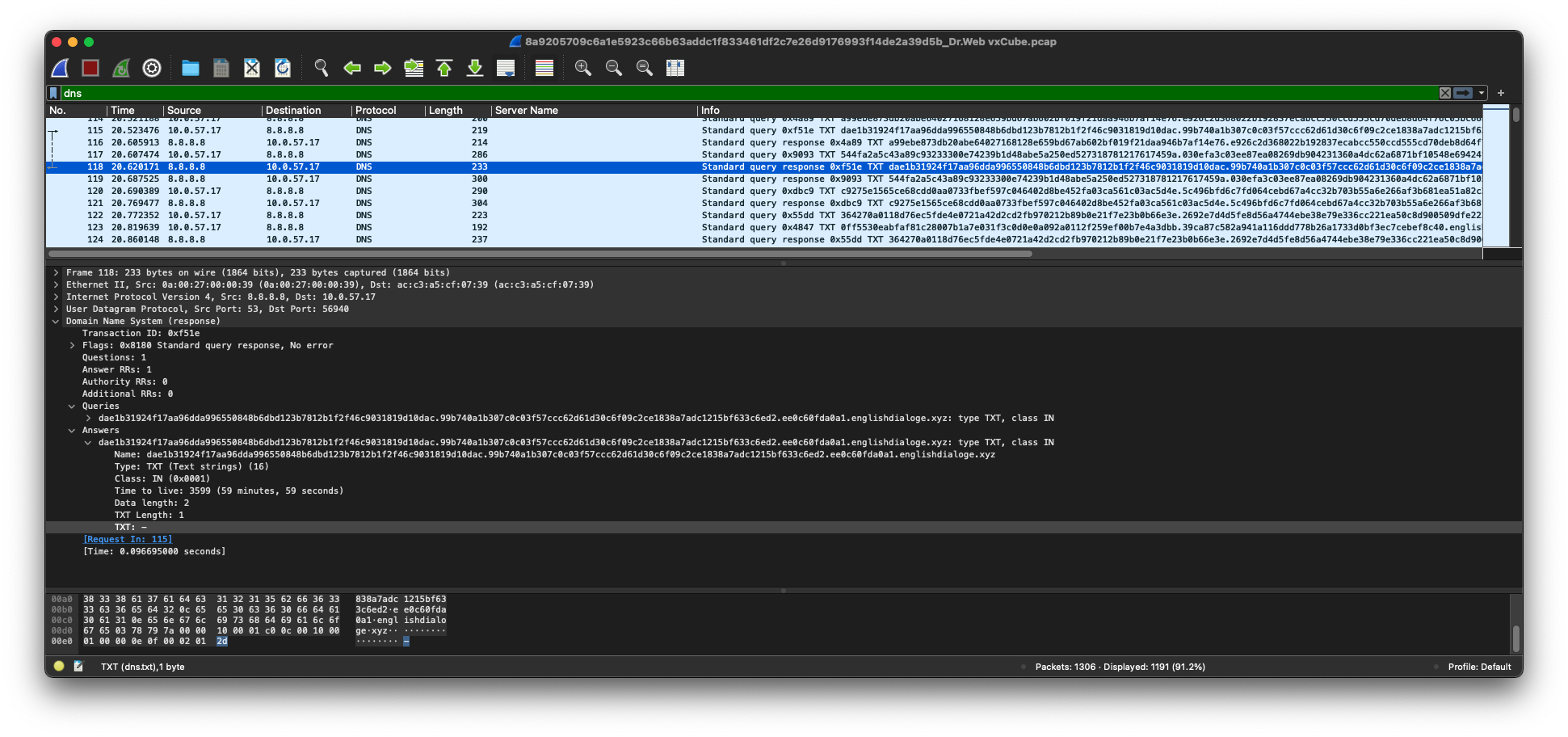
Corelight recently added a generic DNS tunnel detector to our sensors based on an algorithm developed by Vern Paxson and colleagues. This algorithm detects DNS tunnels without using signatures for every DNS tunneling tool available. We ran the ChaChi PCAPs through our generic DNS tunnel detector to see if there were detections:
$ zeek -Cr 8a9205709c6a1e5923c66b63a__Dr.Web\ vxCube.pcap packages
$ cat generic_dns_tunnels.log
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path generic_dns_tunnels
#open 2021-06-23-11-52-02
#fields ts dns_client domain bytes capture_secs
#types time addr string int interval
123.898128 10.0.57.17 englishdialoge.xyz 35378 123.898128
#close 2021-06-23-11-52-02
$ zeek -Cr 0bcbc1faec0c44d157__VirusTotal\ Jujubox.pcap packages
$ cat generic_dns_tunnels.log
#separator \x09
#set_separator ,
#empty_field (empty)
#unset_field -
#path generic_dns_tunnels
#open 2021-06-23-11-52-21
#fields ts dns_client domain bytes capture_secs
#types time addr string int interval
134.204483 10.0.2.15 ntservicepack.com 5273 134.204483
#close 2021-06-23-11-52-21
You see above that as each PCAP was run through our algorithm, the following (dns_client, dns_tunnel_domain) pairs were detected as DNS tunnels:
Corelight’s generic DNS tunneling algorithm detected these pairs without any prior knowledge of the protocol or domains chosen by the malware. The algorithm works by identifying significant information-transfer in DNS query streams. You will notice that the algorithm measured the first tunnel to be approximately 35kb of data and measured the second tunnel at 5kb, signifying the first tunnel sent more data than the second tunnel.
Since the algorithm measures information transfer, it is capable of detecting non-malicious tunnels that occur all the time. For example, we regularly see DNS tunnels on networks we monitor go to “sophosxl.net.” Sophos uses DNS queries and responses to presumably provide anti-virus lookups, which is a type of non-malicious DNS tunnel. Corelight’s generic DNS tunnel detector will detect this non-malicious activity.
This type of activity is so well known that we keep a whitelist of DNS tunneling domains to filter out their activity so you do not have to. As you see above, the domains “englishdialoge.xyz” and “ntservicepack.com” are not filtered out by Corelight’s generic DNS tunnel detector because they are true DNS tunnel detections.
You also may be wondering if the generic algorithm will detect ChaChi when the C2 server does not reply correctly. The generic algorithm expects two-way communication. The following two links provide ChaChi PCAPs you can download:
Upon examining these PCAPs in Wireshark, you will see the ChaChi DNS queries fail with a server failure (a.k.a. SERVFAIL):
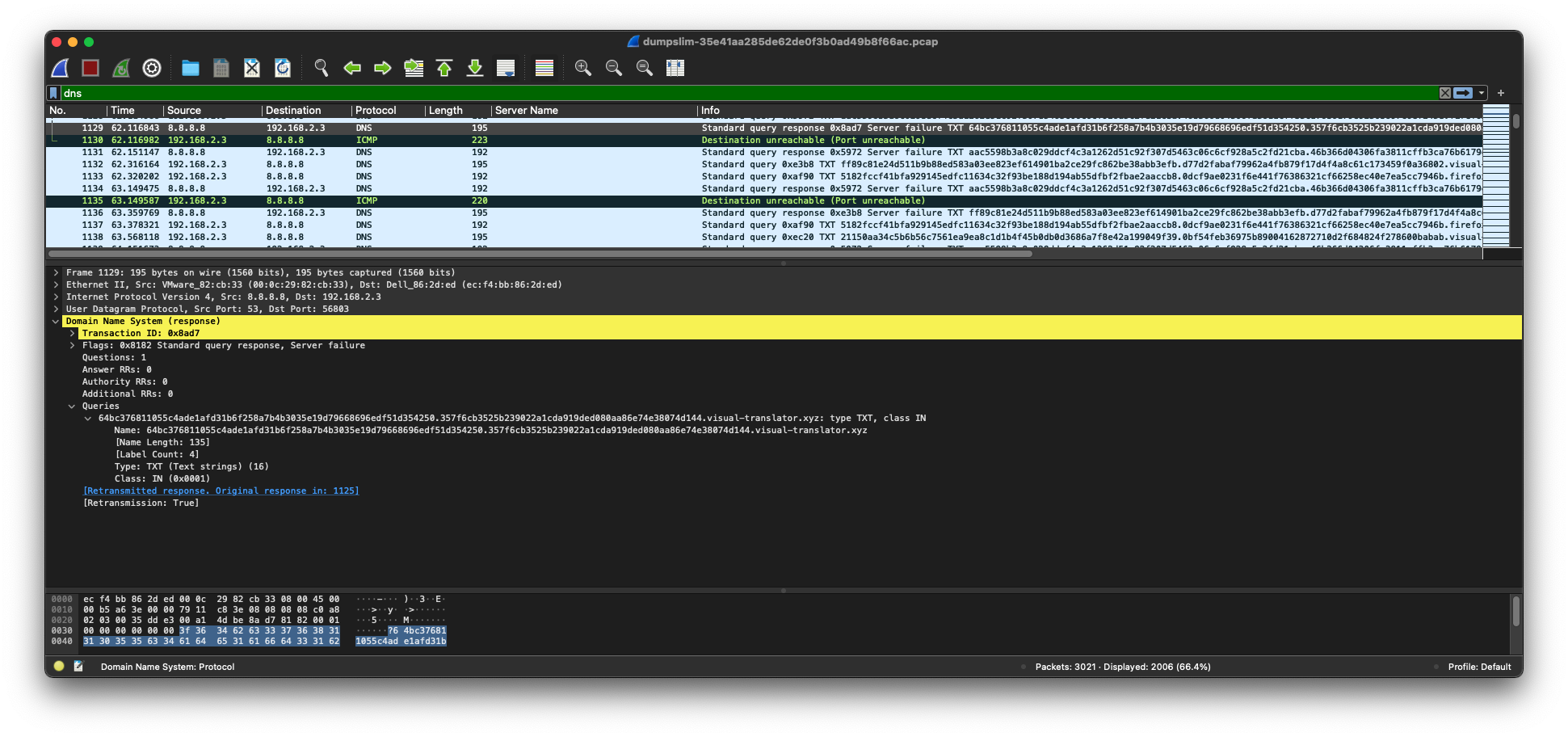
Since the DNS queries were not successful, C2 did not occur and therefore there was no detection by Corelight’s generic dns tunnel detector. When two-way ChaChi C2 communication occurs, as it did in the first two PCAPs from VirusTotal, Corelight’s generic DNS tunneling algorithm will detect it as such.
You can learn more about Corelight’s new C2 collection, launched last month, which identifies C2 tools and techniques that indicate the presence of malicious communication here on the blog.
*Downloading PCAPs requires commercial access to VirusTotal.
Corelight Labs Team - Paul Dokas, Keith Jones, Anthony Kasza, Yacin Nadji, & Vern Paxson
Recently Blackberry analyzed a new GoLang Remote Access Trojan (RAT) named “ChaChi.” Here's how Corelight Sensors can detect the ChaChi RAT.
We hosted a virtual CTF tournament where hundreds of players raced to solve security challenges using Zeek data in Splunk and Elastic. Here are the...
We are excited to announce the expansion of our ETC. In this post, I will provide some further details and what the research team is working on next!