Detecting Log4j exploits via Zeek when Java downloads Java
The blog covers a third log4j detection method, this one focused on the second-stage download that happens after the first stage completes.
We recently discussed some methods for detecting the Log4j exploit, and we’ve now developed another method that everyone running Zeek® or a Corelight sensor can use. Our new approach is based on the rarity of legitimate downloads of Java via LDAP. Zeek does not currently have a native LDAP protocol analyzer (though one is available if you are running Spicy). This will not stop you from detecting this exploit downloading Java over LDAP, though. To see how, read on.
First, you can see what we are going to detect if you open the following PCAP in Wireshark:https://github.com/cyberxml/log4j-poc/blob/main/data/log4j-webapp.pcap
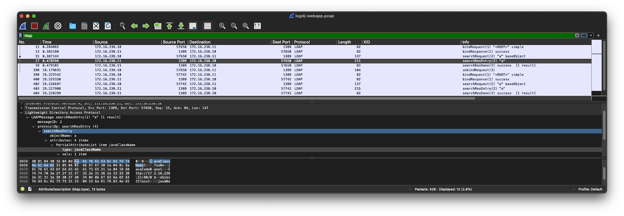
Wireshark decodes the LDAP search response as Java! You can also see “javaClassName” in the bytes. But you may still be asking how we can detect this without a Zeek LDAP protocol analyzer? We will do it with Zeek’s signature framework. With the signature framework, we are able to search the raw bytes for phrases like “javaClassName” inside a valid LDAP connection signature:
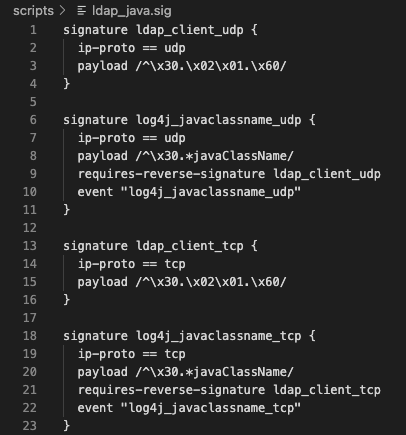
Once the signatures are detected, we will fire a notice for them:
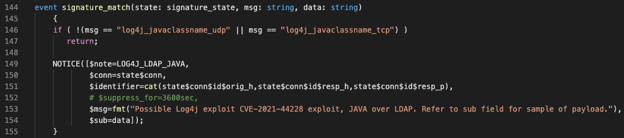
An example log for the PCAP introduced previously looks like this:
https://github.com/corelight/cve-2021-44228/blob/master/testing/Baseline/log4j.ldap_java/notice.log
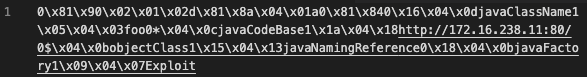
Note that the malicious payload shows up in the sub field of the notice.log, making some instances of incident response triage quick work:
For Suricata users, or those running Corelight sensors with Suricata, the same detection method can be achieved with this pair of Suricata signatures:
alert tcp $HOME_NET any -> any any (msg:"CORELIGHT LDAP Bind Request"; flow:established,to_server; content:"|30 0c 02 01 01 60|"; depth:6; flowbits:set,ldap.bind; flowbits:noalert; classtype:protocol-command-decode; metadata:created_at 2021_12_16, updated_at 2021_12_16; sid:3000015; rev:1;)
alert tcp any any -> $HOME_NET any (msg:"CORELIGHT Java class download over LDAP (CVE-2021-44228)"; flow:established,to_client; flowbits:isset,ldap.bind; content:"javaClassName"; nocase; reference:cve,2021-44228; metadata:created_at 2021_12_16, updated_at 2021_12_16; classtype:attempted-admin; sid:3000016; rev:1;)
If you have suggestions for additional detection methods, or see false positives, please file an issue here with your ideas.
By Corelight Labs Team
The blog covers a third log4j detection method, this one focused on the second-stage download that happens after the first stage completes.
Here are four elements of the security strategy for the next Log4Shell.
Simplify the detection of CVE-2021-44228 exploit (the log4j 0-day known as Log4Shell) with Corelight.