Explore Corelight evidence in Humio Community Edition
Our new collaboration with CrowdStrike and Humio allows our customers and the community to experience the value of evidence.
UPDATE 12-16-20: Corelight Resources
——————————————–
FireEye’s threat research team has discovered a troubling new supply chain attack targeting SolarWind’s Orion IT monitoring and management platform. The attack trojanizes Orion software updates to deliver malware called SUNBURST, which opens a stealthy backdoor for command-and-control and other malicious activity that blends in with Orion Improvement Program (OIP) protocol traffic.
Scott Runnels, a Mandiant researcher involved in the discovery, revealed that Zeek played a key role in FireEye’s investigation and discovery of this new threat:
Given the widespread use of the Orion software we want to provide the community and our customers with some preliminary guidance on how to use Zeek and related tools to manually find and automatically detect this novel threat in their environment.
We will host a webinar this Wednesday, Dec. 16 to deep dive on these methods and tools, which include:
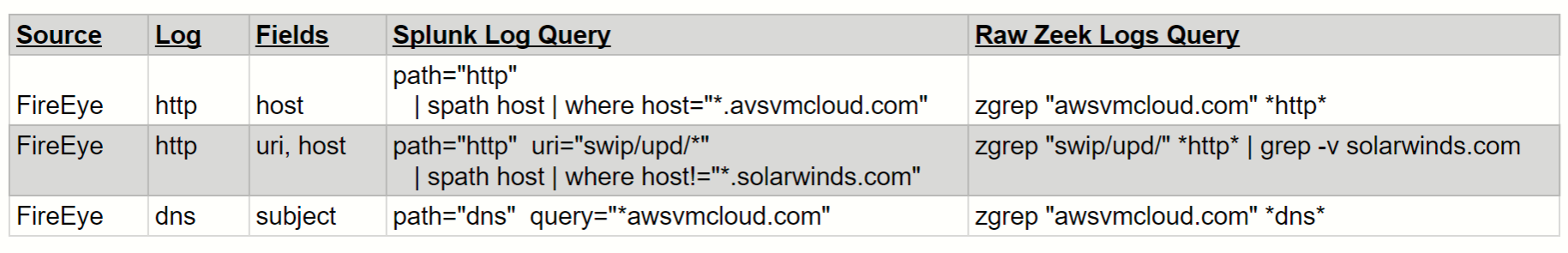
Again, we will host a webinar on Wednesday, Dec. 16 at 7a PST / 10a EST / 3p GMT to deep dive on these methods and tools.
If you would like to attend, please register here: https://www3.corelight.com/finding-sunburst-solarwinds-zeek-suricata
Our new collaboration with CrowdStrike and Humio allows our customers and the community to experience the value of evidence.
Sigma is an open-source project that provides a generic signature format for SIEMs. Here are the benefits of Sigma, and how to get these threat...
We are excited to announce the expansion of our ETC. In this post, I will provide some further details and what the research team is working on next!