How SOCs can level up their PCAP game with Smart PCAP (Part 2)
Learn how Corelight Smart PCAP helps customers streamline workflows and achieve incredible efficiency.
This blog post is the first in a 2 part series on Corelight Smart PCAP.
Tune in next week for part two where we’ll take a deep dive look at Corelight’s PCAP functionality and workflows that accelerate security investigations.
Over the past decade, the full PCAP approach has proved ineffective for core security use cases due to infrastructure overhead, difficulty of use, and high costs for limited retention timeframes. Enterprise security stakeholders, including C-level executives and board members, demand better. Corelight Smart PCAP leverages the power of decades of proven open-source technologies to capture only those packets needed to inform and enable cyber incident response and threat hunting, allowing SOCs to dramatically extend their PCAP retention window from hours/days to weeks/months and more efficiently capture and more quickly retrieve those packets in modern, SIEM-driven workflows.
This blog post describes how Corelight Smart PCAP delivers the most highly operational and cost-efficient packet capture workflows for security teams that completely changes the game to give cyber defenders superior operational advantage.
The perimeter of most network topologies is an easy place to start the Smart PCAP evolution and address low-hanging fruit immediately. The perimeter (Internet, WAN, B2B, VPN, etc.) is where legacy packet capture vendors are going to raise fear, uncertainty, and doubt about the necessity of full packet capture. For starters, the majority of Internet traffic is encrypted. To sidestep this issue, legacy PCAP vendors describe workflows like “decrypt as needed after the fact” or “ replay these packets.” Such workflows get implemented rarely and typically only on small network segments because doing so is cumbersome and unrealistic at scale.
Corelight, on the other hand, leverages Zeek under the hood of our platform to generate high-resolution logs for all TCP/IP communications, including encrypted protocols (e.g., DNS, HTTP, RDP, SSH, TLS, x.509) and also delivers hundreds of novel security analytics around encrypted connections without break and inspect. With this expanded visibility and improved detection capabilities around encrypted traffic, Corelight customers can focus packet capture on decrypted streams.
Before we dive into Corelight Smart PCAP capabilities, lets look at how these insights provide the specific data cyber defenders need to create network baselines on encrypted traffic and perform connection monitoring. Corelight Labs has developed a unique set of analytic capabilities in our platform called Encrypted Traffic Collection (ETC), which provides automated encryption analysis to give cyber defenders insights into the bad things in encrypted traffic without the cost, expense, and complexity of key management in man-in-the-middle decryption. Below are screenshot examples of some the encrypted insights Corelight can generate for organizations:
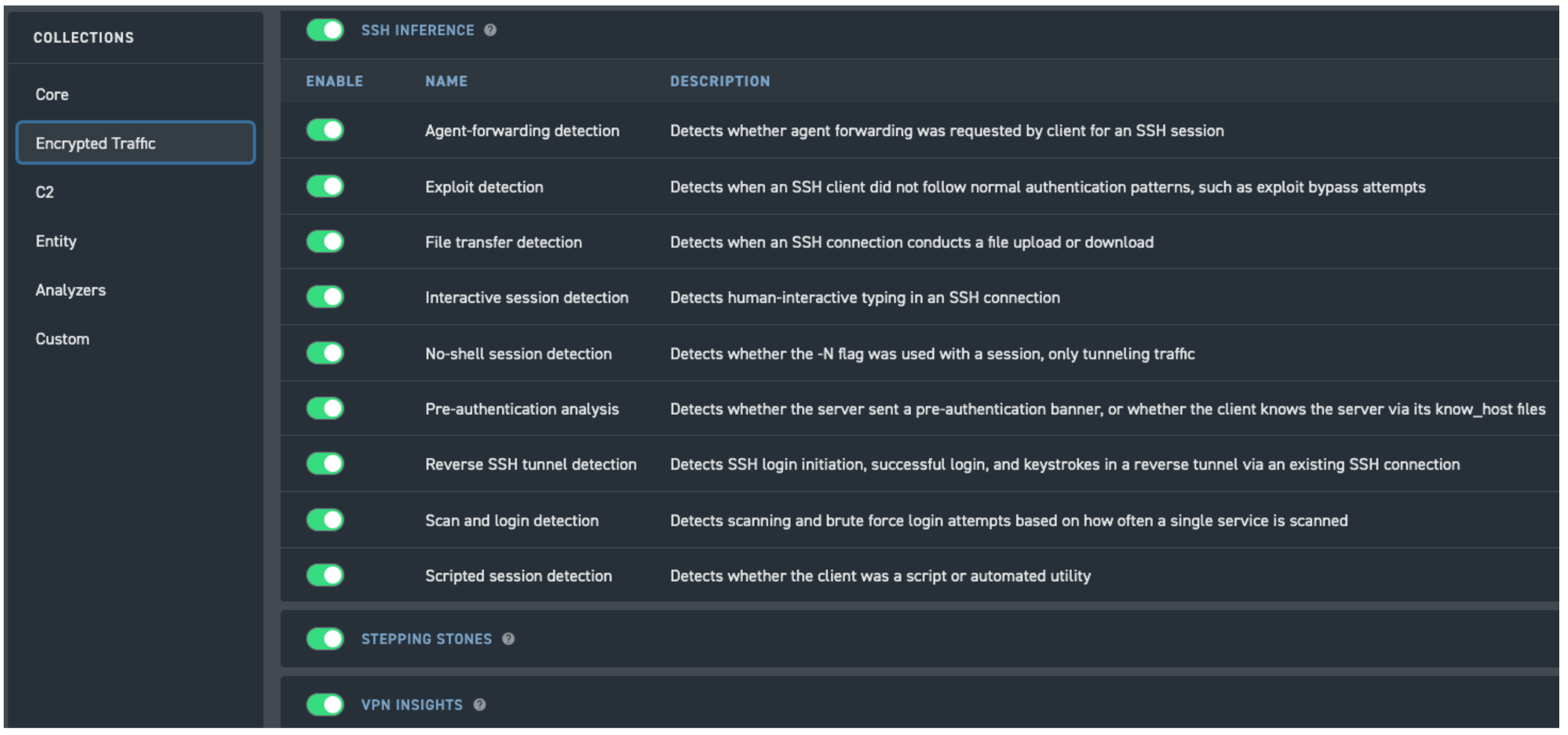
Corelight customers can enable analytics around TLS, RDP, SSH, and VPN traffic.
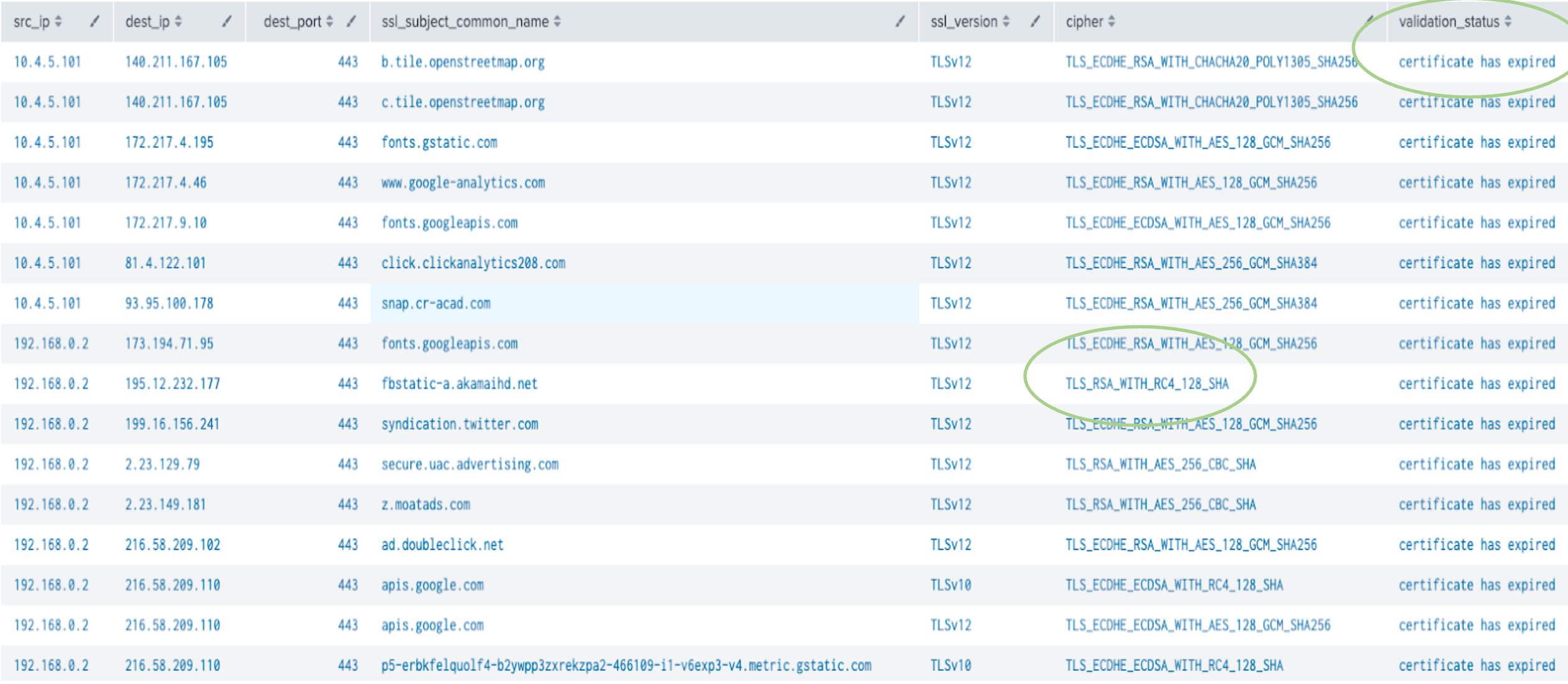
Corelight provides insights around weak encryption connections.
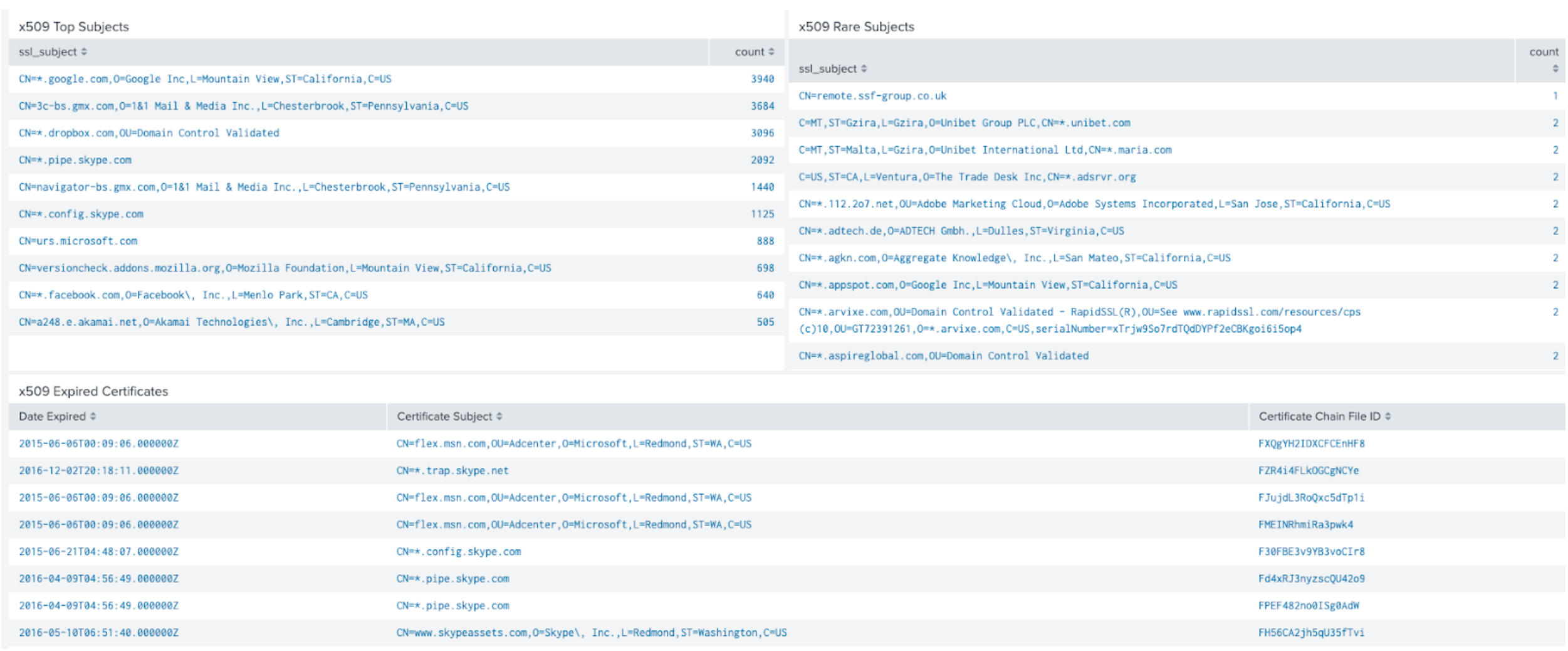
Corelight reveals certificate usage trends in your environment. No PCAPs required here.
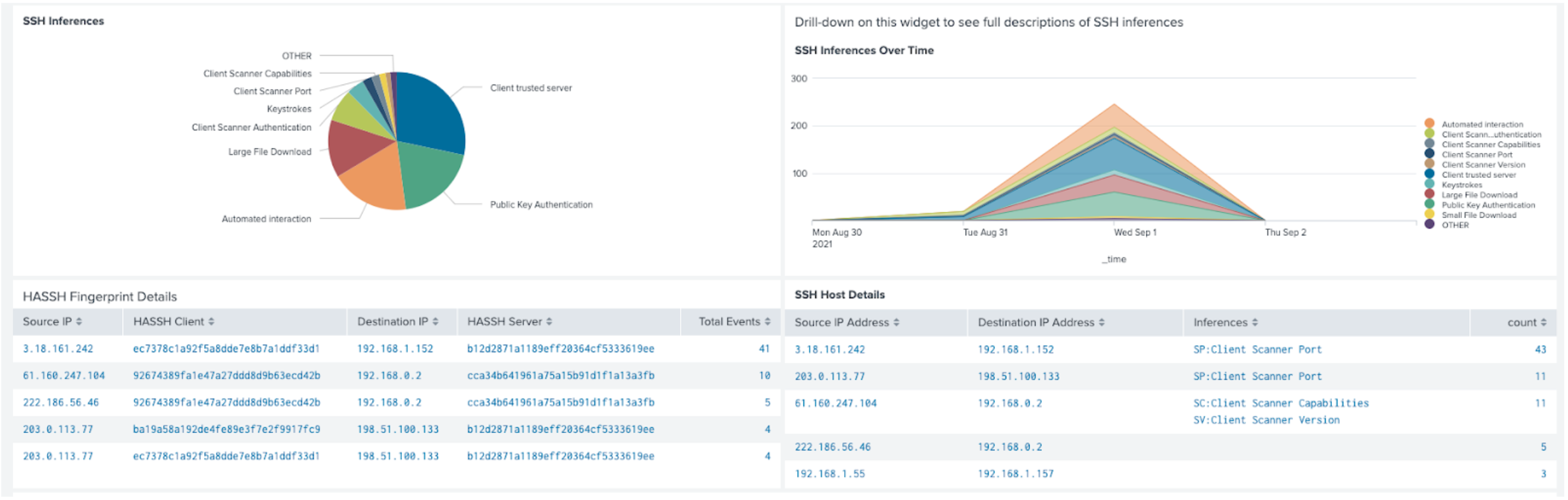 Malicious SSH revealed without decryption and without PCAP!
Malicious SSH revealed without decryption and without PCAP!
As you can see, the smart thing to do at the perimeter with packet capture is to rely on the robustness of Corelight-generated logs to avoid storing any PCAP for encrypted protocols and focus packet capture on connections in the clear. Extending that architectural design model to the internal network is also practical and highly efficient.
Corelight hardware sensors enable a straightforward methodology to minimize the impact of TLS by embedding shunting, the capability at the hardware level to ignore TLS packets after the encryption negotiation completes. The protocol negotiation sequence is all that Corelight needs to collect all the comprehensive metadata in the examples provided above (e.g. to generate an SSH.log for all ssh connections). There may be cases, however, when customers want to capture encrypted packets, e.g. when Corelight parses anomalous encryption sequences in which case customers can elect to automatically trigger a PCAP collection for that one transaction rather than millions of nominally “normal” communications.
Customers can enable shunting in the Corelight management console
Given most traffic is encrypted and Corelight comprehensively logs and analyzes this traffic with no or minimal PCAP storage (at the customer’s discretion), Corelight Smart PCAP allows SOCs to refocus their capture on just those (unencrypted) packets relevant to their investigations. Among many capture trigger capabilities, this primary trigger can easily be configured in the Corelight console:
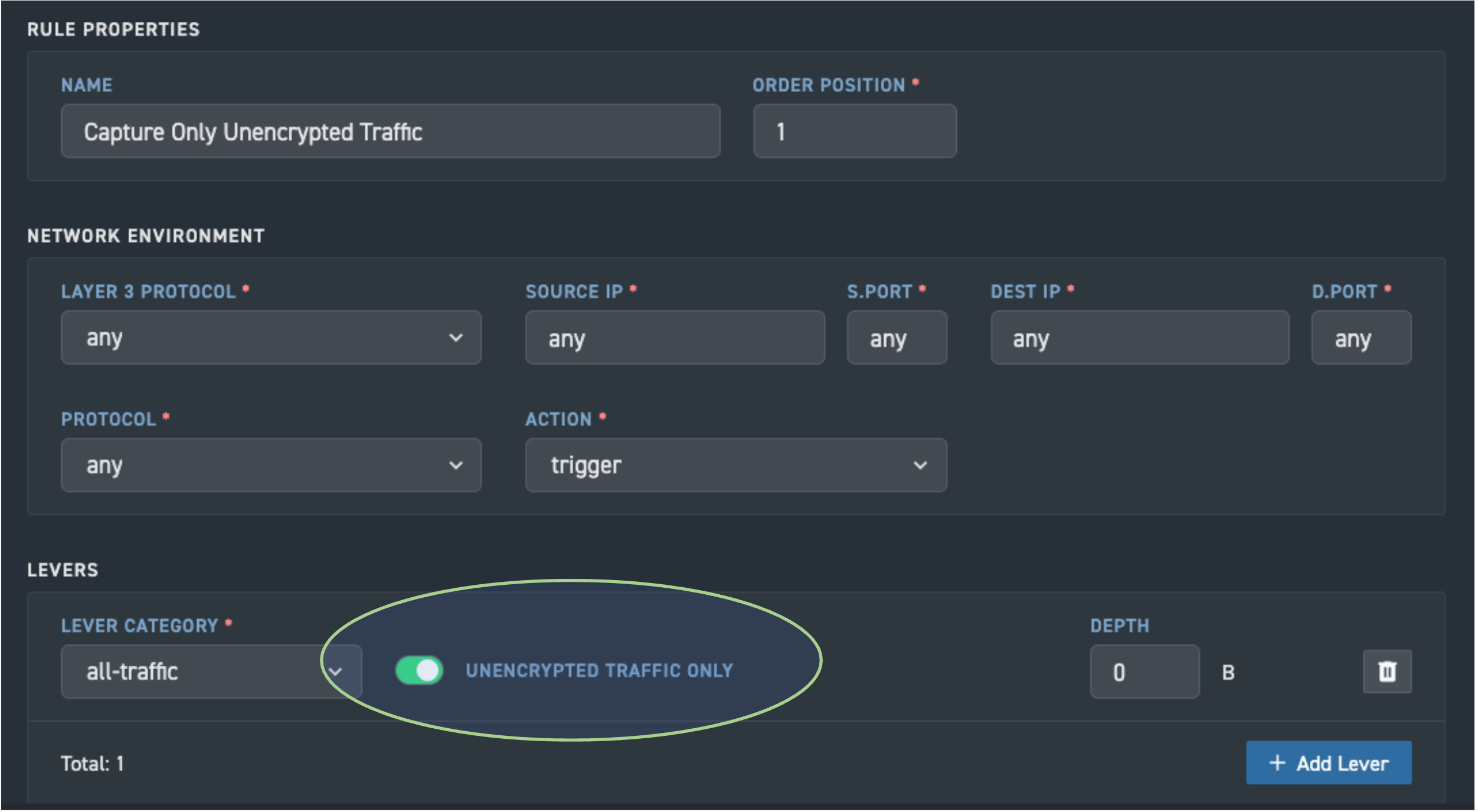
Corelight's PCAP trigger for unencrypted traffic
This blog post is the first in a two-part series on Corelight Smart PCAP.
Tune in next week for part two where we’ll take a deep dive look at Corelight’s PCAP functionality and workflows that accelerate security investigations.
Learn how Corelight Smart PCAP helps customers streamline workflows and achieve incredible efficiency.
Corelight launches software version 22, which introduces a transformative new security product, Smart PCAP, and also enables threat detection in the...
Corelight's data aggregation reduces SIEM ingest by 50-80% compared to legacy network security monitoring tools.