How SOCs can level up their PCAP game with Smart PCAP
Encrypted traffic and the security use case limitations of full packet capture vs. Corelight's Smart PCAP solution.
This is the second in a 2 part series on Corelight Smart PCAP. If you missed Part 1, you can find it here.
In terms of unencrypted traffic, several highly used protocols lend themselves to logging and can significantly reduce the burden of packet capture without lowering the fidelity of information or the capabilities of analysts.
Corelight DNS logs are a customer favorite to replace DNS PCAP and logs from DNS servers. Storing all of the packet capture (PCAP) for DNS just creates process and storage bloat, as analyzing DNS packets is laborious and inefficient, as shown here:
Loading DNS Query packets into Wireshark
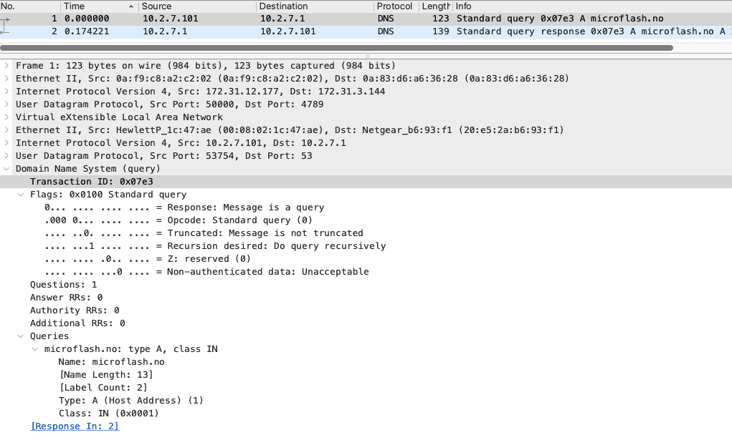
Loading DNS Response packets into Wireshark
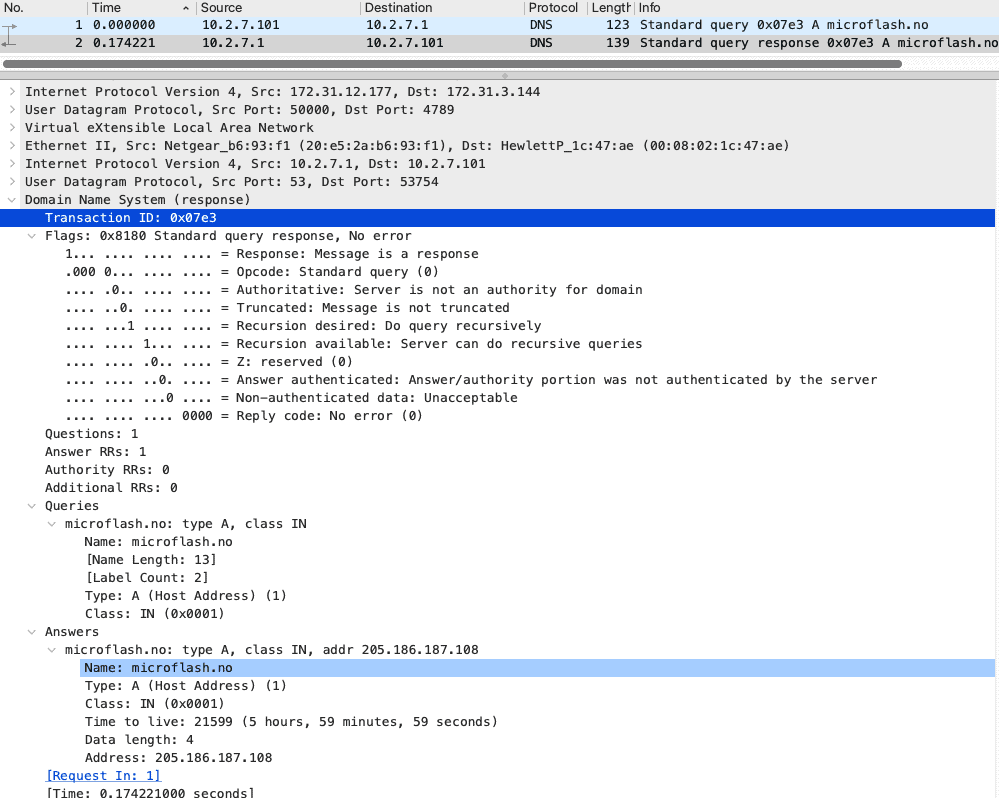
Corelight generates a basic DNS log automatically, which has both the query and the response detail merged in a simple-to-read record:
When streamed automatically to the SIEM(s) of choice, that's all of the data needed to pursue an investigation with none of the PCAP pivots in a single row-based view.
DNS logging is so easy. Let's do another with a more complex data structure and significant PCAP implications. Here is what HTTP looks like in PCAP: 2367 packets to review in this simple HTTP connection.
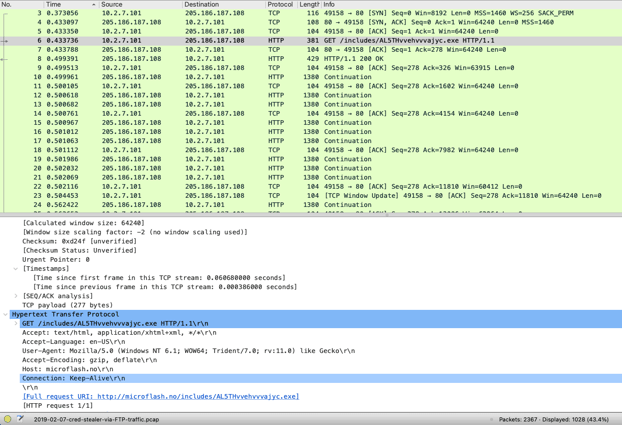
Note: It’s time for more coffee before the analyst digs in, focuses, and tackles this high-touch analysis using PCAP and related tools. For Corelight, this HTTP analysis and detection and the associated DNS detection are automatically summarized in the SIEM, as shown below. While the PCAP-focused analyst goes for coffee, the Corelight-enabled analyst either escalates or closes the incident.
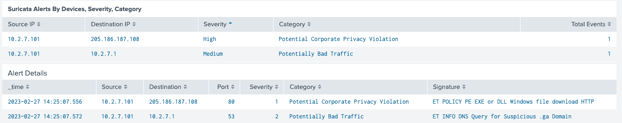
The discussion above supports that the blanket requirement for full packet capture is excessive and inefficient. Excluding encrypted traffic and removing packet capture for protocols where robust data is automatically logged for consumption for SIEM, the need for full PCAP diminishes to a much more manageable percentage of traffic. Are there packets that you should capture? Yes, and for this reason, Corelight took PCAP to the next level by embedding links to the packets into the relevant logs shown above. Suricata has generated a critical alert in this example workflow that "A Network Trojan was detected" on the SMB protocol:

With a simple pivot using Corelight logs, analysts can easily find the associated connection log associated with this alert. In this raw log event, the “all-unencrypted” PCAP trigger has fired and has appended the link to download the PCAP for this transaction. Rather than scouring through gigabytes of PCAP around the time of the event to find the connection and packets, Corelight simply provides a URL directly to the packets the analysts need to pursue or escalate the investigation.
Further, Corelight enables non-alert-based hunting with a simple search showing the inventory of transactions that generated PCAP:
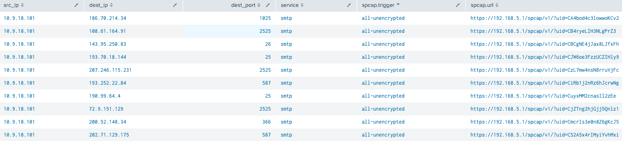
To level up packet capture, customers can achieve incredible efficiency by using metadata logging to replace PCAP, streamline the analyst workflows in the SIEM and reduce PCAP to only what is truly anomalous or requires further investigation. This approach enables organizations to access the efficiency and automation they need to supercharge the SOC and optimize the security stack budget. Visit our Smart PCAP page to learn more.
Encrypted traffic and the security use case limitations of full packet capture vs. Corelight's Smart PCAP solution.
Corelight launches software version 22, which introduces a transformative new security product, Smart PCAP, and also enables threat detection in the...
Recapping our learnings from the Black Hat NOC, using packet captures and Zeek scripting to decode threat payloads.