Zeek & Sigma: Fully compatible for cross-SIEM detections
Corelight recently teamed up with SOC Prime, creators of advanced cyber analytics platforms, to add support for the entire Zeek data set into Sigma.
One of the most important aspects of threat hunting is having a place to start. A question, a theory, or a hunch often begins the hunt. Where you end up may not be where you first intended, but a good hunt will always reveal new information about your environment, your risks, and perhaps even a compromise. Theoretical exercises are a good way to hone in on particular data or threat vectors you want to hunt for, but pretty quickly you’ll need to get your hands into the data by writing some queries.
For the theoretical, the MITRE ATT&CK framework is a great approach to adversarial mapping, and we oriented the latest Corelight Threat Hunting Guide (THG) around the ATT&CK matrix. The guide is a fantastic tool to get familiar with how to hunt using Corelight’s Zeek data, the only things missing are some actual queries to demonstrate the techniques explained in the guide.
Well, Corelight just made that task a lot easier. We worked with SOC Prime to release 70 new threat hunting queries, written in Sigma rule format, which can be translated directly to the most popular SIEM query languages. Designed to be paired with the Corelight THG, these queries map directly to 16 unique MITRE ATT&CK TTPs across 10 categories and provide a way to turn queries into direct action, showcasing how to hunt with Corelight’s Zeek network data. Now you can search for exposed services, identify forced authentication, and find staging or exfiltration behavior just to name a few examples.
If you’re not familiar with Sigma, it’s an open-source project that provides a generic signature format for SIEMs. Write a query or rule once in Sigma and it can be easily translated into Splunk, Elastic, Humio, Azure Sentinel, and other SIEM query languages. We’re really excited about Sigma as a project, and though its early focus was on endpoint data, we added Zeek’s data mapping into Sigma last year. By releasing the new THG rules in Sigma format, we’re hoping to drive more interest and adoption in the network defender community to contribute to both these THG rules and to the Sigma project.
There are a number of great benefits to Sigma:
Sounds great, how do I get these threat hunting rules?
First, you’ll want to make sure you’ve got Corelight or Zeek data in your SIEM. If you haven’t gotten that far yet, not to worry. There are several easy ways to get Corelight up and running, including our awesome Corelight@Home program, or by contacting our sales team.
Once you’ve got Corelight data and you’re ready to hunt, the best place to get the rules is to create a free account on SOC Prime’s TDM:
2. Once in the TDM content section, search for “Corelight” in the search bar and select one of the relevant tags:
3. You’ll then see the individual rules you can explore:
4. If you want to download the whole rule pack, just follow this link:
https://tdm.socprime.com/tdm/info/RbcYuUdzacD7/?p=1
5. Once you’ve found some rules you like, you can translate them directly on TDM into queries for your SIEM, or use some of the other tools (like uncoder.io, sigmac, or others) to translate the queries:
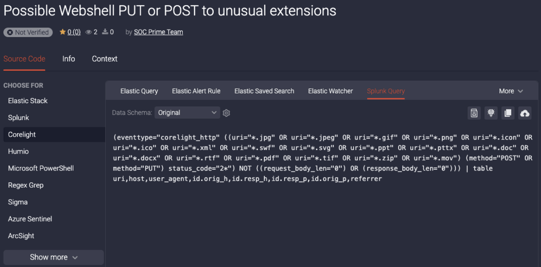
We’re very excited to release these rules and we hope there will be even more new rules added in the coming months. We’re also hoping to hear from you as you use them, and we’re looking for improvements, bug fixes, and better ways to hunt! You can email us directly at info@corelight.com, or make suggestions within TDM.
FAQ:
https://github.com/SigmaHQ/sigma/blob/master/LICENSE
Corelight recently teamed up with SOC Prime, creators of advanced cyber analytics platforms, to add support for the entire Zeek data set into Sigma.
FireEye’s threat research team has discovered a troubling new supply chain attack targeting SolarWind’s Orion IT monitoring and management platform.
We look at the main angles of innovation that are playing out across form factors (on-prem, MSSP, and SaaS) and the elephant in the room that goes...