- Defining defense in depth
- When and where does defense in depth happen?
- How do layers power defense in depth?
- How does defense in depth relate to the cyber or intrusion kill chain?
- Defense in depth example for a sample incident
- Network security monitoring data enables defense in depth
- How does Corelight enable defense in depth?
- About Richard Bejtlich
Defining defense in depth
Defense in depth is a security strategy that can save you when an intruder comes calling. Should your prevention methods fail, defense in depth can also feed critical awareness data to power your detection and response processes.
Defense in depth is a concept familiar to anyone with a security role, whether in the cyber or physical worlds. Any time you apply more than a single layer to protecting an asset, you are acting in the spirit of defense in depth. For example, if you’re using a pass phrase and a security token to access your email, you’re practicing a form of defense in depth.
NIST (https://csrc.nist.gov/glossary/term/defense_in_depth) defines defense in depth as an “information security strategy integrating people, technology, and operations capabilities to establish variable barriers across multiple layers and missions of the organization.” Defense in depth is more than an information security strategy, as it is derived from age-old physical strategies used by militaries, police forces, civilian guards, and others tasked with protecting assets.
Defense in depth seeks to minimize the vulnerabilities portion of the risk equation, which expresses risk as a pseudo-mathematical multiplication of asset value, threat actor capabilities and intentions, and asset vulnerabilities. (You may see this written as R = A x T x V. While not an actual number, the “equation” captures the concept that as any factor trends to zero, risk decreases, and vice versa.) By employing defense in depth, organizations try to make it more difficult for threat actors to exploit vulnerabilities or exposures in assets.
When and where does defense in depth happen?
One promising aspect of defense in depth is that the strategy is not limited to preventive measures. Typically organizations want to prevent as many intrusions and breaches as possible. (An intrusion is any unauthorized access. A breach is the threat actor accomplishing his mission, such as destroying, altering, or stealing data.)
While minimizing the number of intrusions and breaches is preferable, prevention eventually fails. Therefore, wise security leaders understand that they must pair detection and response strategies with preventative measures. That allows them to determine when, where, and how their defenses fail, and to act as quickly as possible to contain any intrusion.

How do layers power defense in depth?
Defenders can apply defense in depth at every point where data is accessed, stored, or moved. Thirty years ago, defenders had few choices when it came to protecting their data. Simple file system access controls, network firewalls, and user management were the main tools available to implement defense in depth.
Today, data can be protected and instrumented in almost every way imaginable. The key to deciding what controls and visibility mechanisms to deploy is to imagine how they would perform when confronted by a live intruder.
The basic idea is to construct scenarios that reflect how intruders try to access data, and then determine if the existing defense in depth mechanisms are sufficient to both limit access and to notify defenders when those limiting systems fail. Red teams, which simulate adversary behavior, can help defenders confront the realities of the effectiveness of their security measures.

How does defense in depth relate to the cyber or intrusion kill chain?
If a security team can detect an intrusion and contain it before it worsens to a breach, then the organization wins and the threat actor loses. Defense in depth assists with this strategy by offering multiple opportunities for security teams to detect and respond to intrusions. The landmark 2010 paper by Eric M. Hutchins, Michael J. Cloppert, and Rohan M. Amin titled “Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains” popularized defense in depth for a variety of counter-threat activities. For more information about the cyber kill chain, see the Corelight blog post How Does the Kill Chain Apply to Network-Derived Evidence?
Defense in depth takes many forms in modern security architectures. Consider this scenario. A threat actor wants to gain access to a document stored on a target’s laptop. The threat actor decides to employ a phishing technique to steal the document. The threat actor composes an email with a malicious PDF attachment. The PDF will seek to exploit one or more vulnerabilities in Windows software when opened by the target.
Defense in depth example for a sample incident
The following are opportunities for defense in depth to not only prevent an intrusion, but also to prompt detection and response processes.
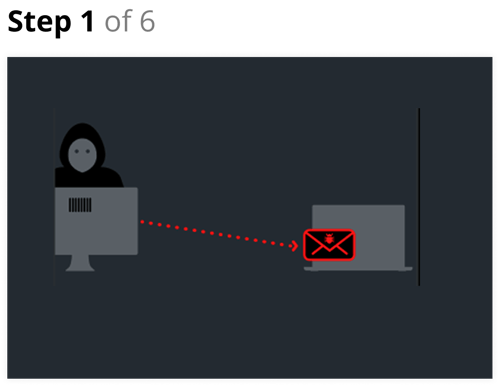
Step 1
- The threat actor transmits the email using a mail server hosted in a country foreign to the target. The email arrives on the mail server, waiting to be read by the target.
Prevention
- The mail server handling email for the target refuses to accept the email from the threat actor. It is configured to reject email from the sender due to previously dodgy behavior. An anti-malware application on the mail server detects the malicious PDF payload and either removes the attachment or scrubs the entire email.
Detection
- The mail server notifies the target security team that it rejected and scrubbed the email.
Response
- The security team incorporates this information into its regular security processes and takes action to be more vigilant if it meets their threshold.

Step 2
- The target receives the email in their queue and reads it on their laptop.
Prevention
- The user notices that the email appears suspicious. The user reports it to the security team.
Detection
- The security team may have already noticed the malicious PDF by virtue of systems and processes to analyze suspicious attachments. They also receive the report from the user.
Response
- As before.
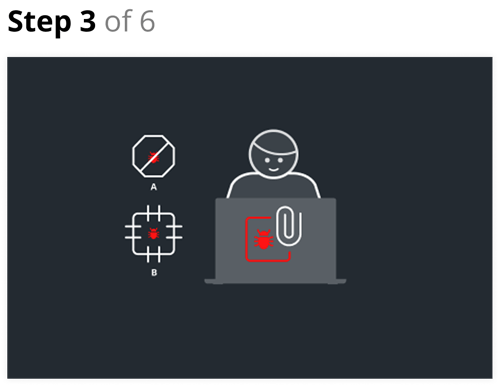
Step 3
- The target opens the attachment on their laptop. In scenario A, the laptop is running Mac OS or Linux. In scenario B the laptop is running Windows but it is patched and the malicious PDF uses an old exploit against a known vulnerability.
Prevention
- On a Mac OS or Linux laptop the malware does not execute as it is written to exploit Windows software.
On the Windows laptop the malware does not execute as the target software is patched.
Detection
- As before.
Response
- Mac OS or Linux: The security team notes that a threat actor managed to deliver a malicious payload to a user, but it did not affect the user. Enhance vigilance as before.
Windows: The security team may receive a notice from an application log that the software encountered unexpected input but it handled it properly and did not succumb to the exploit.
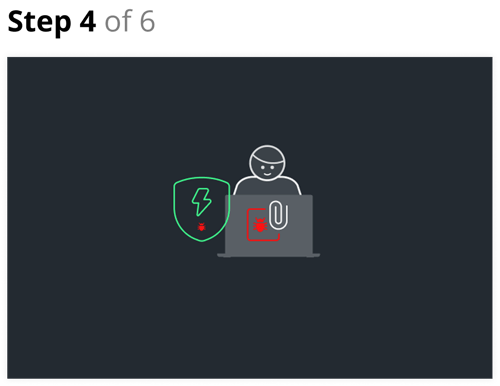
Step 4
- The target opens the attachment on their laptop. The laptop is running Windows but it is not patched against the vulnerability used by the threat actor, either because of missing patches or because the threat actor used a novel exploit. However, the laptop is running an anti-malware application that intercepts and contains the exploit.
Prevention
- The anti-malware application intercepts and contains the exploit.
Detection
- The security team should receive an alert from the anti-malware application that it stopped exploitation.
Response
- As before.
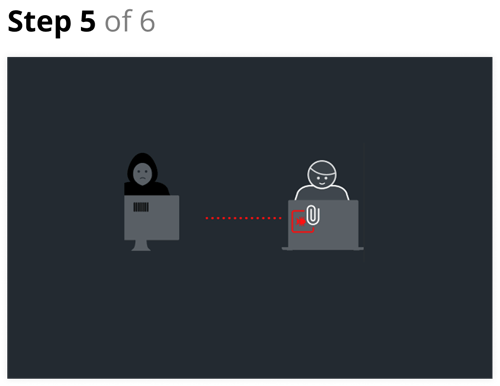
Step 5
Or, the target opens the attachment on their laptop. The laptop is running Windows but it is not patched against the vulnerability used by the threat actor. An anti-malware application is either missing or ineffective against the exploit. The malware seeks to establish a command and control channel with the threat actor prior to stealing data.
Prevention
Although the malware activates and executes its callback to establish a command and control channel, any one or more of the following could interdict the connection if the malware:
- Is not proxy-aware, and the local network requires a proxy to reach the Internet.
- Tries to use a protocol or channel that is denied outbound access.
- Tries to connect to a domain name or IP address that is denied outbound access.
New outbound connections are denied by default, until the user provides consent, either by a host firewall or a network firewall.
Detecion
Any of the above activities could trigger an alert and/or provide material for network security monitoring evidence for the security team.
Response
The security team should identify that outbound command and control is a sign of a compromised computer. The team should validate the activity as quickly as possible and contain the compromised system.
Step 6
The malware succeeds in establishing a connection with its command and control server. At this point, the intruder is basically free to do whatever they want.
Prevention
Prevention has failed.
Detection
Network security monitoring will provide evidence of the command and control activity. The security team must recognize it before the intruder completes his mission.
Response
The security team must identify that outbound command and control is a sign of a compromised computer. The team must validate the activity as quickly as possible and contain the compromised system.
Network security monitoring data enables defense in depth by providing the following forms of network-derived evidence.
ALERTS
Alerts from intrusion detection systems and logic indicate that suspicious or malicious activity may be occurring.
TRANSACTION DATA
Transaction data provides records of all network activity, regardless of whether it was considered suspicious, malicious, or normal. Transaction data summarizes large amounts of network content into high fidelity, compact representations of network activity.
FULL CONTENT
Full content or “smart” PCAP data captures the actual data transferred on the network. If an intruder communicates using unencrypted protocols, keystroke-level insight is available.
EXTRACTED CONTENT
Extracted content or files are the caches of data transferred by the intruder when conducting their activities. These could include a weaponized PDF, additional malware downloaded once command and control is established, or documents stolen by the intruder. In the case of malware, analysts can process extracted content using file analysis tools. Sandboxes and so-called “detonation chambers” are options if the file is captured appropriately.
How does Corelight enable defense in depth?
Corelight enables defense in depth by providing evidence of suspicious and malicious activity through network security monitoring data.
| EVIDENCE | HOW CORELIGHT PROVIDES THE DATA: |
|---|---|
|
ALERTS |
Corelight’s detections highlight how the adversary uses the network to achieve their goals. These detections provide alerts using best-in-class technologies like Suricata and proprietary logic and models developed by Corelight. Detection occurs prior to, during, and after intrusion and breach activity. Security teams leverage alerts from multiple points in the defense in depth cycle to prompt response activities. |
|
TRANSACTIONS |
Corelight’s transaction data takes the form of dozens of logs which capture network activity in a compact but high fidelity manner. These logs are the perfect companion to alert data – alerts are judgments, and transactions are neutral. This means that activity that may not have caused an alert will still be recorded in a transaction. Security teams use transaction data to validate that what they are seeing represents true malicious activity. They also use transaction data to help determine the scope of malicious activity. |
|
PCAP |
Corelight’s Smart PCAP data records the specifics of network conversations in the most detailed way possible – writing raw data to disk. While most cases can be investigated using alert and transaction data, it’s sometimes helpful to have the “source” material as seen on the wire. Security teams use full content data from Smart PCAP to get detailed information on specific aspects of an incident as revealed by defense in depth. |
|
FILE EXTRACTION |
Corelight’s file extraction gives security teams another form of “raw data” that can drive specialized analysis platforms. Mature teams examine payloads for indicators of compromise and derive threat intelligence to feed their detection and response processes. |
AUTHOR:
Richard Bejtlich
Strategist and Author in Residence
Richard is strategist and author in residence at Corelight. He was previously chief security strategist at FireEye, and Mandiant's CSO when FireEye acquired Mandiant in 2013. At General Electric, as director of incident response, he built and led the 40-member GE Computer Incident Response Team (GE-CIRT). Richard began his digital security career as a military intelligence officer in 1997 at the Air Force Computer Emergency Response Team (AFCERT), Air Force Information Warfare Center (AFIWC), and Air Intelligence Agency (AIA). Richard is a graduate of Harvard University and the United States Air Force Academy. His fourth book is 'The Practice of Network Security Monitoring'. He also writes for his blog and Mastodon.


