How Bro logs gave one company better DNS traffic visibility than their DNS servers
Discover how Zeek (formerly Bro) logs gave one company better DNS traffic visibility than their DNS servers.
When Eric M. Hutchins, Michael J. Cloppert, and Rohan M. Amin published their paper “Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains” in late 2010, they changed the way security personnel thought about defending their digital assets. The paper continues to be a useful model for defense today. This article proposes ways that modern network-derived evidence applies to the kill chain.
The original kill chain paper built on previous work, such as 2000s-era United States Department of Defense Joint Staff publications which described “a kill chain with [the] stages find, fix, track, target, engage, and assess.” These terms describe steps taken by military operators to detect, deny, disrupt, degrade, deceive, or destroy adversary targets. Rather than using a kill chain for offense, Hutchins, Cloppert and Amin imagined how defenders could take similar actions against an adversary targeting friendly digital assets.
Their paper featured a matrix which explained the concept and mapped defensive technologies and tactics against phases of adversary activity.
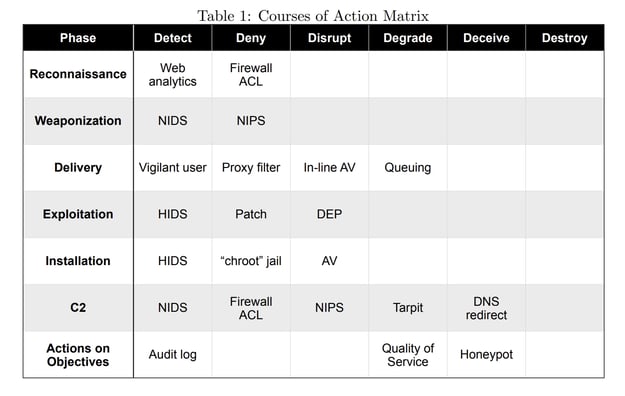
The table shows how a mix of technologies can be applied to implement a kill chain.
The following sections will use the original definitions of the kill chain phases, and will add network-derived evidence (if applicable) to assist defenders.
Hutchins, Cloppert, and Amin described the reconnaissance phase as follows:
“Research, identification and selection of targets, often represented as crawling Internet websites such as conference proceedings and mailing lists for email addresses, social relationships, or information on specific technologies.”
This concept of reconnaissance is usually expanded to include a suite of behaviors whereby adversaries collect information about a target. If the adversary conducts network-based reconnaissance against Internet-accessible properties, then defenders have an opportunity to collect network evidence.
This evidence could take the form of connection logs in Zeek format, domain name system (DNS) requests made to the target’s DNS servers, and protocol-specific queries to Internet-exposed services. These include HTTP requests to Web servers, Windows protocol (often Server Message Block, or SMB) exchanges with Microsoft devices, and other interactions with Internet systems. The cryptographic protocols used by the adversary may also provide clues, and such information can be found in JA3 and other logs in Zeek format.
The weaponization stage of the kill chain is sometimes misunderstood by security teams. Hutchins, Cloppert, and Amin described it as follows:
“Coupling a remote access trojan with an exploit into a deliverable payload, typically by means of an automated tool (weaponizer). Increasingly, client application data files such as Adobe Portable Document Format (PDF) or Microsoft Office documents serve as the weaponized deliverable.”
This refers to an action by the adversary within their own toolchain to create code to exploit a target. There is no interaction with the target during this phase. The kill chain authors included this step to emphasize that the process of weaponization often leaves toolmarks, just as the barrel of a firearm leaves marks on a projectile. Hutchins, Cloppert, and Amin advocated that defenders look for the toolmarks left on malicious code to assist the defensive process.
With respect to network-derived evidence, defenders can extract files from traffic (during the delivery phase, next) and look for these toolmarks. Such indicators include specific file headers or other artifacts unique to software which produced the file. The kill chain authors recommended collecting a corpus of files and analyzing them for toolmarks. The results of this investigation could then be applied to files entering or leaving an organization. The point is that although other technologies might not initially identify a file as “malicious,” if it bears specific toolmarks it could be the product of a malicious process that has successfully evaded existing defenses.
Hutchins, Cloppert, and Amin defined delivery as follows:
“Transmission of the weapon to the targeted environment. The three most prevalent delivery vectors for weaponized payloads by APT actors, as observed by the Lockheed Martin Computer Incident Response Team (LM-CIRT) for the years 2004-2010, are email attachments, websites, and USB removable media.”
This is a straightforward step in the kill chain. With respect to network evidence, defenders can review connection logs and protocol-specific logs for signs of inbound malicious activity. The collection of full content data in PCAP format also provides defenders with the opportunity to observe and store a copy of the adversary’s code as it enters the network.
Consider how the three examples would or would not manifest in network data, however.
“Email attachments” means that a target receives an email with a malicious attachment. If defenders are scanning email attachments for signs of malicious intent, they might detect the “weapon.” Inspecting embedded URLs is another common defensive practice.
“Websites” means that the target visits a website compromised by the adversary, and in addition to any desired content also receives malicious content. This technique is sometimes called a “watering hole attack.” The canonical example is an employee visiting a sports news site at work, at which point the sports news site delivers a malicious payload to the employee’s computer. Network evidence might capture the transfer of the payload.
“USB removable media” means that a person inserts a flash drive into a sensitive system, and receives unwanted malicious content. Some USB-hosted malware attacks the target independently, while others require user interaction. There is generally no network evidence at this point in the kill chain for physical hardware attacks like this.
The kill chain authors addressed exploitation and installation as follows:
“After the weapon is delivered to victim host, exploitation triggers intruders’ code. Most often, exploitation targets an application or operating system vulnerability, but it could also more simply exploit the users themselves or leverage an operating system feature that auto-executes code… Installation of a remote access trojan or backdoor on the victim system allows the adversary to maintain persistence inside the environment.”
Hutchins, Cloppert, and Amin defined command and control as follows:
“Typically, compromised hosts must beacon outbound to an Internet controller server to establish a C2 channel. APT malware especially requires manual interaction rather than conduct activity automatically. Once the C2 channel establishes [sic], intruders have “hands on the keyboard” access inside the target environment.”
Detecting command and control is one of the key benefits of robust network evidence. Unless an intruder is local to the target system, he or she must establish a remote connection to the target. Almost all remote connections traverse the Internet, providing a means for defenders to log and detect this activity. Connection and protocol-specific logs in Zeek format are key. They should be kept for as long as the organization’s budget and policies will allow.
Logging and detecting C2 also benefits from collecting traffic in PCAP format. Some C2 traffic is not encrypted, allowing defenders to gain insights on adversary activity. Even when encrypted, defenders may be lucky enough to recover an encryption key from a compromised target system. When applied to stored network traffic, defenders can again peer into adversary actions.
The kill chain authors provided a final “catch all” phase for all other adversary activity beyond C2. The describe actions on objectives as the following:
“Only now, after progressing through the first six phases, can intruders take actions to achieve their original objectives.”
This is the stage in the kill chain where defenders look for escalation of privileges, lateral movement, additional reconnaissance, collecting sensitive data, and eventual exfiltration. If the adversary is moving within a target network, then network-derived evidence will provide rich insights into this phase.
The kill chain paper and its ideas were a landmark in the development of defensive thought. Other forms of “kill chains” had already existed for several years, such as the “phases of compromise” in my first book The Tao of Network Security Monitoring: Beyond Intrusion Detection (Addison-Wesley, 2004): (1) reconnaissance, (2) exploitation, (3) reinforcement, (4) consolidation, and (5) pillage. The “anatomy of a hack” from Hacking Exposed, Fourth Edition (McGraw-Hill Osborne Media, 2003) was similar: (1) footprinting, (2) scanning,(3) enumeration, (4) gaining access, (5) escalating privilege, (6) pilfering, (7) covering tracks, (8) creating backdoors.
What made the approach offered by Hutchins, Cloppert, and Amin unique was its focus on aligning one’s security program with the steps in the kill chain. They showed example technologies to detect, deny, disrupt, degrade, and/or deceive the adversary, unlike previous efforts. Network security monitoring fits this model well, because it provides a way to detect and respond to intruders before they accomplish their mission. Therefore, the intrusion kill chain offers a powerful model for identifying the data defenders need to collect and analyze.
For more on network security monitoring, I encourage you to learn more about Zeek, the world's most widely used network security monitoring platform and the foundation for Corelight network evidence.
Discover how Zeek (formerly Bro) logs gave one company better DNS traffic visibility than their DNS servers.
In this post, we’ll explore DNS over TLS (DoT) and DNS over HTTPS (DoH). Before examining DoT and DoH, it’s important to take a quick look at DNS...
This blog is a brief story of a few points that occurred to me during the less than 24 hours it took to turn around this package from dev to testing.