Executive Summary
Managed Detection and Response (MDR) services have become an essential component of contemporary security operations due to the escalating complexity and volume of cyber threats and skills shortages on security teams. Key MDR capabilities include real-time network monitoring, automated responses to threats, and scheduled and ad-hoc threat hunting.
MDR services integrate a provider's technology stack, which often includes a Security Information and Event Management (SIEM), with the customer's environment. This streamlines the aggregation and analysis of security data, and can facilitate effective threat hunting, investigation, and response to threats.
The services provided by MDR vendors can vary, with some offering additional asset management, security assessments, and vulnerability management. Managed Detection and Response service adoption models range from full-service offerings to collaborative approaches where in-house teams handle investigation and response based on the provider's recommendations.
Network evidence is crucial for MDR services to effectively detect and counter advanced attacks that may not have known signatures or behaviors.
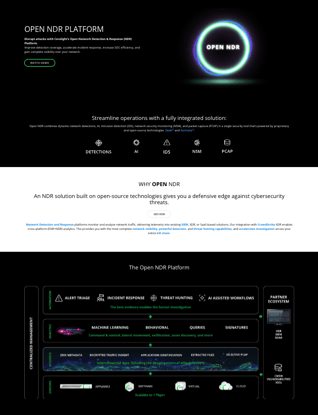
Corelight's Open Network Detection and Response (Open NDR) platform enhances MDR service efficacy by providing detailed security analytics and identifying a wide array of adversarial tactics and techniques. By leveraging machine learning, open-source technologies, and partnerships with leading security organizations, Corelight offers enriched network evidence that, when integrated into Managed Detection and Response services, significantly improves visibility, optimizes SIEM data ingestion, and accelerates investigation and response times.
What is Managed Detection and Response?
Managed Detection and Response (MDR) is an outsourced cybersecurity service that provides organizations with a robust technology stack and a team of expert analysts for continuous monitoring, threat detection, and response across various infrastructures.
Core capabilities of MDR
Capabilities offered through MDR services differ from vendor to vendor, but organizations should expect their MDR service to include:
- A technology stack operated by the service provider, which facilitates real-time monitoring, threat identification and response capabilities.
- A team of human security operations experts who leverage the technology stack.
- 24x7 monitoring of on-prem, cloud, and SaaS infrastructure.
- Correlation and prioritization of security data, which enables detection of threats by using established processes and content.
- Scheduled and ad-hoc threat hunting.
- Automated response capabilities (e.g., host isolation and re-authentication) to contain and mitigate the impact of threats.
Some MDR service providers offer additional capabilities such as management of assets (e.g., endpoints, firewalls, security assessments, and vulnerability management.)
Why are organizations using MDR services?
As cyber threats escalate in volume, diversity, and complexity, organizations find it increasingly difficult to equip their security operations centers (SOCs) with the necessary high-skilled professionals and tools. In response, Managed Detection and Response providers offer services tailored to bolster cybersecurity posture and mitigate cyber risk.
According to a report from Gartner, Emerging Tech: Security — Adoption Growth Insights for Managed Detection and Response MDR mindshare has continued to increase by double digits year over year, and strong MDR demand continues regardless of industry size and vertical. In another research, Gartner predicts that by 2025, 50% of organizations will use MDR service monitoring, threat detection, and response.
However, there are over 300 MDR providers, making it challenging for security leaders to determine which service is best suited for their environment.
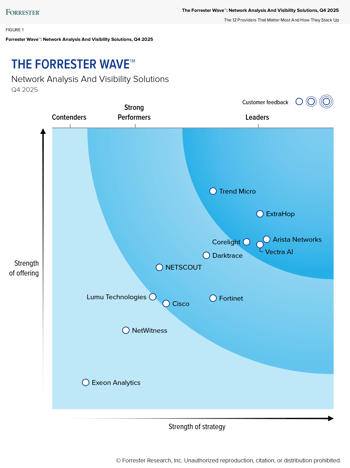
Corelight named as a Leader in Forrester Wave™: Network Analysis and Visibility Solutions, Q4 2025
How does MDR service work?
Managed Detection and Response service providers deploy their technology stack in the customer environment and drive integration with existing technologies. Each provider's stack is different, but most include SIEM capability to aggregate and correlate security data.
- Some MDR providers use a fine-tuned commercial SIEM that is either bundled with the MDR service or a pre-existing SIEM in customer environments.
- Other MDR providers use their own proprietary SIEM-like tool that offers similar functionality.
Although SIEMs offer a centralized repository for alert correlation and curation, ingesting all the data across the environment into a SIEM can be expensive and may not scale for every organization.
Managed Detection and Response services typically include:
- Aggregation of security data: Security telemetry is gathered across environments, including endpoints, firewalls, networks, cloud deployments, email, etc.
- Threat detection: Alert correlation and curation, together with input from threat intel feeds and business context, help security teams determine whether anomalies and events are possible threats.
- Threat hunting: Skilled threat hunters use the detection data to form hypotheses and look for tactics, techniques, and procedures (TTPs) commonly used by cybercriminals and threats that may bypass various security tools.
- Investigation: Determine severity and scope of the detected threats to define next steps and response action.
- Response: Take remedial actions to contain and minimize the impact of threats.
There are three models for MDR service adoption:
- Provider performs all the functions, from aggregation of security data to response.
- Provider performs aggregation of security data, threat detection, and threat hunting, and the in-house team works on investigation and response based on provider’s recommendation.
- Provider performs some response actions like host isolation and step-up authentication, while the in-house team engages in response actions (e.g., firewall rule changes and data backups.).
Irrespective of the model of adoption, to be effective in threat detection and response, the Managed Detection and Response service needs high-quality evidence derived from networks, systems, and other sources — evidence that makes it possible to reconstruct the mechanism of a breach and understand its severity and impact.
Why is network evidence integral to MDR service?
If the Managed Detection and Response service only deploys an alert-based strategy for threat detection, then it will only detect threats based on known attack types and rely on threat hunting for unknown threats. MDR services that rely on endpoint visibility but do not analyze network data (e.g., DNS, DHCP, and IDS), limit the visibility from an analyst’s perspective. Alerts are certainly necessary, but they only capture information about known variables. Alerts can be leveraged when responding to an incident, but this approach is reactive.
Although the majority of MDR providers highlight their solution’s network data aggregation and curation, SIEM-based tech stacks limit how much network data can be realistically ingested and analyzed. A full packet capture (PCAP) ingest is certain to test the ingest licensing and utilization of the SIEM. On the other hand, using an sFlow-based ingest approach optimizes bandwidth but limits the context needed for accurate threat detection.
An evidence-based strategy involves collecting and analyzing data across the network to identify and disrupt advanced attacks that don’t match known signatures or behaviors. The right network evidence can be helpful for comprehensive visibility, early detection of potential compromise, and adding context to investigations that can reveal how attackers entered or moved around a network.
How Corelight’s Open NDR improves the efficacy of MDR services
Corelight delivers a comprehensive suite of network security analytics that help MDR providers identify more than 75 adversarial TTPs across the MITRE ATT&CK® spectrum. These detections reveal known and unknown threats via hundreds of unique insights and alerts across machine learning, behavioral analysis, and signature-based approaches. Corelight’s Open NDR platform leverages powerful machine learning and open source technologies that can detect a wide range of sophisticated attacks and provide analysts with context to interpret security alerts, together with LLMs such as ChatGPT.
Our use of Zeek® and Suricata, as well as partnerships with Crowdstrike, Microsoft Alliance, and other security consortiums delivers the double benefit of maximized visibility and high-quality contextual evidence that has helped us expand our offerings of supervised and deep learning models for threat detection.
Corelight’s network evidence can be enriched and normalized before it is ingested into SIEM tools in the MDR tech stack. Incorporating network evidence in Managed Detection and Response services can help boost visibility from the perimeter to endpoints and across the network, optimize data ingestion in the SIEM, understand the ground truth faster, and improve investigation and response times.
Looking to improve the efficacy of your MDR service as a provider or security operations leader? Contact us
Close the case on ransomware
In high stakes ransomware investigations, many security teams are unable to answer key questions and default to worst-case assumptions. With complete visibility from Corelight, teams can avoid costly overreactions. One customer, when confronted with a $10 million ransomware demand, used Corelight to prove the exfiltrated data had no real value while providing legal aircover for refusing to pay the ransom.

Recommended for you
Book a demo
We’re proud to protect some of the most sensitive, mission-critical enterprises and government agencies in the world. Learn how Corelight’s Open NDR Platform can help your organization tackle cybersecurity risk.