How does a next-generation SIEM solution work?
Modern technology
Next-generation SIEM uses modern technologies to enable long-term storage and fast analysis of high-quality data, such as Corelight data. This contrasts with legacy SIEMs, which often have limitations around data ingestion, storage, search and associated licensing costs. Next-gen SIEMs leverage cloud-scale infrastructure, big data architectures and advanced indexing techniques to store and analyze large datasets efficiently.
Machine learning and AI
Next-gen SIEM applies machine learning and artificial intelligence to large amounts of data to identify complex and evolving threats. These systems detect anomalies and suspicious patterns in real time and provide early warnings of potential security incidents. They are designed to handle large volumes of data from diverse sources, including cloud environments, IoT devices and traditional IT infrastructure while ensuring fast processing and analysis that delivers timely and actionable insights.
Integration
Seamless integration with a wide range of security solutions, such as network detection and response (NDR), firewalls, intrusion detection systems, and endpoint protection platforms allows next-gen SIEM to correlate data from multiple sources. This can give security teams a holistic view of the security landscape and improve the accuracy of threat detection.
What are the benefits of a next-generation SIEM?
Improved threat detection
By leveraging advanced technologies such as machine learning, artificial intelligence, and big data analytics, next-gen SIEMs provide superior threat detection capabilities that can identify complex and evolving threats that traditional systems might miss.
Accelerated response
Next-gen SIEM facilitates real-time network monitoring and analysis and ensures prompt detection and response to security incidents, which minimizes potential damage and downtime.
Cost savings
Next-gen SIEMs built on cloud-scale architectures not only allow for the ingestion and long-term storage of vast amounts of high-quality data; they typically offer usage-based licensing models that can significantly reduce storage costs.
Improved operational efficiency
The integration and orchestration of various security tools enable automated responses to threats, reducing the operational burden on security teams and allowing them to focus on strategic initiatives.
How can advanced NDR technology benefit a next-generation SIEM?
Adversaries are always targeting blind spots.
In recent years attacks have shifted toward the network periphery where endpoint detection and response (EDR) sensors cannot be deployed. When EDR data isn’t available, NDR data is the best substitute, as it provides coverage for every device on the network. By integrating your EDR and NDR data within a next-generation SIEM, you can catch attacks in a former blind spot and enhance operational efficiency.
Adversaries can’t evade the network.
Virtually all attacks cross the network and leave a trail of evidence behind. NDR technology continuously monitors network traffic in real time, using machine learning and behavioral analytics to identify anomalies and potential threats that might go unnoticed by traditional security measures. By integrating NDR with a next-gen SIEM, organizations can achieve better visibility of adversaries’ movement by using high-fidelity network evidence that SIEMs can analyze alongside logs and events from other sources, such as EDR.
Defenders can uncover advanced attacks.
NDR technology excels at identifying sophisticated attacks, such as lateral movement and command and control (C2), by analyzing network behavior patterns. The detailed network insight it provides allows the SIEM to correlate and contextualize security events more accurately, reducing false positives and enabling faster, more precise incident response.
Enhance visibility for hybrid networks.
NDR solutions can provide visibility for cloud and on-prem environments. Additionally, the integration of NDR technology enhances visibility into network traffic, including east-west (internal) and north-south (incoming and outgoing) flows. This comprehensive visibility is crucial for detecting internal threats and compromised devices, which are often missed by perimeter-focused security tools. The enriched data from NDR feeds into the SIEM, providing a holistic view of the security landscape and enabling more informed decision-making.
Enhanced threat hunting
Moreover, NDR technology provides real-time network evidence and historical data to support long-term threat hunting and forensic investigations. This historical context is vital for understanding the full scope of an incident, identifying patient-zero and tracking an attacker's activities over time.
Security response automation
Finally, seamless integration between NDR and next-gen SIEM facilitates automated and orchestrated responses to detected threats. By leveraging the detailed network insights provided by NDR, the SIEM can trigger automated workflows to contain and mitigate threats, thereby reducing the response time and minimizing potential damage.
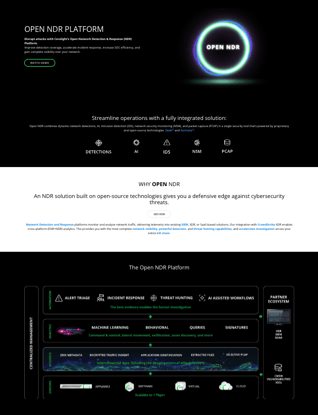
Corelight’s Open NDR Platform delivers the data of choice for next-generation SIEM
Corelight's Open NDR Platform provides rich network telemetry, intrusion detection, advanced detection capabilities (including machine learning) and the capacity to drill down into packets. These capabilities improve threat detection and accelerate incident response, which can increase next-generation SIEM effectiveness for all organizations.
Utilizing Zeek® to convert network traffic into comprehensive, correlated evidence and analytics, the Open NDR Platform integrates easily with most next-generation SIEMs and delivers the broadest protocol coverage and built-in detections and machine learning analytics to helps security teams scale their security operations in response to an evolving threat landscape.