COMPLETE VISIBILITY
Gain a commanding view of your organization and all devices that log onto your network—with access to details such as SSH inferences, DNS query/response, file hashes, TLS connection details, and HTTP content.

COUNTER UNCERTAINTY WITH VISIBILITY
Corelight delivers visibility into every connection to give a complete understanding of your network. Our out-of-band sensors parse all North-South and East-West traffic, turning it into rich, correlated, security-specific evidence that goes back months, not days. Read more on the blog.
HOW CORELIGHT EXPANDS VISIBILITY
One source for all evidence
See DNS, SSH, IoT, and more
Get visibility into traffic that's been hidden due to technical or organizational issues. If it has an IP address, Corelight can see it. Read the blog on finding Sunburst backdoors.
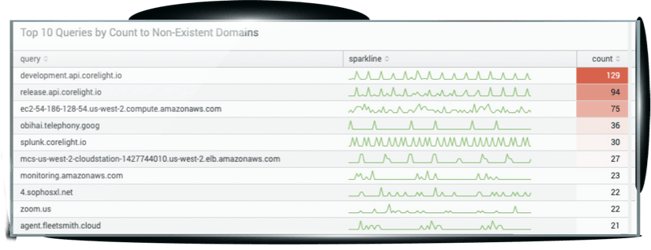
Isolate risk with machine learning
See how Corelight's machine learning can help you spot anomalies and attacks in less than a minute.
Complete coverage on-prem or in the cloud
Corelight's sensors and detections give you complete visibility into your network, whether your enviroment is on-prem, hybrid, or multicloud. Read the blog.
Detect and disrupt cloud-specific threats
Securing multi-cloud environments presents significant challenges due to the expanding attack surface and constant evolution of cyber threats and ever-changing network topology. See how to effectively mitigate limited visibility, missed detections and inefficient response times.

Extending NDR visibility in AWS laaS
While cloud environments offer rich telemetry and logs, achieving complete visibility into them is challenging. Issues can include ensuring that logging is configured on every service, ingesting diverse log types into a SIEM, and correlating logs from different cloud environments. Luckily, Corelight has the answers. Read more on our blog.

Recommended for you