Detecting the STRRAT Malware Family
In recent months STRRAT has become one of the top malware families submitted to Any.Run. Here's how to detect it.
Corelight recognized as a leader in the 2025 Gartner Magic Quadrant™ for network detection and response
Corelight recognized as a leader in the 2025 Gartner Magic Quadrant™ for network detection and response
Corelight has strengthened the Suricata integration within its Open NDR Platform, empowering customers with a custom ruleset, the Corelight Feed, designed to swiftly detect and help respond to emerging threats. With a new monthly update cycle, Corelight ensures that organizations stay ahead of the latest vulnerabilities and enhance their network security posture effortlessly.
Just over four years ago, Corelight launched our Suricata integration , bringing together two of the most powerful and widely used open-source network security tools into our Open NDR Platform--Zeek and Suricata. Our Suricata integration goes well beyond simply running the two engines side by side. By fusing the alerts from Suricata with the powerful contextual data from Zeek, we create a combined log to help analysts triage and respond to alerts more quickly. This tight coupling also helps integrate with our Smart PCAP product and other features of our platform.
Of course Suricata is an Intrusion detection system , which requires loading rules to trigger alerts, so. . . what rules do our customers typically use, and how do they get them?
Most of our customers license Proofpoint’s Emerging Threats (ET) Pro rules feed from Corelight, as it’s one of the most widely used rulesets for Suricata, spanning more than 80,000 rules targeting attack tools, malware, phishing, and much more. ET Pro is a fantastic resource and, we’ve also dedicated resources to examining and tuning the rules specifically for our customers to get the most value from them right out of the gate. We provide a “Day 1” tuned ruleset, continuously adapted based on our own customer feedback and testing, which is an excellent starting point to balance signal and noise. We also make it extremely easy to enable and tune your complete Suricata ruleset within our Fleet Manager product.
Making ET Pro available (and providing a recommended ruleset for our customers) is only one component of Corelight’s approach to Suricata rules, though. We also offer the Corelight Feed.
Our company has developed its own proprietary ruleset, the Corelight Feed, available to all our Suricata customers. Designed by the Corelight Labs team, the Corelight Feed focuses on rapid response to emerging threats, including zero-day exploits, lateral movement and more. With nearly 350 custom rules (and we’re always adding more) that cover nine categories and 50 unique TTPs of MITRE ATT&CK, the Corelight Feed is a powerful tool that enables customers to respond swiftly and decisively to network threats.
For the Corelight Feed, we’re now going to be using a monthly release cycle (with exceptions for out-of-band rapid response content that greatly benefits from near-immediate distribution). You can now expect regular emails detailing the new rules and any significant changes to the Corelight Feed process.
As we’ve just made some big changes this month, below you’ll see the text of the update email that will be going out shortly to all of our Corelight Suricata customers.
It’s worth noting a few important things from this latest release:
You can enable the Corelight Feed in the Suricata rules management section within Fleet Manager. Under the “Enable Suricata Automation” section, you’ll see “Corelight Feed” at the top. Just make sure that’s enabled and the Corelight Feed will stay updated along with the rest of your configured rulesets.
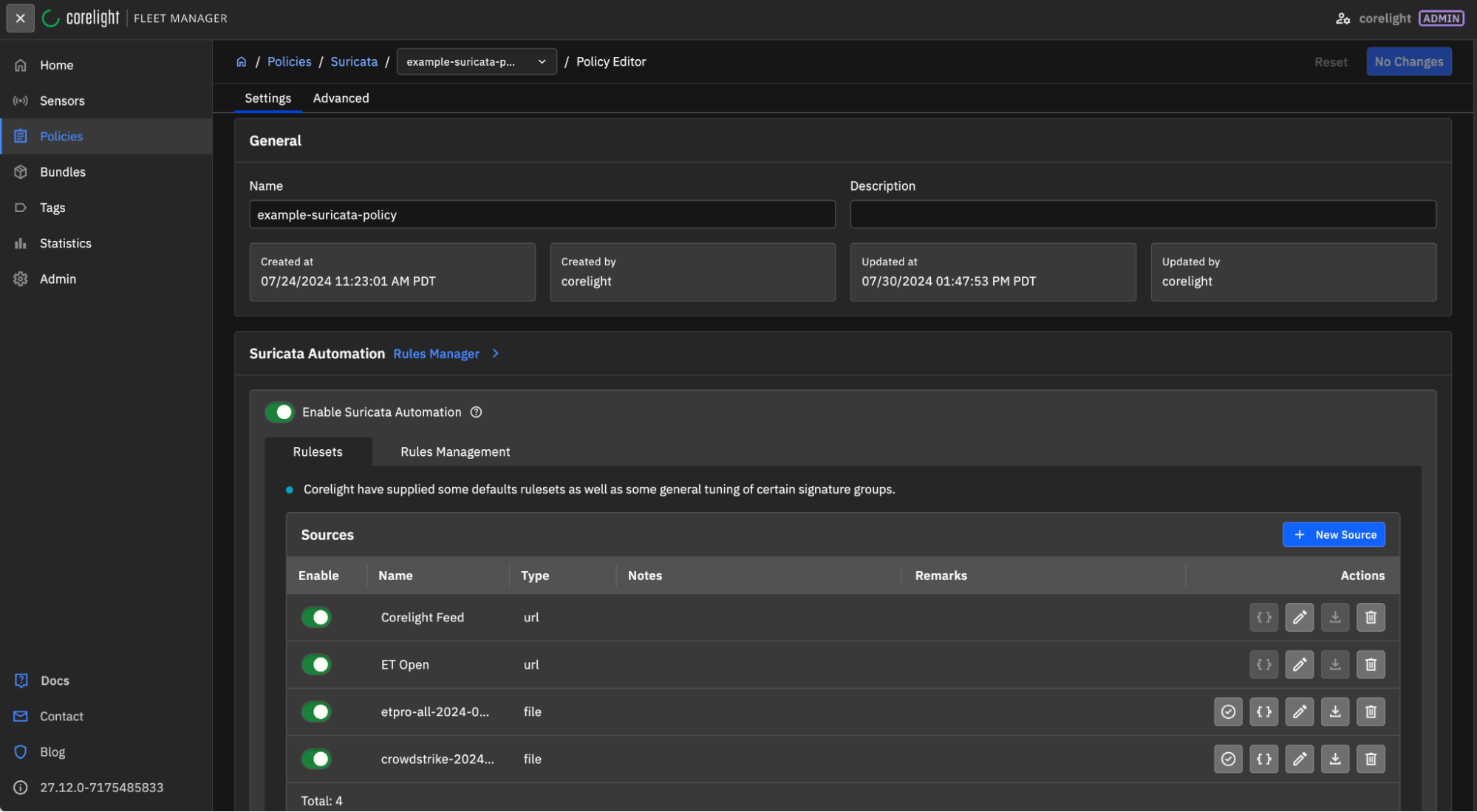
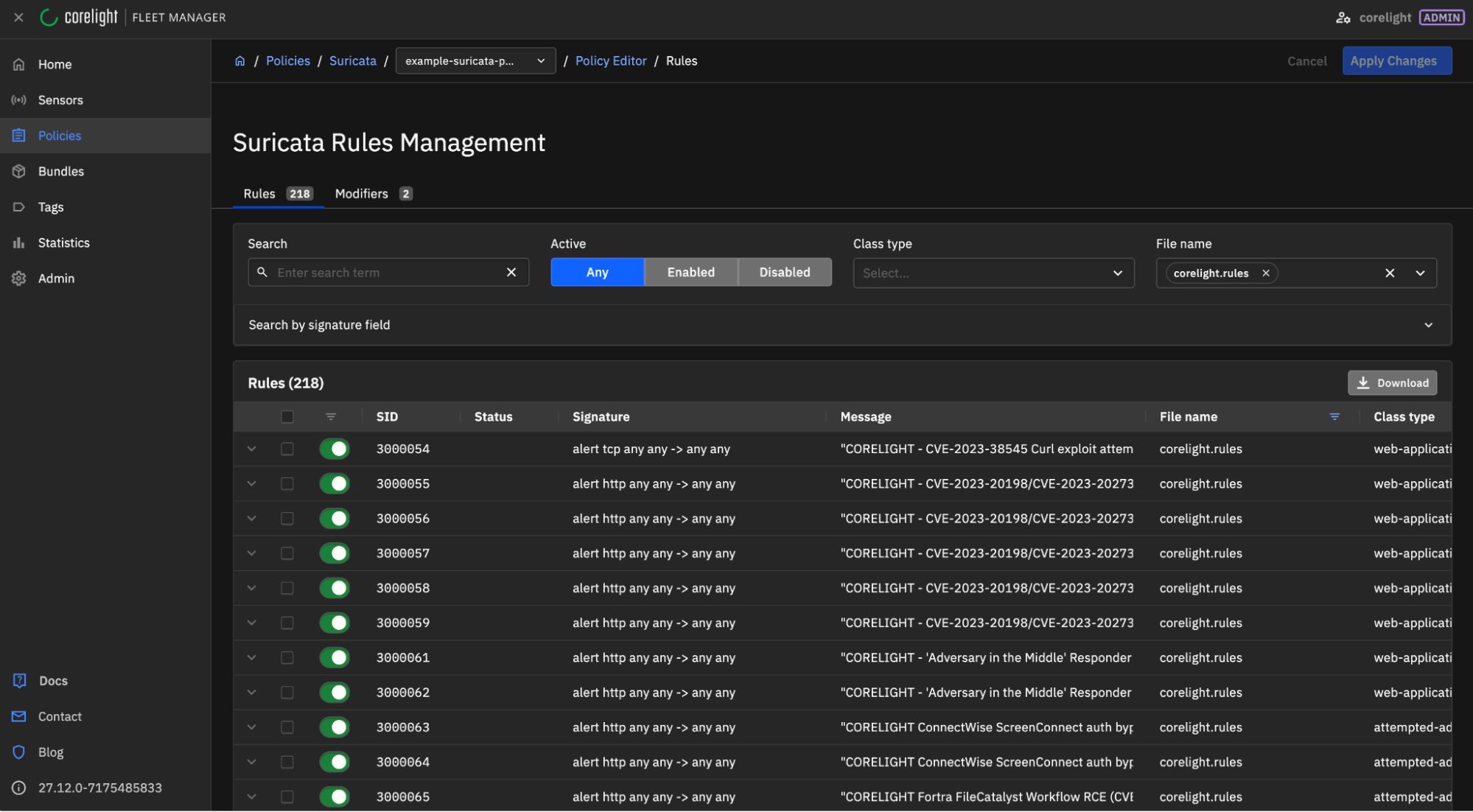
To confirm that the rules are being used, you can check the Suricata Rules editor and use the File Name search for “corelight.rules”:
Please visit this link in our Corelight Support portal , where you will find a section dedicated to explaining the rules management process, FAQs, and further details.
What’s new in this release?
Migration from CORELIGHT 3CORESec LATERAL -> CORELIGHT LATERAL Existing 3CORESec rules in sid range 2620186 - 2620554 have been copied to Corelight sid range 3000147 - 3000281. Please update any saved searches using the sid range 2620186 - 2620554, as they will be retired in 3 months.
92 new rules offering coverage exclusive to this ruleset.
New LATERAL coverage
"
3000061 - CORELIGHT LATERAL AiTM Responder HTTP server harvesting NTLM hashes after Local mDNS/LMMR poisoning (M1) https://attack.mitre.org/software/S0174/
\n
3000062 - CORELIGHT LATERAL AiTM Responder HTTP server harvesting NTLM hashes after Local mDNS/LMMR poisoning (M2) https://attack.mitre.org/software/S0174/
\n
3000083 - CORELIGHT LATERAL MSSQL Admin Role Check (IS_SRVROLEMEMBER)
\n
3000084 - CORELIGHT LATERAL CrackMapExec MSSQL Artifact 2.1 (sp_configure set)
\n
3000085 - CORELIGHT LATERAL CrackMapExec MSSQL Artifact 2.2 (sp_configure unset)
\n
3000086 - CORELIGHT LATERAL MSSQL xp_cmdshell Stored Procudure Successfully Enabled
\n
3000087 - CORELIGHT LATERAL CrackMapExec Style AMSI Bypass Observed
\n
3000088 - CORELIGHT LATERAL CrackMapExec MSSQL Artifact 3.0 (xp_cmdshell + downloadstring)
\n
3000089 - CORELIGHT LATERAL CrackMapExec MSSQL Artifact 3.1 (xp_cmdshell + downloadstring)
\n
3000090 - CORELIGHT LATERAL CrackMapExec MSSQL Artifact 3.2 (xp_cmdshell + downloadstring)
\n
3000091 - CORELIGHT LATERAL CrackMapExec MSSQL Ping Reply
\n
3000092 - CORELIGHT LATERAL impacket MSSQL Username Check
\n
3000093 - CORELIGHT LATERAL MSSQL sa Account Brute Force Attempt (UTF-8)
\n
3000094 - CORELIGHT LATERAL MSSQL Account Brute Force Attempt (UTF-8)
\n
3000095 - CORELIGHT LATERAL MSSQL sa Account Brute Force Attempt (UTF-16LE)
\n
3000096 - CORELIGHT LATERAL MSSQL Account Brute Force Attempt (UTF-16LE)
\n
3000097 - CORELIGHT LATERAL MSSQL Brute Force Attempt (squelda 1.0)
\n
3000098 - CORELIGHT LATERAL MSSQL Metasploit Style Blank Password Check (mssql_enum)
\n
3000099 - CORELIGHT LATERAL MSSQL Metasploit Style Command Execution (mssql_exec sp_oacreate)
\n
3000100 - CORELIGHT LATERAL MSSQL Attempted Command Execution (xp_cmdshell)
\n
3000101 - CORELIGHT LATERAL MSSQL Nmap NSE Client
\n
3000102 - CORELIGHT LATERAL Impacket smbexec Artifact in SMB (UTF16-LE __output in Create Request)
\n
3000103 - CORELIGHT LATERAL Impacket smbexec Artifact in SMB (ASCII __output in Create Request)
\n
3000104 - CORELIGHT LATERAL SMB CreateServiceW Suspicious Binary Path
\n
3000105 - CORELIGHT LATERAL Impacket dcomexec Remote Shell Artifacts
\n
3000106 - CORELIGHT LATERAL Covenant C2 Framework HTTP Beacon (default C2 profile)
\n
3000107 - CORELIGHT LATERAL Covenant C2 Framework HTTP Beacon Response (default C2 profile)
\n
3000108 - CORELIGHT LATERAL Covenant Grunt Implant Copied to Fileshare
\n
3000109 - CORELIGHT LATERAL Shellcode Launcher Artifacts in DCERPC
\n
3000110 - CORELIGHT LATERAL SMB Create iertutil.dll Possible DLL Hijacking
\n
3000111 - CORELIGHT LATERAL SMB Create wbemcomn.dll Possible DLL Hijacking
\n
3000112 - CORELIGHT LATERAL SMB CreateServiceA With SharpSC Artifacts
\n
3000131 - CORELIGHT LATERAL [ANY.RUN] Impacket SMB Server GUID
\n
3000135 - CORELIGHT LATERAL NTDS Database Export in SMB (ntds.dit filename)
\n
3000136 - CORELIGHT LATERAL NTDS Database Export in SMB (ESENT format artifacts)
\n
3000137 - CORELIGHT LATERAL NTDS Database Export in SMB (zip with export filenames)
"
New EXPLOIT coverage
"
3000044 - CORELIGHT EXPLOIT ServiceNow ACL bypass in Reporting functionality attempt (CVE-2022-43684)
\n
3000045 - CORELIGHT EXPLOIT Internet Connection Sharing (ICS) Remote Code Execution Attempt (CVE-2023-38148)
\n
3000046 - CORELIGHT EXPLOIT WS_FTP Server Remote Code Execution Attempt - POST method (CVE-2023-40044)
\n
3000047 - CORELIGHT EXPLOIT WS_FTP Server Remote Code Execution Attempt - GET method (CVE-2023-40044)
\n
3000048 - CORELIGHT EXPLOIT Citrix-Netscaler CVE M1 (CVE-2023-3519)
\n
3000049 - CORELIGHT EXPLOIT Citrix-Netscaler CVE M2 (CVE-2023-3519)
\n
3000050 - CORELIGHT EXPLOIT Citrix-Netscaler CVE M3 (CVE-2023-3519)
\n
3000051 - CORELIGHT EXPLOIT Citrix-Netscaler CVE M4 (CVE-2023-3519)
\n
3000052 - CORELIGHT EXPLOIT Citrix-Netscaler CVE M5 (CVE-2023-3519)
\n
3000053 - CORELIGHT EXPLOIT Curl exploit attempt in SOCKS5 - no alert just set flowbit (CVE-2023-38545)
\n
3000054 - CORELIGHT EXPLOIT Curl exploit attempt in SOCKS5 (CVE-2023-38545)
\n
3000055 - CORELIGHT EXPLOIT Cisco IOS XE implant connection attempt via logoutconfirm uri (CVE-2023-20198/CVE-2023-20273)
\n
3000056 - CORELIGHT EXPLOIT Cisco IOS XE implant connection attempt via Authorization header (CVE-2023-20198/CVE-2023-20273)
\n
3000057 - CORELIGHT EXPLOIT Cisco IOS XE implant connection attempt via exec command within POST body (CVE-2023-20198/CVE-2023-20273)
\n
3000059 - CORELIGHT EXPLOIT Cisco IOS XE implant DETECTED - exec command was successful (CVE-2023-20198/CVE-2023-20273)
\n
3000063 - CORELIGHT EXPLOIT ConnectWise ScreenConnect auth bypass attempt (CVE-2024-1709)
\n
3000064 - CORELIGHT EXPLOIT ConnectWise ScreenConnect auth bypass SUCCESSFUL (CVE-2024-1709)
\n
3000065 - CORELIGHT EXPLOIT Fortra FileCatalyst Workflow RCE attempt URL pattern 1 (CVE-2024-25153)
\n
3000066 - CORELIGHT EXPLOIT Fortra FileCatalyst Workflow RCE attempt URL pattern 2 (CVE-2024-25153)
\n
3000067 - CORELIGHT EXPLOIT Fortra FileCatalyst Workflow RCE attempt URL pattern 3 (CVE-2024-25153)
\n
3000068 - CORELIGHT EXPLOIT Fortra FileCatalyst Workflow RCE attempt URL pattern 4 (CVE-2024-25153)
\n
3000069 - CORELIGHT EXPLOIT FortiGate SSL VPN RCE exploit attempt (CVE-2024-21762)
\n
3000073 - CORELIGHT EXPLOIT ColdFusion exploit attempt at retrieving a uuid - stage 1 of the attack (CVE-2024-20767)
\n
3000074 - CORELIGHT EXPLOIT ColdFusion exploit attempt at file read - stage 2 of the attack (CVE-2024-20767)
\n
3000080 - CORELIGHT EXPLOIT Hytec HWL-2511-SS Remote Command Injection Attempt (CVE-2022-36553)
\n
3000082 - CORELIGHT EXPLOIT Apache OFBiz Deserialization Remote Code Execution Attempt (CVE-2021-26295)
\n
3000119 - CORELIGHT EXPLOIT Possible QEMU Tunnel
\n
3000133 - CORELIGHT EXPLOIT Axis Camera RCE Attempt (CVE-2018-10660)
\n
3000138 - CORELIGHT EXPLOIT D-Link NAS Command Injection Attempt (CVE-2024-3273)
\n
3000139 - CORELIGHT EXPLOIT D-Link NAS Possibly Successful Command Injection Attempt (CVE-2024-3273)
\n
3000282 - CORELIGHT EXPLOIT Progress MOVEit Transfer authentication bypass - First stage of attack - HTTP POST of a SSH public key (CVE-2024-5806)
\n
3000283 - CORELIGHT EXPLOIT Progress MOVEit Transfer authentication bypass - Second stage of attack - SSH connection (CVE-2024-5806)
"
New MALWARE coverage
"
3000070 - CORELIGHT MALWARE AsyncRAT Style TLS Certificate
\n
3000071 - CORELIGHT MALWARE AsyncRAT Variant Style TLS Certificate
\n
3000072 - CORELIGHT MALWARE QuasarRAT TLS Certificate
\n
3000075 - CORELIGHT MALWARE STRRAT C2 Request
\n
3000076 - CORELIGHT MALWARE STRRAT C2 Response
\n
3000077 - CORELIGHT MALWARE STRRAT C2 Infected Computer License Check
\n
3000078 - CORELIGHT MALWARE STRRAT C2 External IP Check Via ip-api.com
\n
3000079 - CORELIGHT MALWARE STRRAT JAR File Inbound
\n
3000081 - CORELIGHT MALWARE xmrigCC Donation Mining Pool Domain Lookup
\n
3000118 - CORELIGHT MALWARE Kryptina Ransomware Encryptor Download Attempt
\n
3000132 - CORELIGHT MALWARE dnscat2 Static Tagged DNS Tunnel
\n
3000134 - CORELIGHT MALWARE Known Malicious User-Agent Inbound (Volt Typhoon)
\n
3000140 - CORELIGHT MALWARE Amadey Malware Check-In via HTTP M1
\n
3000141 - CORELIGHT MALWARE Amadey Malware Check-In via HTTP M2
\n
3000142 - CORELIGHT MALWARE Amadey Style Module Download (cred64.dll)
\n
3000143 - CORELIGHT MALWARE Amadey Style Module Download (clip64.dll)
\n
3000144 - CORELIGHT MALWARE Amadey Malware Check-In via SOAP
\n
3000145 - CORELIGHT MALWARE Amadey Malware Check-In Response via SOAP
\n
3000146 - CORELIGHT MALWARE Covenant C2 TLS Certificate Artifacts
\n
3000284 - CORELIGHT MALWARE Mythic C2 POST content (M1)
\n
3000285 - CORELIGHT MALWARE Mythic C2 POST content (M2)
\n
3000286 - CORELIGHT MALWARE Mythic C2 Websocket content (M3)
\n
3000287 - CORELIGHT MALWARE Mythic C2 Binary (M4 noalert)
\n
3000288 - CORELIGHT MALWARE Mythic C2 Binary (M4)
"
In recent months STRRAT has become one of the top malware families submitted to Any.Run. Here's how to detect it.
I am excited to announce Corelight’s v21 release, which delivers dozens of powerful C2 detections, extends analyst visibility around RDP connections,...
In this blog we aim to provide a little insight into part of the lifecycle of Corelight Lab’s response to a critical HTTP vulnerability.
Be the first to know about new B2B SaaS Marketing insights to build or refine your marketing function with the tools and knowledge of today’s industry.