Announcing The New Corelight for Splunk App
The Corelight for Splunk app is now available! Using the new app you can now monitor the health and performance of Corelight Sensors in Splunk and...
Want to use Zeek (formerly Bro) network data in Splunk ES, but don’t know how to start or where to look?
Need to quickly narrow down Zeek logs from a mountain, to a hill, to a handful?
Want to avoid hours of work mapping Corelight key-value pairs for ingest?
Our recently updated Corelight App for Splunk may be just what you’re looking for. It accelerates SOC workflows by providing guided threat hunting workflows using dashboards and filters that enable analysts to quickly narrow down and pivot across Zeek logs. It’s also a great demonstration of how Zeek data sent into the Splunk platform can be leveraged to find encrypted malicious traffic, DNS exfiltration, hidden malware and other network risks.
In addition we’ve released an updated technology add-on (TA) that automatically normalizes Corelight security data for easier ingest into the Splunk platform. The TA can be used standalone or in conjunction with the new app — a tool worth checking out if you’re a Corelight + Splunk shop.
The Corelight App for Splunk works with Corelight sensors as well as Zeek. The app requires the above mentioned TA for Corelight data, or the Splunk Add-on for Zeek data. You can download the app and either TA for free on Splunkbase.
To learn more about Corelight’s integration with Splunk software and how it helps incident responders and threat hunters work faster and more effectively, please read our joint solution data sheet, watch our webinar on Threat Hunting in Splunk with Zeek or check out the screenshots of the app below:
Detections dashboard
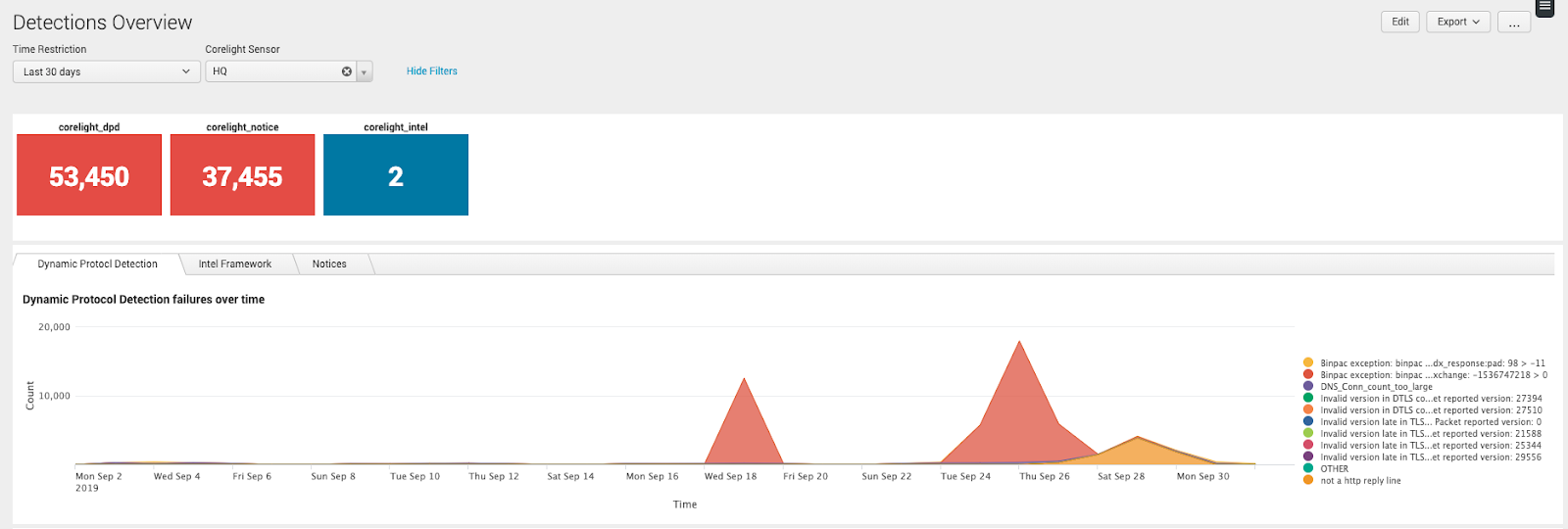
Find and respond to off-port protocol usage, IOC matches, and other potentially interesting events.
Intel workflow
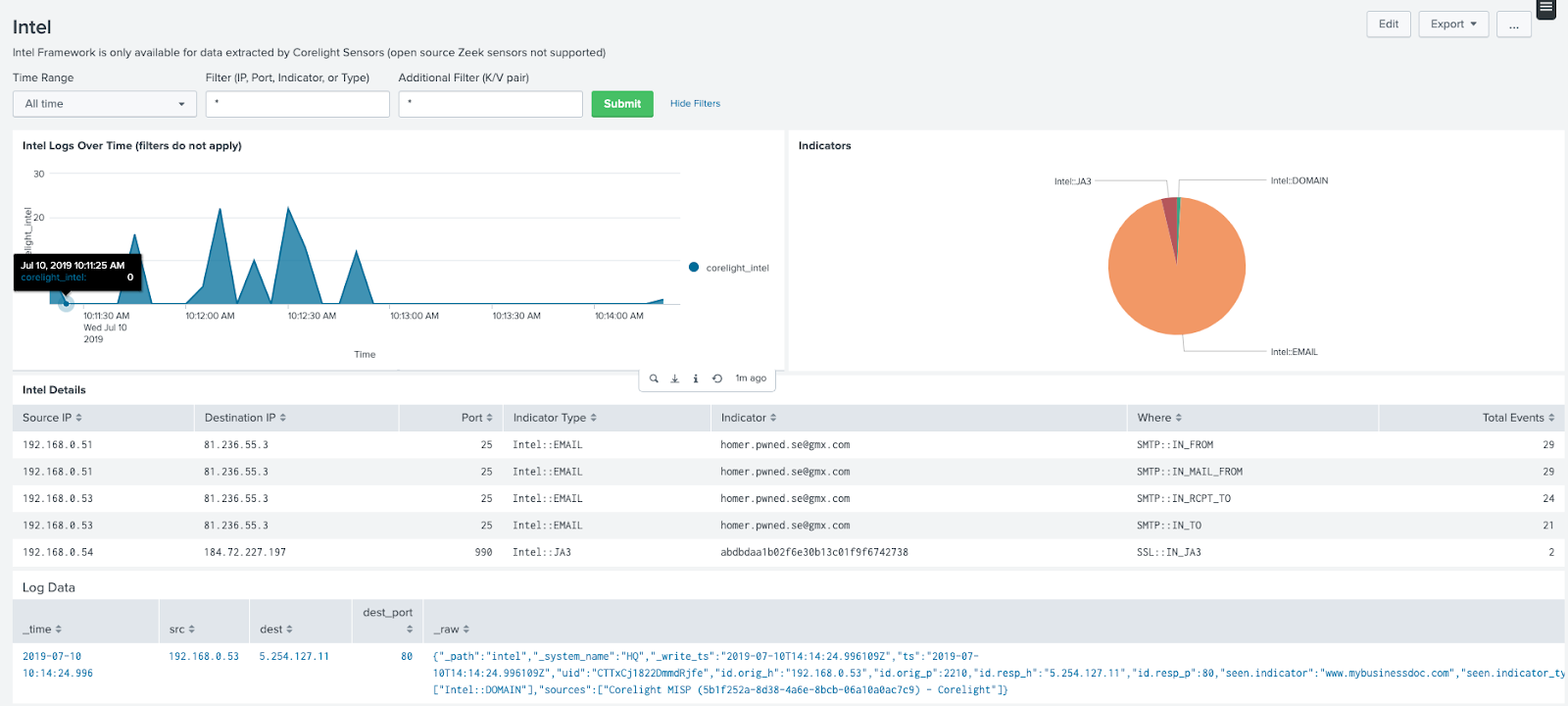
Find IOCs from external sources matched in network traffic.
Notices workflow
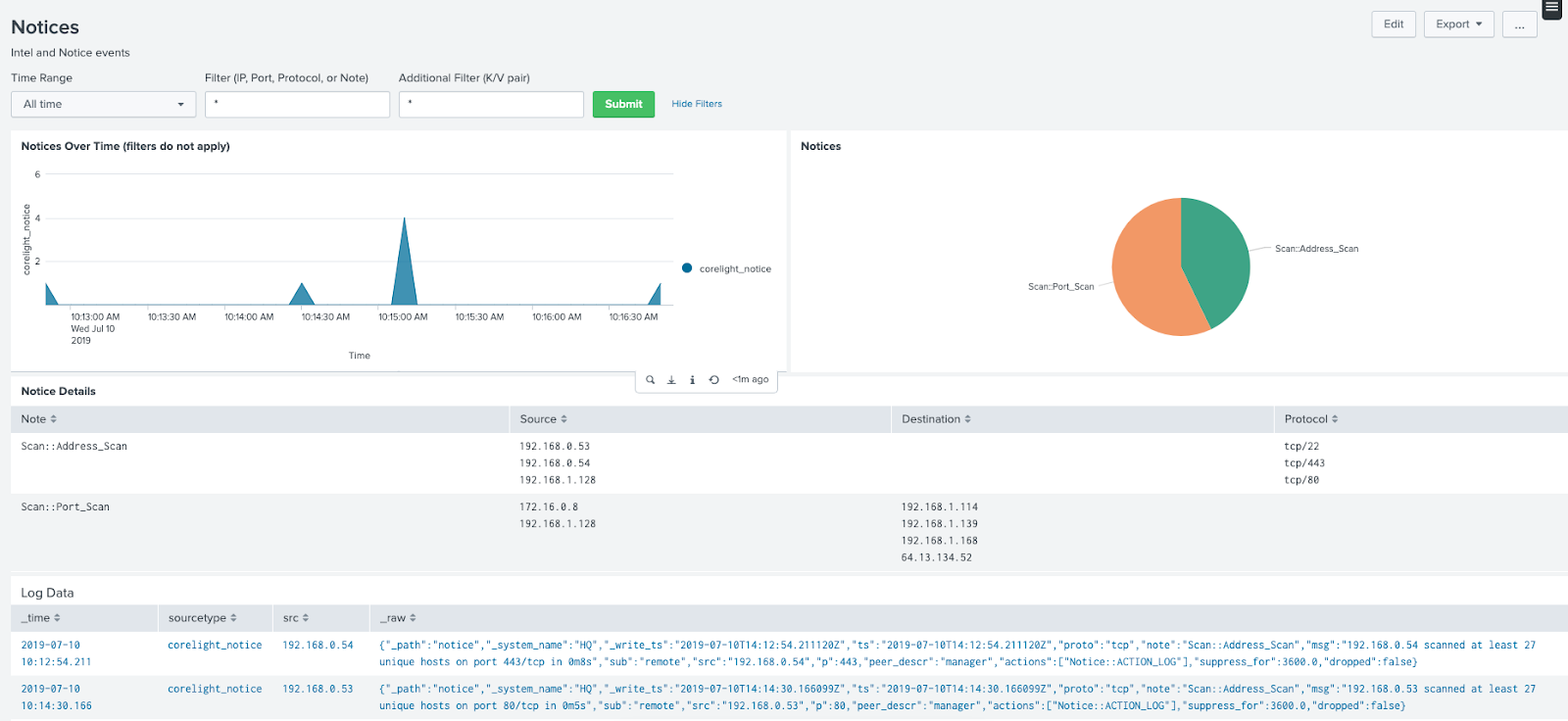
See situations flagged by the Notice policy for further investigation.
Log hunting workflow
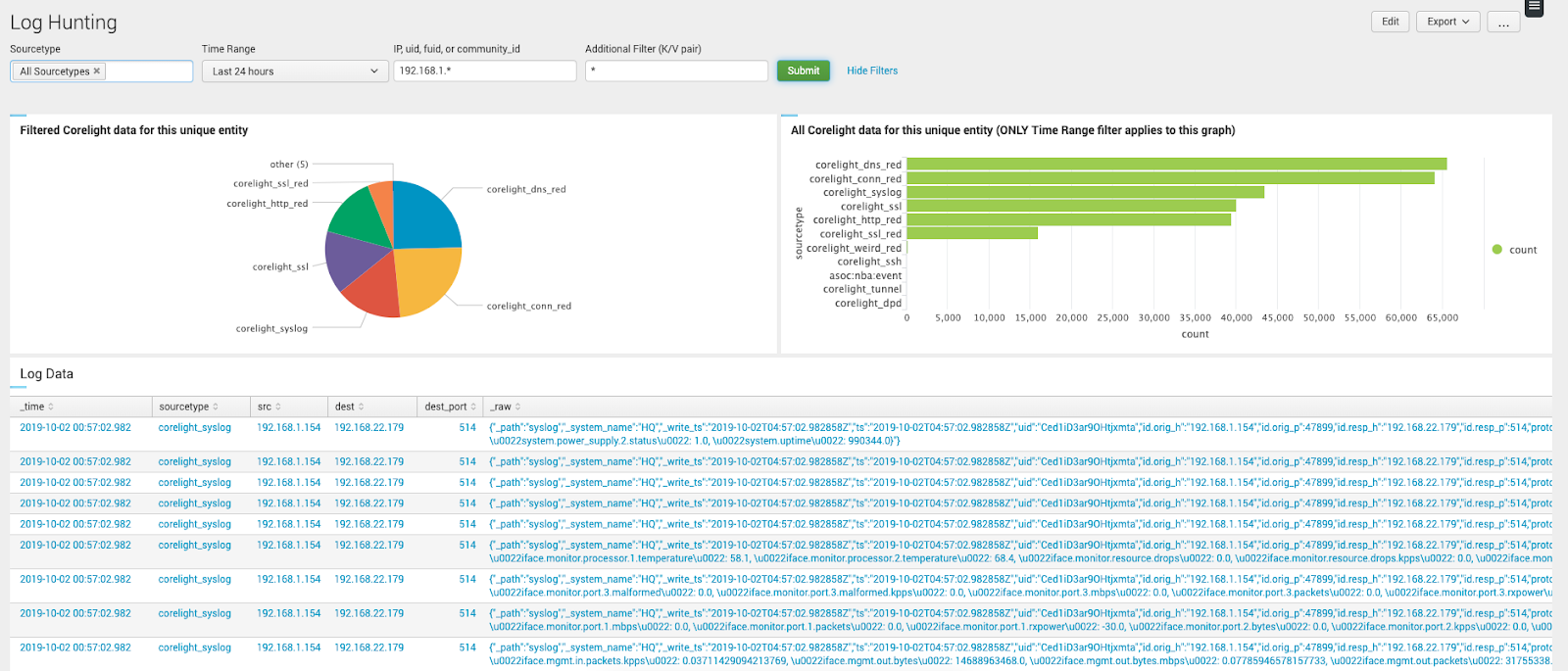
Accelerate your hunt by narrowing down many logs to only the logs that matter.
DNS dashboard
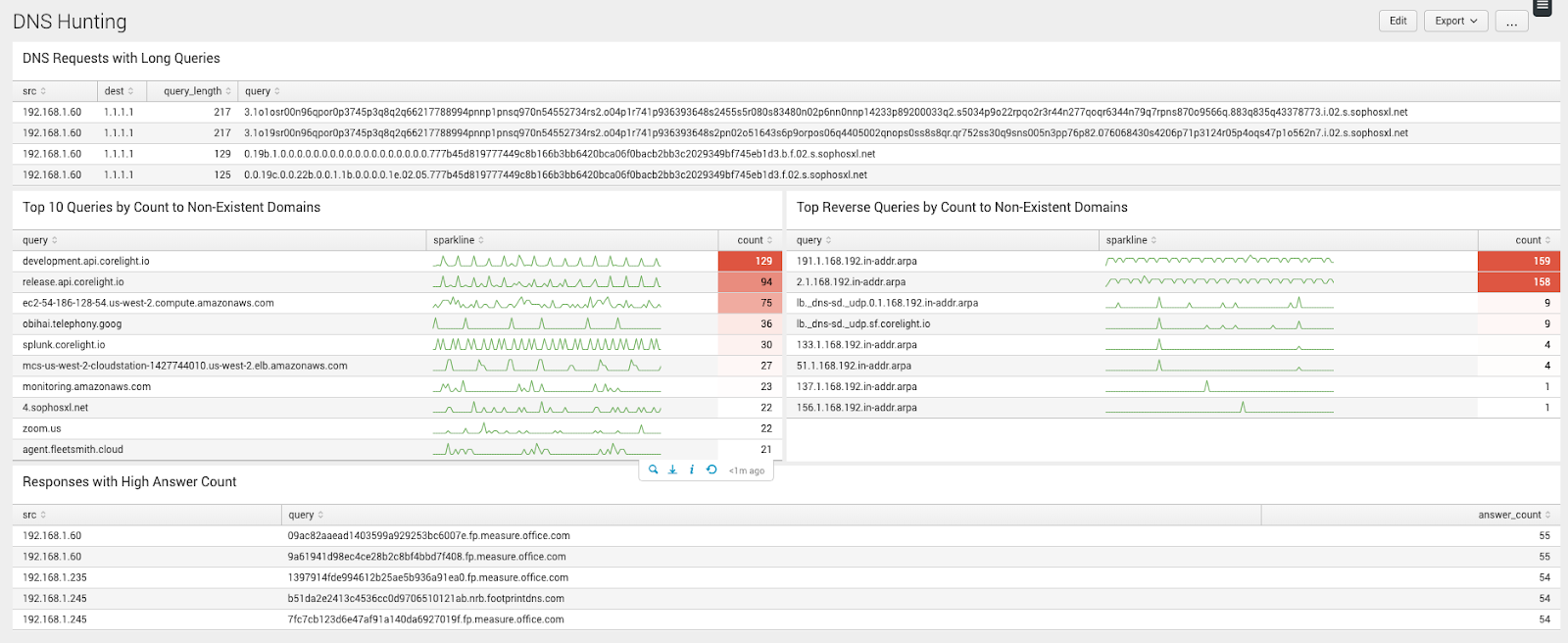
Detect DNS exfiltration by spotting queries to non-existent domains and high connection counts.
Corelight egress monitor
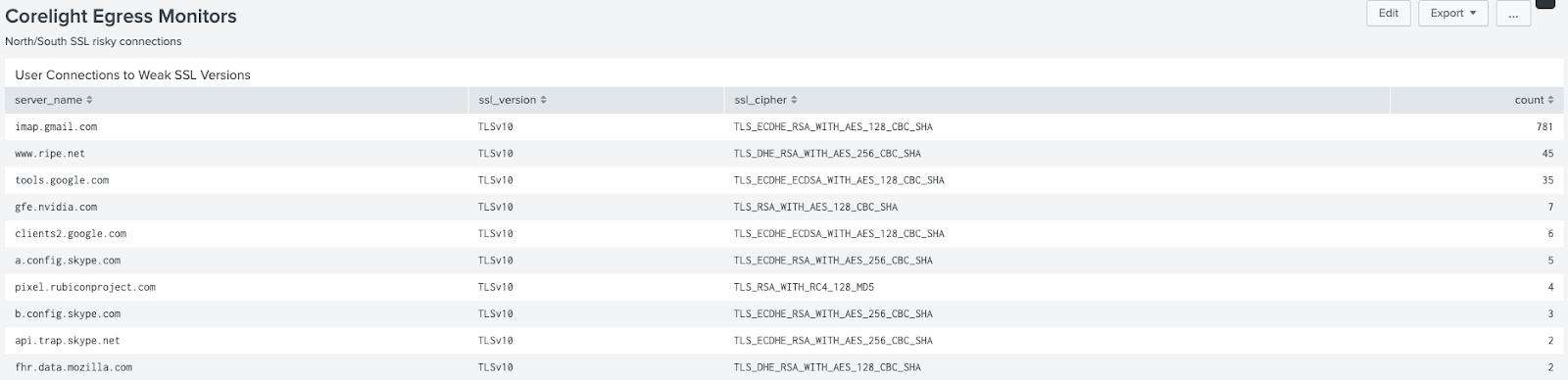
Find risky North/South user connections to weak SSL versions.
Ed Smith - Senior Product Marketing Manager, Corelight
The Corelight for Splunk app is now available! Using the new app you can now monitor the health and performance of Corelight Sensors in Splunk and...
Download the Corelight App for Splunk and see how easy it is to get Corelight data into Splunk.
Learn about the benefits of Corelight DNS logs, and how Splunk Enterprise Security can reach a new level of functionality through integration with...