WHY EVIDENCE-BASED SECURITY
Elite defenders recognize that alerts can—and will—be missed. They know that an evidence-first strategy is their best opportunity to catch advanced adversaries in the act.
RISK THRIVES IN UNCERTAINTY. THE BEST DEFENSE IS EVIDENCE.
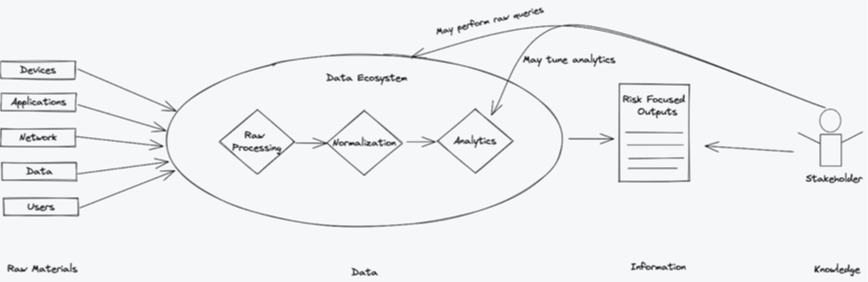
Cyber risk is an inevitable part of any organization's security posture. Uncertainty makes this risk even harder to deal with. That's why the most sophisticated defenders adopt an evidence-based approach to network security. This strategy removes uncertainty so they can make the right decision in critical moments—when an alert comes in, when a major attack is detected, or when they're remediating a breach—so they can deal with risk from the most informed position.
HOW TO DEFEND WITH EVIDENCE

COMPLETE VISIBILITY
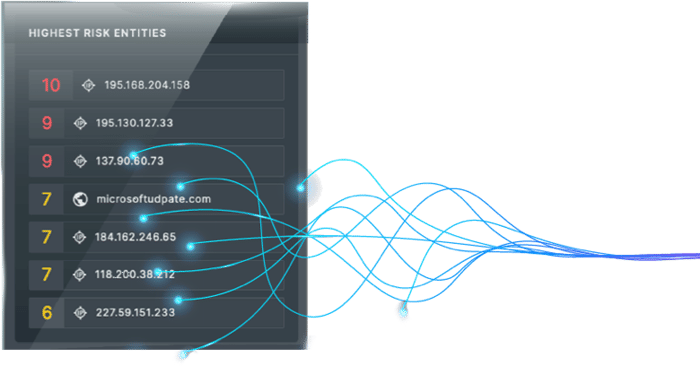
NEXT LEVEL ANALYTICS
![]()
FASTER INVESTIGATION
EXPERT HUNTING
The evidence bank
Evidence is the currency cyber defenders use to pay down security debt, balancing the value equation between adversaries and the enterprise. Defenders can use evidence proactively, identifying and protecting structural risks within our zone of control. Read more on our blog.