Thousands of organizations around the world depend on the Zeek Network Security Monitor to illuminate and secure their networks, including:




Security possibilities limited only by your imagination.
What if you could see every significant event on the wire and automate analysis and alerting tasks against any behaviors or indicator of compromise you wanted? With Zeek, you can do amazing things like:
- Identify Cyrillic keyboard usage in your environment
- Easily investigate and document unauthorized SMB file access events
- Detect cryptocurrency mining traffic
- And much, much more….




Case StudyFind out why Zeek is an unrivaled threat hunting tool.
A law firm purchased Corelight to make Zeek deployment easy, and used their newfound network visibility to unlock new threat hunting capabilities.

Join the data-first revolution in network security design.
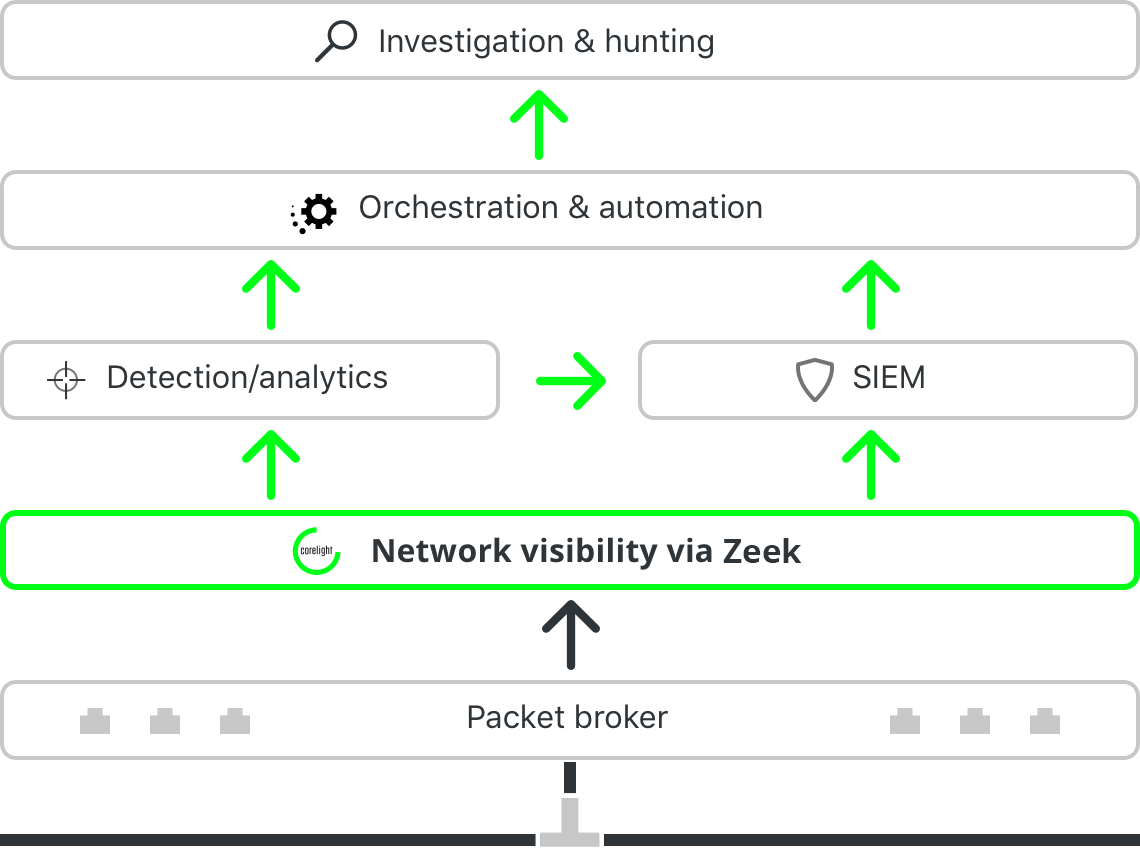
Leading security organizations use Zeek as the foundational layer in a network architecture that provides complete, actionable network visibility that can be deployed in any network environment and centralizes data in a common repository (e.g., a SIEM).
Compared to network architectures where visibility is limited and decentralized, this data-first design pattern can dramatically accelerate security operations and analytics. Learn how.
Our family of sensors simplify deploying Zeek at any scale.
The features you wish open-source Zeek had.



- Simple 15 minute, plug-and-play deployments with intuitive web interface for configuration and sensor monitoring
- Out-of-the-box integration with your favorite tools, like Splunk, Elastic, Kafka and more...
- Activate Corelight-verified Zeek packages with one click for additional traffic insights, like cryptocurrency mining activity alerts
- Easily filter out unneeded Zeek logs to control traffic volumes to your SIEM







