Leveraging map-reduce and LLMs for enhanced cybersecurity network detection
Learn how Map-Reduce and LLMs can be used to efficiently analyze huge datasets and improve threat hunting, incident response, and forensic analysis.
Welcome to the latest hunt from Corelight Labs! This blog continues our tradition of analyzing trending TTPs on Any.Run and writing detectors for them.
This month’s post covers a post-exploitation tactic abusing NetSupport Manager. NetSupport Manager, often used for benign purposes, provides system monitoring and remote access for corporate technical support. Because of these capabilities and its legitimate usage, NetSupport Manager is also an attractive application for post-exploitation activities, a well-documented trend (ref). This behavior was first identified in 2016, but has become especially popular in the latter half of 2023 and early 2024. Recently, analysts have identified usage of the tool by infostealer and ransomware groups such as FIN7 (ref) and Black Basta (ref).
Corelight Labs developed Zeek logic to help detect malicious use of NetSupport. Through partner networks in our Polaris Program, we used this logic to find multiple infections occurring in 2024 with zero false-positives, despite the large size and complexity of the networks. We’ve released an open-source Zeek script to detect these signatures at https://github.com/corelight/zeek-netsupport-detector. Zeek users can install this package using zkg.
Typical NetSupport Manager behavior consists of the client exchanging commands with NetSupport Manager server over HTTP. The client polls the server for new commands, to which the server responds with an encrypted command to be executed by the client (Figure 1). When this traffic occurs in-the-clear, we can observe the client’s typical heartbeat behavior in an HTTP stream:
Figure 1: Two sequential client-server interactions facilitating data exchange to a known info-stealer (ref). The first request polls for new commands, to which the server responds with an encrypted command. The client then continues the exchange of data over this encrypted channel.

Our primary detection signature searches for the ENCD command in the HTTP request/response body. While this is a core feature of NetSupport Manager, we found that `CMD=ENCD` (encrypted command) over cleartext HTTP can be extremely rare––in eight months of data on multiple Polaris networks, we did not find any evidence of benign, clear-text ENCD commands, despite some networks having benign usage of the NetSupport Manager. In practice, legitimate NetSupport Manager instances are well-configured to enforce HTTPS while many malicious NetSupport Manager instances rely on cleartext HTTP. As a result, a client sending the POLL command over HTTP will either result in an error or will be redirected to HTTPS. In either case, the cleartext response will not contain CMD=ENCD. We found that in a typical infection, systems repeatedly reach out to the NetSupport Server across hours or days, usually in bursts.
This signature can be detected as a regex pattern in Zeek with the Zeek Signature Framework. The following signature detects a newline-separated `CMD=ENCD` in TCP streams:
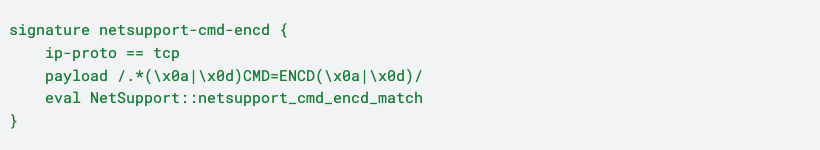
The event fired by this signature can be handled by a Zeek script, generating a “NetSupport::C2_Traffic_Observed_CMD_ENCD” notice (ref):
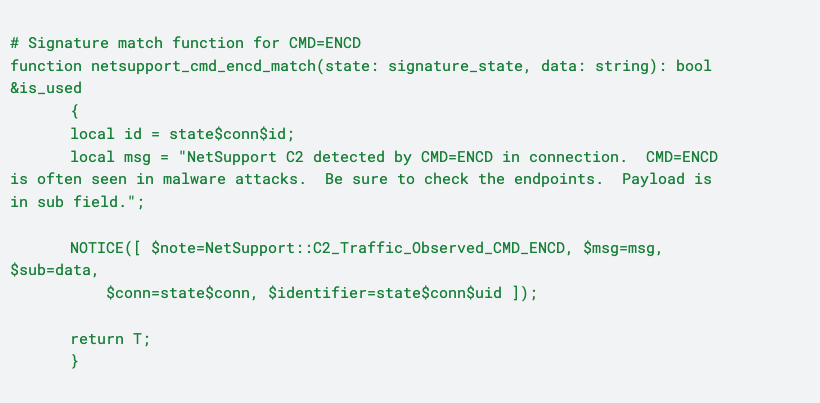
We also found that in general, malicious NetSupport Manager servers observed on Any.run and our Polaris sites were located in eastern European countries, which can serve as an additional indicator. This information is available in Zeek with some additional configuration (see the docs) and can aid in hunting for both NetSupport Manager usage and other threats.
While all the malware samples we reviewed in Any.Run used the ENCD command, it is possible malware could not use the ENCD command and we want to be ready for that. We wrote an additional signature to detect the NetSupport POLL command so that the analyst could review those hits for potential malware, since NetSupport is used so often maliciously:
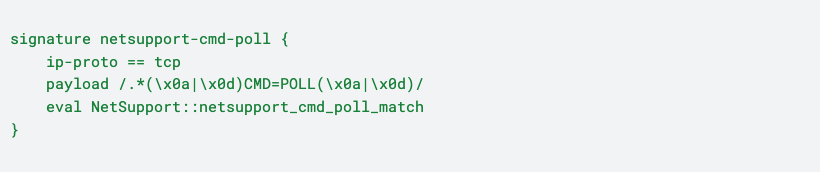
When this signature hits, a “NetSupport::C2_Traffic_Observed_CMD_POLL” notice is generated:
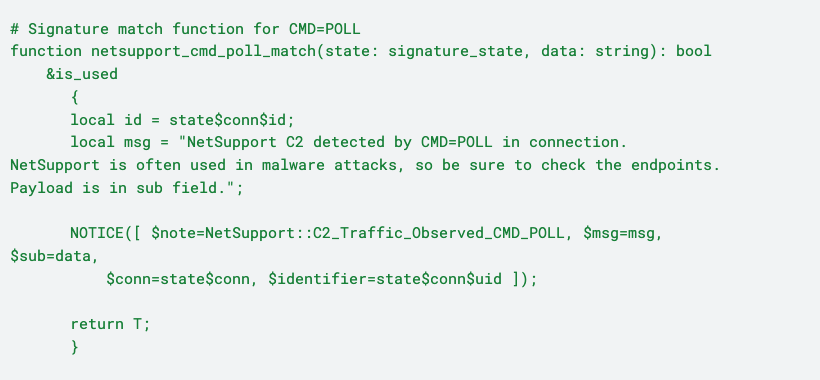
In addition, we added logic to look for “NetSupport” in either the “USER-AGENT” or “SERVER” HTTP headers. If “NetSupport” is found, a “NetSupport::C2_Traffic_Observed_HTTP_Headers” notice is generated:
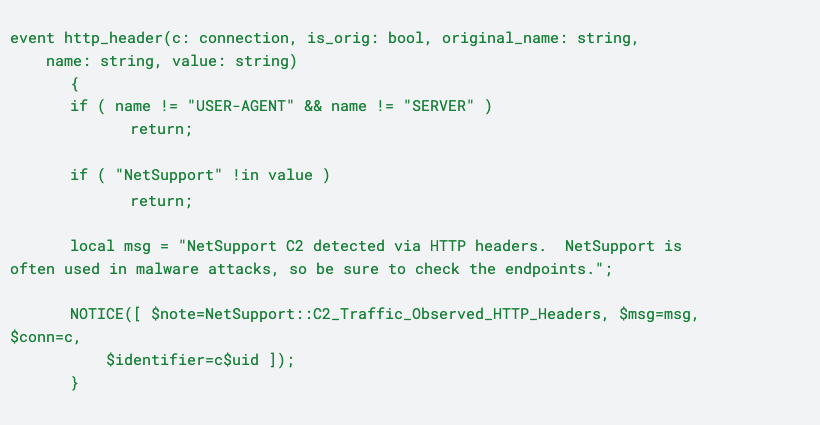
Putting all of the logic together and running it on the Any.Run PCAP, you will see the following notices:
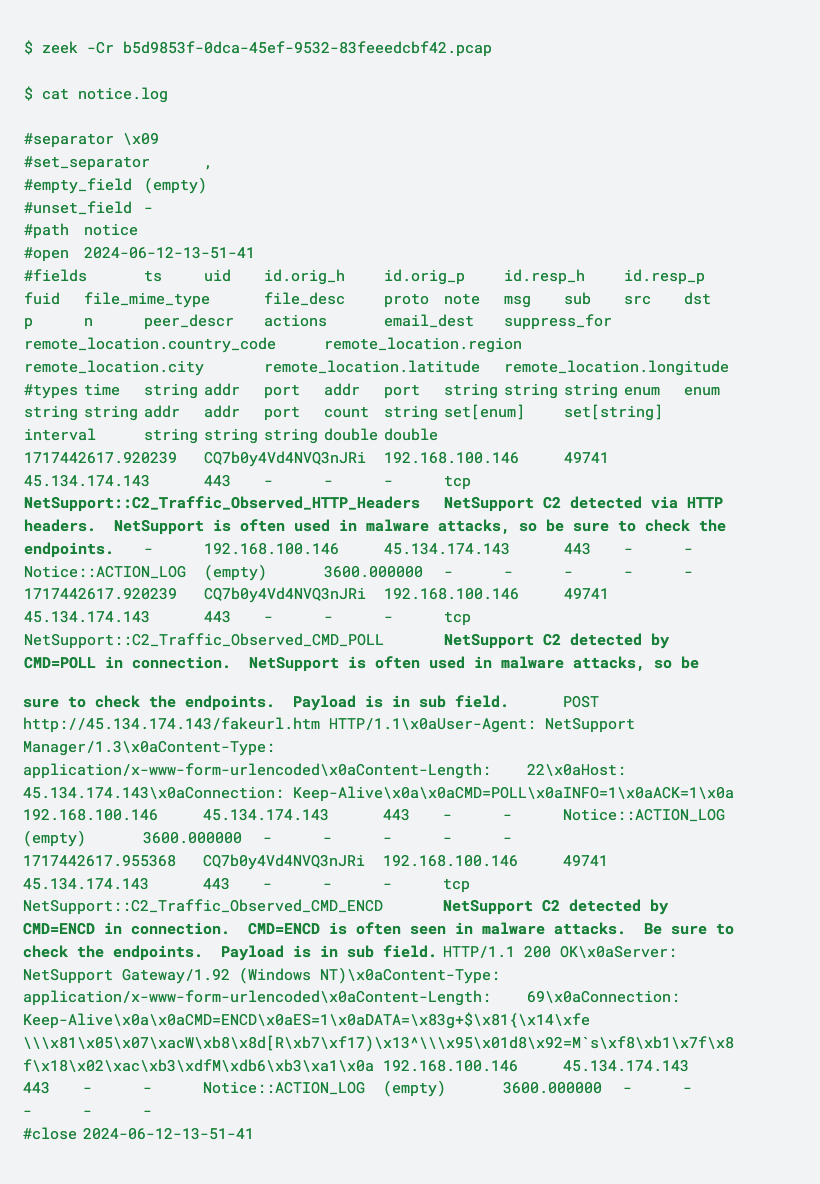
You see above that all three notices fire on the example malicious NetSupport PCAP. Enabling this logic in our Polaris partner networks increased the notices, but it was a manageable amount. We were able to use a combination of these three notices to help give us context around the connections they flagged. Do note that looking for the second (POLL) signature and HTTP headers will flag connections that are legitimate NetSupport too, so be sure to evaluate the connections in detail to determine their actual threat level.
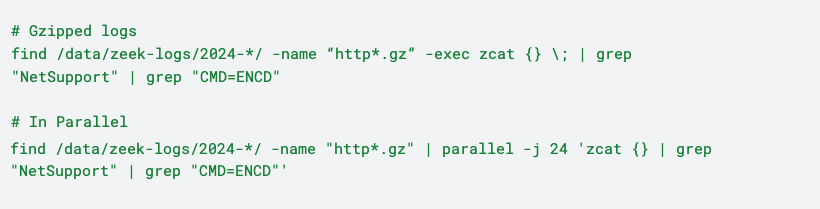
In the process of building this specialized detector for NetSupport, Corelight’s open-source package to add HTTP POST bodies to http.log was instrumental in retroactive detections ( https://github.com/corelight/log-add-http-post-bodies). Given our signatures, this package enabled us to look back at months of historic logs to find additional infections. This can be implemented as an expression in a SIEM search or a grep against Zeek logs. For example, we used the following commands to search gzipped Zeek logs:
In this month’s blog, we’ve highlighted effective methods for detecting the malicious use of NetSupport Manager, leveraging clear-text HTTP traffic and the CMD=ENCDcommand as indicators. We demonstrated how simple it is to implement this detection using a Zeek signature, ensuring that defenders can quickly identify and respond to potential threats. For those who want to get hands-on, we’ve made the detection code available at https://github.com/corelight/zeek-netsupport-detector. You can install this logic with the zkg package manager.
We also recommend checking out Corelight’s C2 Collection, which covers known C2 toolkits and MITRE ATT&CK® C2 techniques and is based on Zeek metadata, for more than 50 unique insights and detections that illuminate command and control activity and help defenders find novel attacks.
Happy Hunting!
Corelight Labs
Learn how Map-Reduce and LLMs can be used to efficiently analyze huge datasets and improve threat hunting, incident response, and forensic analysis.
Detect Quasar RAT malware with Corelight’s open-source Zeek script, leveraging Quasar’s default TLS configuration.
Learn how you can use Zeek to detect this level of cunning evasion tactics in your own retrospective hunts and forensic investigations.