Streamlining security investigations with real-time enrichment of Corelight Open NDR and SentinelOne Singularity
Corelight’s integration with SentinelOne is a game-changer for security teams looking to stay ahead of evolving cyber threats.
One of the major causes of alert fatigue for SOCs is a class of alerts that fall in between false positives and useful detections: when an actual attack has been launched, and the detection is working correctly, but the host on the receiving end is not vulnerable, guaranteeing that the attack will fail. Whether that’s because it’s a total mismatch - think of a vulnerability in IIS on Windows Server being used against an Apache box on Linux - or because defenders have been vigilant and got their systems patched, these alerts are ultimately just noise that slows down the processing of alert queues. On the other hand, if you can confirm that the system being attacked was in fact vulnerable to the bug being exploited, that investigation suddenly rockets to the top of your priority list.
That prioritization is exactly what Corelight’s new integration with Tenable is designed to do. We poll your enterprise’s Tenable APIs to retrieve data on vulnerabilities known to be present in the environment, and then load that information through the Zeek® input framework. When a Suricata alert that contains a CVE reference is raised, we cross-reference into that Tenable data to determine if the vulnerability in question is present on the system being attacked - and if so, add a field to the alert to highlight that fact:
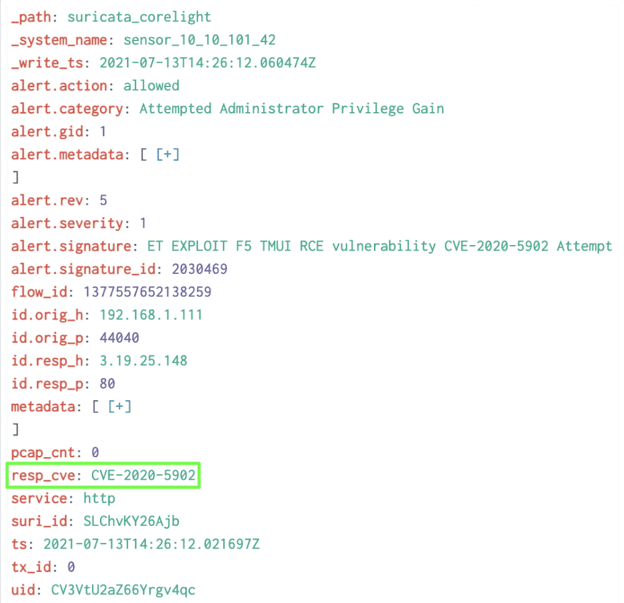
The field in question will be either resp_cve or orig_cve, depending on whether the server or the client of the session in question is the one known to be vulnerable. Since these fields will only ever be present on confirmed-vulnerable situations, a simple query for their presence in your alert queue will yield a prioritized list of alerts for your SOC to tackle first.
Enabling the integration requires no special setup on the Tenable side beyond enabling API keys with read access to vulnerability details, and is configured in a few lines of option setup on the Corelight side to allow it to run as a recurring background job. Note that we currently only support Tenable.sc, though work is in progress to support Tenable.io as well.
While this correlation could certainly also be done directly in-SIEM if both data sets are present there, we here at Corelight understand how many SIEM deployments are already overworked (much like the people that work with them) and/or overly complex, so we’re working to make it easier for SOCs to get their hands on the right data. If you’re an existing or a potential customer and want to check this integration out, please reach out to us to get the ball rolling - and if you have other things you would like to see us to do make life in the SOC easier, we would love to hear from you.
By Alex Kirk, Manager Global Security Consultants, Corelight
Corelight’s integration with SentinelOne is a game-changer for security teams looking to stay ahead of evolving cyber threats.
Reduce time to triage by up to 50% with Corelight's new Guided Triage capability.
The CrowdStrike + Corelight partnership lets customers incorporate threat intelligence into Corelight Sensors to generate alerts and network evidence.