
Reduce triage time by up to 50%
Corelight Investigator reduces the time required to conduct a thorough analysis, enabling analysts to make informed decisions faster. We simplify network complexity for analysts by delivering prioritized alerts, automating workflows, and leveraging AI to explain the expert level data needed for triage in plain language while reducing SIEM ingest.
- Accelerate triage and incident response
- Reduce SIEM ingest (and cost)
- Increase detection coverage
- Consolidate tools and datasets
- Integrate with existing SOC tools
- Easy to deploy, scale, and customize
- Based on open, global standards


Accelerate incident response with Investigator
Investigator streamlines and accelerates analyst workflows. Prioritized alerts direct analysts to a single-page triage experience, enriched with simplified explanations of pre-correlated data, powered by AI. Analysts are a click away from raw data including logs and PCAP for deeper analysis.
- AI explainers and summarizations
- Interactive visual timeline
- Triage history
- Quick host isolation and firewall blocking.
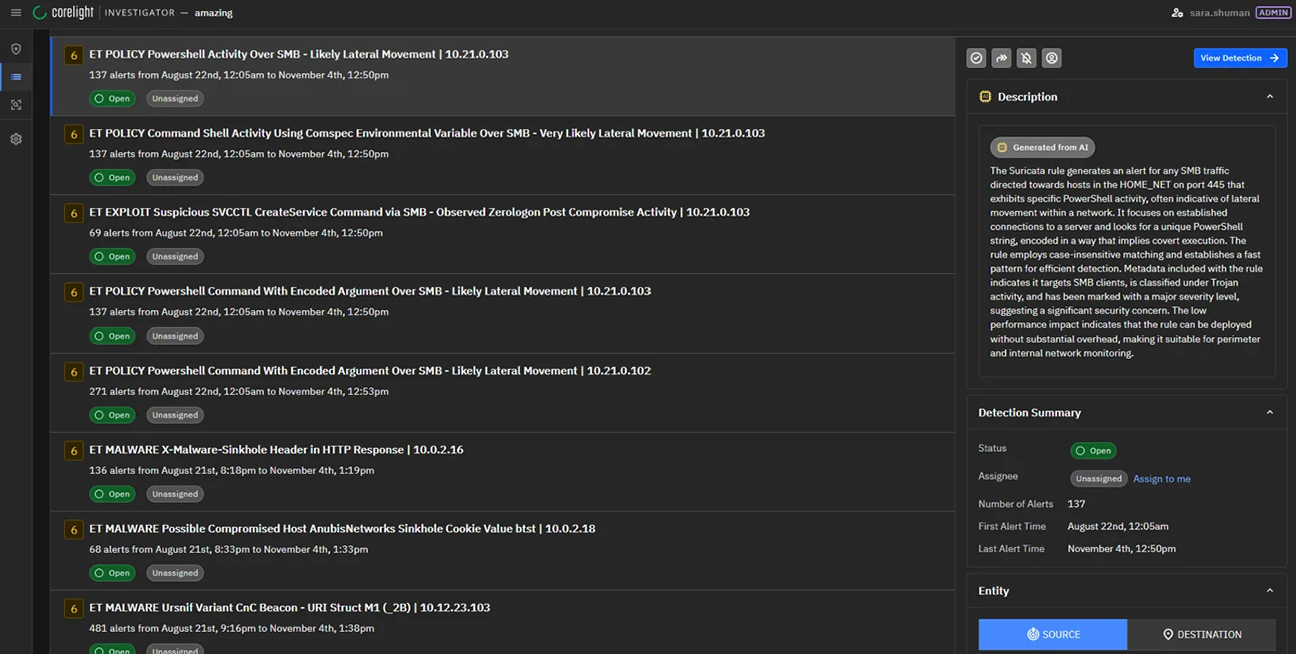
Expand detection coverage with Investigator
Investigator enables SOC teams to disrupt attacks by delivering the broadest range of detection capabilities and the ability to customize and tune based on your team’s requirements.
- Transparent AI/ML models
- Behavioral, signature, threat intel and queries
- Comprehensive MITRE ATT&CK approaches to uncover 80+ techniques, with deep visibility into adversary methods used for Defense Evasion, Credential Access, Discovery, and Command and Control.
- Seamlessly pivot from high-confidence detections to enforcement actions, ensuring rapid containment and minimizing lateral movement.
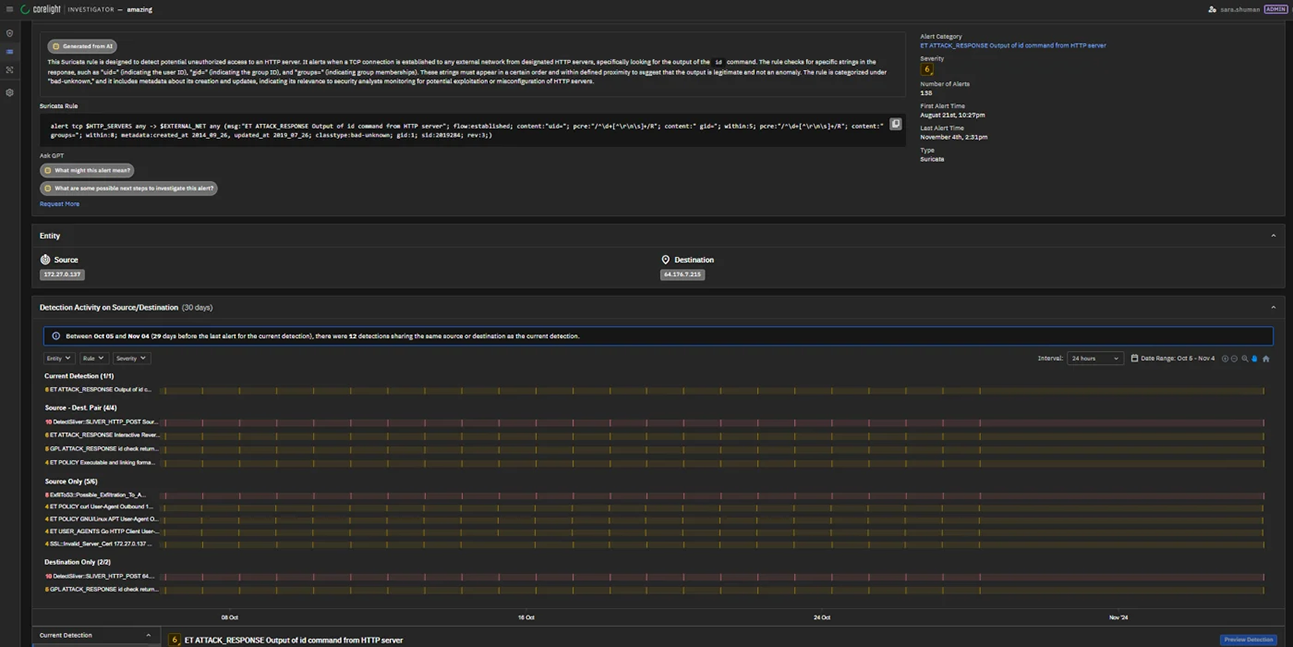
Increase SOC efficiency with Investigator
Investigator empowers analysts to make informed decisions quickly by capturing all the critical data needed for comprehensive threat analysis. Automated workflows, AI-explainers, and triage history help address skill gaps and analyst shortages.
- Toolset and dataset consolidation
- Single-screen triage
- Out-of-the-box and customizable dashboards
- 1-click host isolation and firewall policy enforcement.
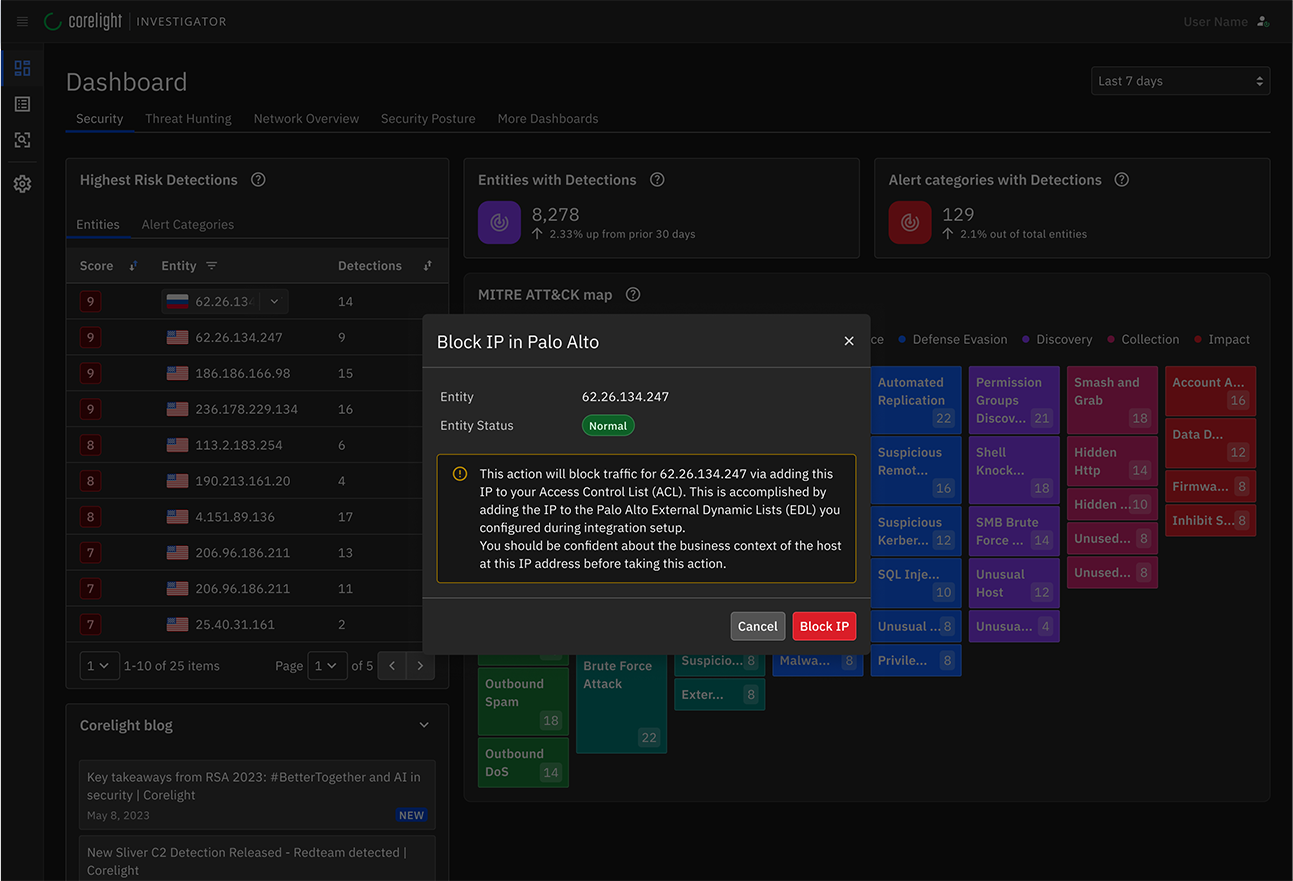
Enhanced response capabilities with Investigator
Investigator empowers analysts to respond swiftly by providing response actions directly from the triage interface. With a single click, analysts can quickly isolate compromised hosts and enforce network policy changes. These streamlined workflows allow SOC teams to reduce response times, limit lateral movement, and mitigate threats efficiently.
- Rapid detection to response built in the same UI
- One-click host isolation and containment
- Streamlined workflows that reduce response times
Compare Open to Closed NDR
This free ESG white paper explains the reasons to consider an open-source solution.
