Smart PCAP
Accelerate investigations with precise packet capture and one-click SIEM retrievals.
Store packets longer, find them faster
Corelight's Smart PCAP links Zeek® logs, detections, and extracted files to only the packets you need for investigations. Compared to full PCAP, it extends lookback windows by up to 10x—capturing only valuable data to save storage and accelerate workflows. Security teams can quickly pivot from alerts to PCAP files with one-click retrieval via SIEM or Investigator.
- Up to 10x longer lookback windows vs. full PCAP
- Powerful rules to capture only relevant packets
- Flexible storage: Corelight hardware, BYO, or cloud (S3)
- Seamless alert-to-PCAP retrieval via SIEM or Investigator

How it works
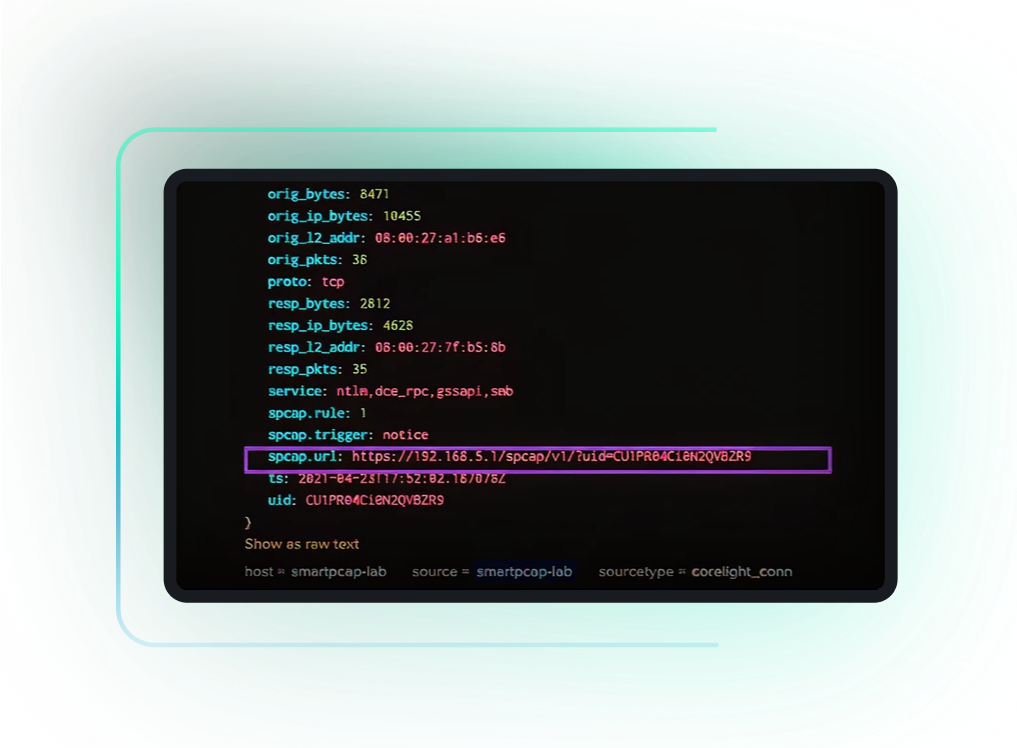
With Corelight Sensors in place, you can configure external packet storage via Corelight, BYO hardware, or cloud storage (Amazon S3). Corelight’s sensor management console lets analysts create new capture rules at configurable byte-depths based on capture triggers such as alerts, protocol type, and encryption status. Analysts can then retrieve packets via their SIEM or Corelight Investigator by clicking the PCAP URL embedded in the connection log, which opens the packets in Wireshark for further analysis.
100% network coverage
Configure Smart PCAP to capture packets for all connections not already captured via Corelight logs, and also capture the first 2,000 bytes of all unencrypted traffic. This configuration drives comprehensive network visibility by giving security teams a source of evidence for every connection in their environment via Corelight logs, captured packets, or both.
