Intrusion detection system
Corelight integrates high-performance signature-based alerts with network context—lowering response times and revealing attack impact.
Close the gap between alert and answer
Knowing which alerts are dangerous, and which aren't, isn’t easy. Corelight's Open NDR Platform fuses signature-based IDS alerts from Suricata with Zeek® network evidence. This correlated package is then delivered to your SIEM, XDR, or Investigator—Corelight’s SaaS analytics solution. With this deep integration, you can accelerate identification, risk assessment, containment, and closure.

Zero in on true positives
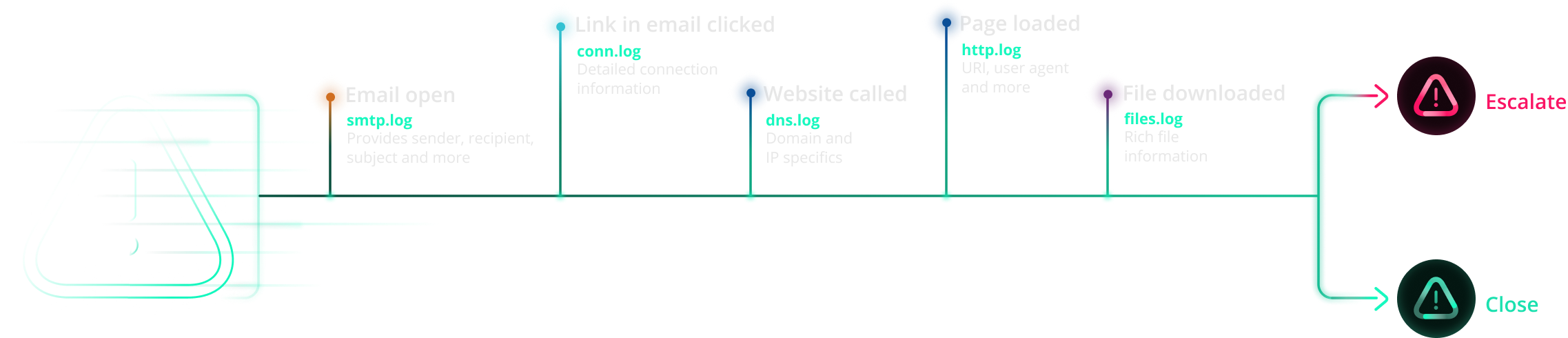
When an IDS alert fires, Corelight packages that alert together with all pertinent network evidence, integrating signal and context. This package contains a unique key that makes it easy for an analyst to find related data using basic SIEM queries. Accelerate incident response with Zeek and Suricata.
Resolve critical cases with speed and accuracy
Triage
Someone attempts a SQL injection, triggering an IDS alert. How do you know if it was successful?
Investigate
See if a SSH session was scripted, if someone is typing, or if they’re moving files around.
Remediate
Watch how our SOAR or XDR integration + playbooks speed up remediation.
Consolidated and fully supported
Corelight's Open NDR Platform consolidates multiple network and security data sources to provide uniform data across your cloud, physical, or container deployment. It also enables you to enrich logs and link related data. Your Technical Account Manager can lead you through the process of replacing legacy data sets.

The data you need—that’s it
Corelight can maximize the signal to noise ratio by filtering data, only providing your SIEM with just the information you need. Your Technical Account Manager will help you tune your system performance to meet organizational needs, up to hundreds of gigabits per second.

Compare open to closed NDR
This free ESG white paper explains the reasons to consider an open-source solution.
