New Corelight app for Splunk: Making network-based threat hunting easier
Here's how the new Corelight app for Splunk makes network-based threat hunting easier.
In support of Corelight’s latest software release, v19, we are pleased to launch our newest installment of the Corelight App for Splunk (Corelight App) and the Corelight Technical Add-on (TA). Both software packages are available on Splunkbase. The Corelight App has been updated with a new dashboard highlighting features from our Encrypted Traffic Collection, plus support for new data on existing dashboards with the newly integrated Corelight Suricata log, Stepping Stones, and Community ID.
New Dashboard:
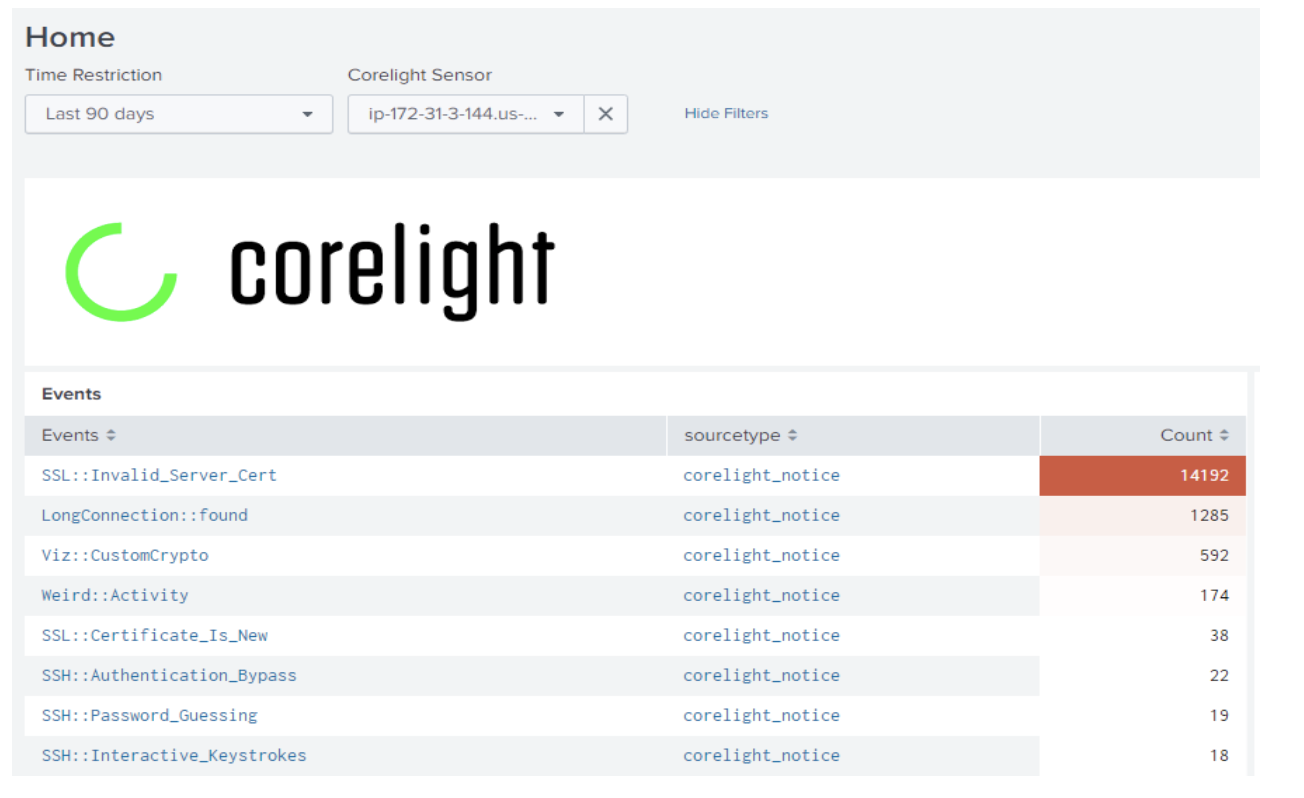
SSH Inferences
When we released our Encrypted Traffic Collection (ETC) with v18, it included a number of inferences about the encrypted SSH connections seen by the sensor. This blog post highlights some of the specific inferences and the techniques used to discover them. For v19 we’ve added even more and there are now more than 25 inferences added to the SSH log. These include understanding the type of authentication used, file activity, detections for scanning and attack behavior, and much more. A single inference alone may not be malicious, but taken together in the context of a threat hunt or an investigation they can help pinpoint anomalous connections and highlight potentially malicious behavior, all without the need for decryption.
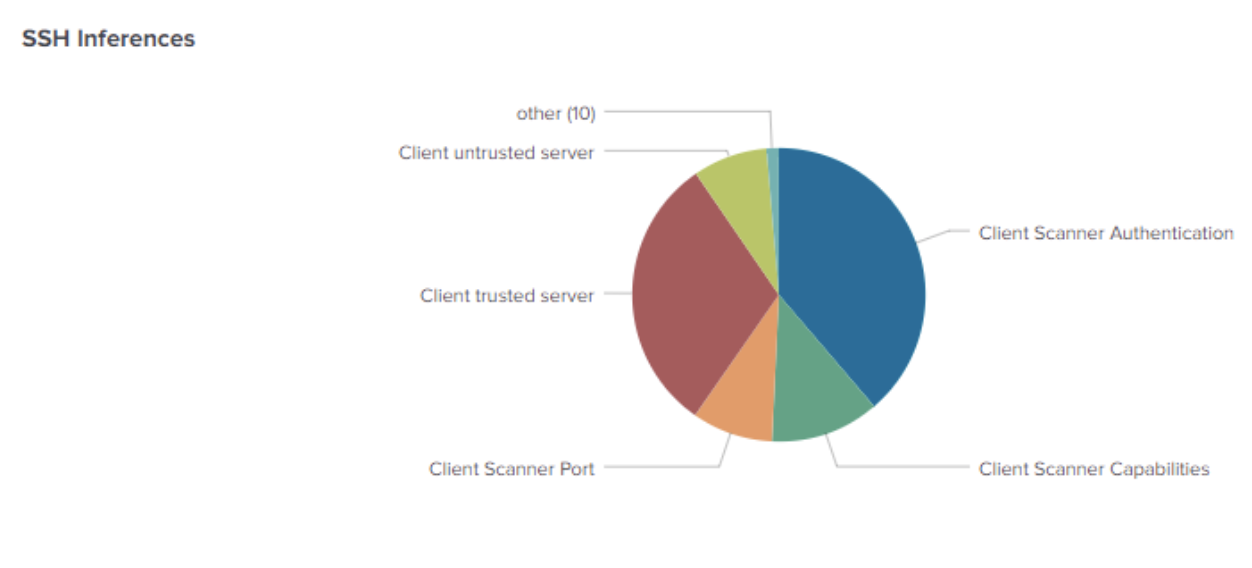
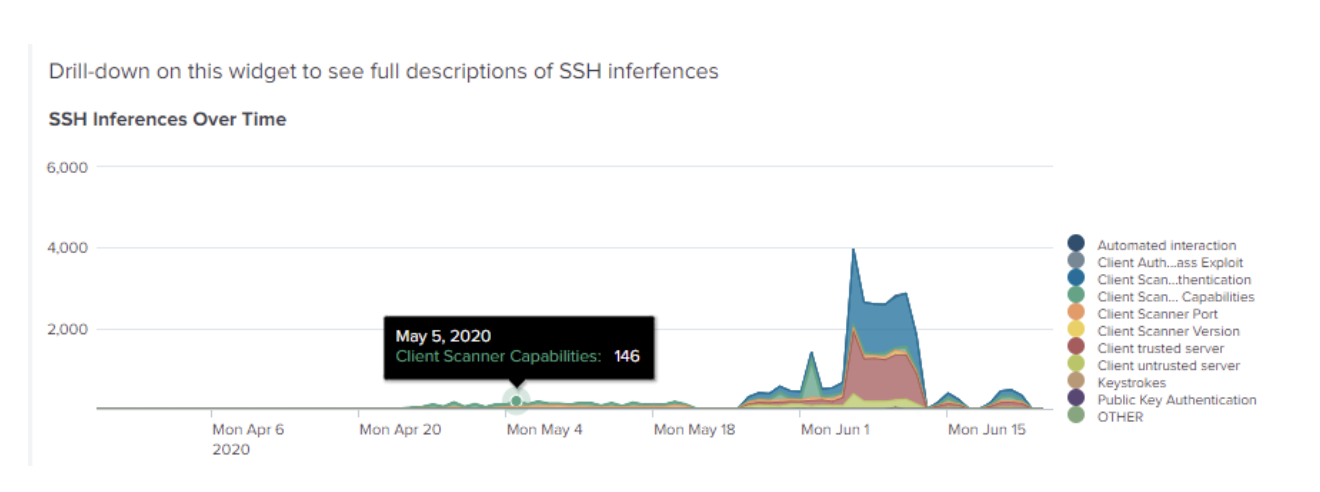
To help make sense of all the different inferences, the Corelight App now features easy access to SSH Inference activity and includes descriptions to make them immediately understandable. Many of these events generate Notices which are highlighted on the homepage of the Corelight App. A pre-built dashboard is available in the Security Workflows drop down menu to help investigate a single event or get relevant summaries of all SSH inferences. The interactive dashboard also provides time, inference, and advanced filtering. Summary widgets for SSH Inferences allow security analysts to drill down into a prevalent inference or a time slice – for example zooming in on authentication bypass attempts during a specific time and watching for successful authentications. An additional set of tables provide summaries of SSH host pairs, HASSH fingerprints, host keys, and displays raw logs to quickly provide the context of the entire alert directly, rather than requiring an additional search.
New data for existing dashboards:
SSH Stepping Stones & DNS over HTTPS
As part of the updates to the ETC in v19, we’ve also added new packages to identify DNS over HTTPS (DoH) and SSH stepping stones. DoH identification adds a new field to the ssl log to indicate when an encrypted DNS transaction has occurred. SSH Stepping Stones creates an entirely new log to highlight when SSH is used to jump between intermediary connections, which could indicate an attacker moving within your network or trying to hide their tracks. This blog post highlights all of the new updates to the ETC in more detail. These techniques are revealed by the new Splunk App in the notices and investigation dashboards to quickly identify anomalous traffic.
Suricata
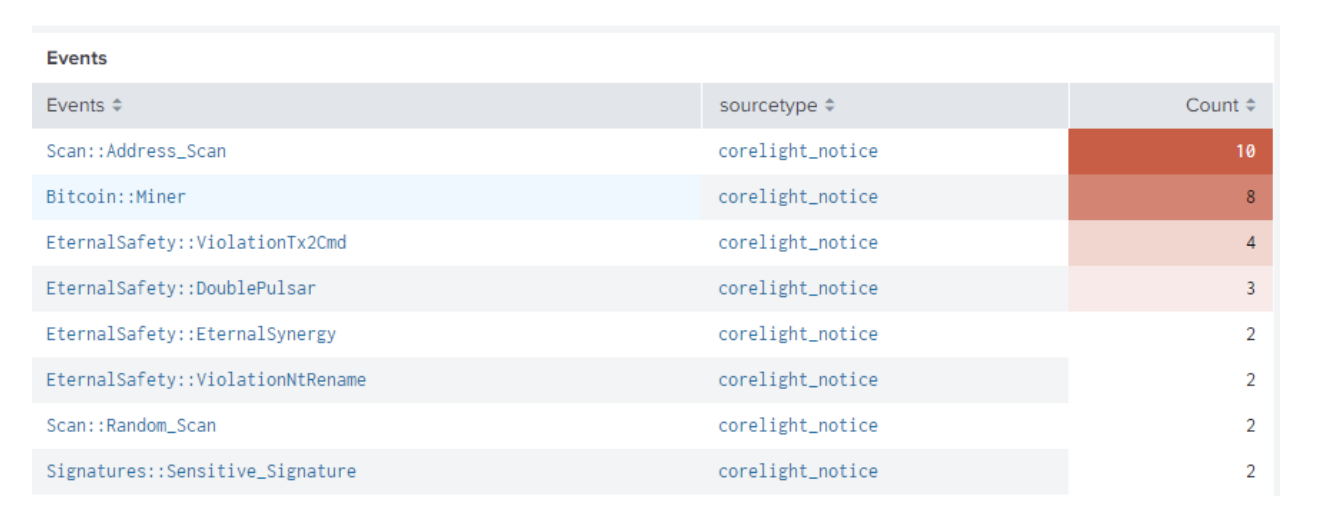
In Corelight’s latest v19 release, Suricata is now available on the Corelight AP 3000 appliances. Suricata is a high performance network intrusion detection system (IDS) and the industry standard for open-source signature matching. Corelight has merged Zeek and Suricata together in a powerful combination which provides more than just these two tools running side by side. Corelight’s new Suricata log directly links Suricata alerts to Zeek’s connection and protocol logs (using the connection identifier or UID) to accelerate investigations by providing immediate access to the context of the alerts. The new Splunk App highlights the top Suricata alerts on the homepage to make it simple for an analyst to jump directly to an investigation as well as context for every alert to prioritize response with alert tuning.
Community_ID
How often does a SOC solve an investigation with only one source of data? Corelight recognized this doesn’t happen often and developed the ability to link disparate data sets with a foreign key: the Community ID. Several products (e.g., ECS, HELK, Moloch, MISP, OSquery, Suricata) have embraced this specification, and we are excited to support it in the new Splunk App. You can see the Community ID in the Corelight logs and dashboards as well as generate it at search time for non-Corelight data, expanding the reach of this simple but powerful field. Community ID is just one more way that Corelight empowers analysts by offering the ability to pivot from NDR to EDR data to increase investigation efficiency.
We hope that you like the new Corelight App for Splunk and let us know if you have feedback for improvements or feature requests. Keep watching our blog for news about upcoming releases, new 0-day detections and more.
Here's how the new Corelight app for Splunk makes network-based threat hunting easier.
I’m pleased to announce that Corelight sensors now support the Elastic Common Schema (ECS) via our Corelight ECS Mapping.
The Corelight for Splunk app is now available! Using the new app you can now monitor the health and performance of Corelight Sensors in Splunk and...