Why evidence-based security
Elite defenders recognize that alerts can—and will—be missed. They know that an evidence-first strategy is their best opportunity to catch advanced adversaries in the act.
Risk thrives in uncertanity. The best defense is evidence.
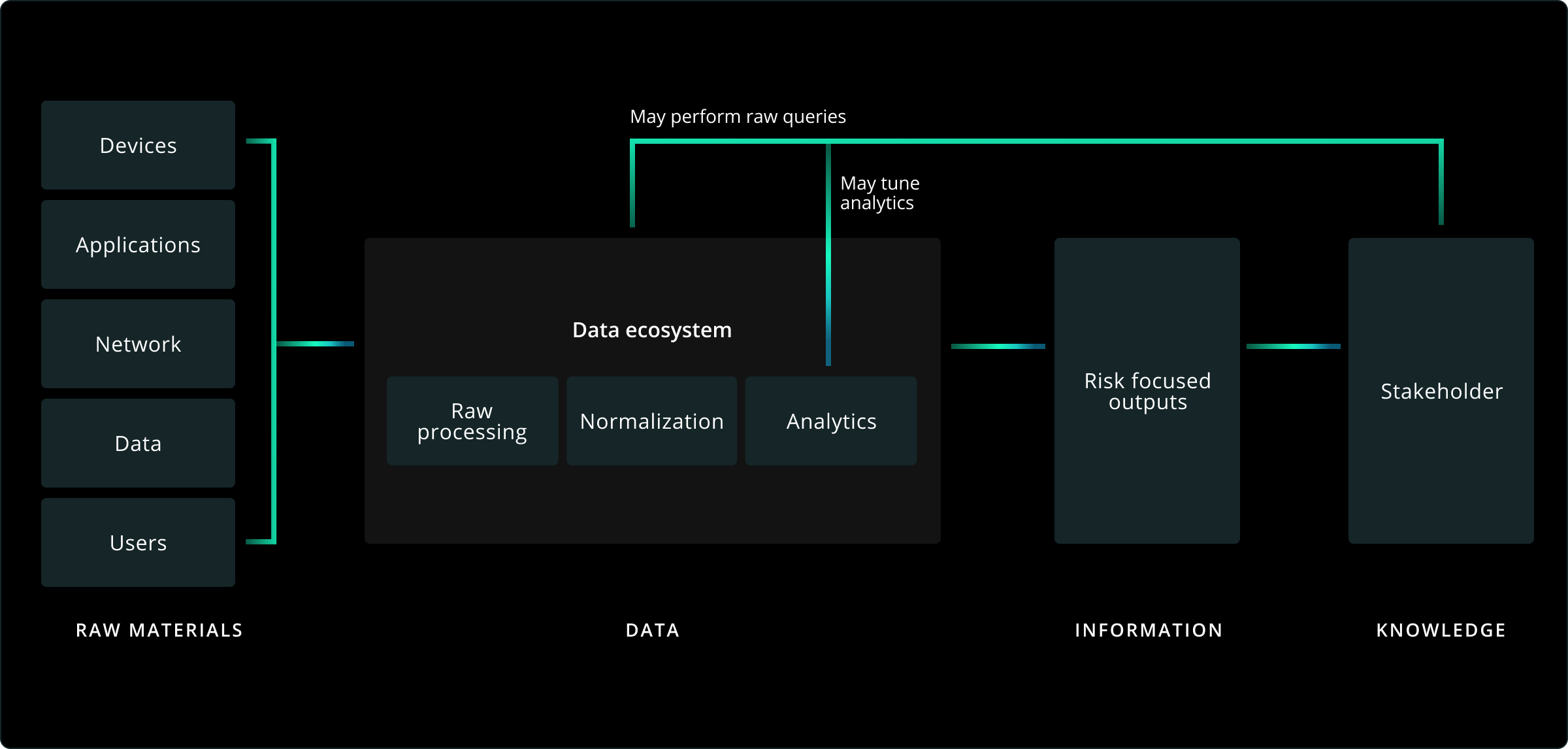
Cyber risk is an inevitable part of any organization's security posture. Uncertainty makes this risk even harder to deal with. That's why the most sophisticated defenders adopt an evidence-based approach to network security. This strategy removes uncertainty so they can make the right decision in critical moments—when an alert comes in, when a major attack is detected, or when they're remediating a breach—so they can deal with risk from the most informed position.
Complete visibility
Gain a commanding view of your organization and all devices that log onto your network—with access to details such as DNS responses, file hashes, SSL certificate details, and user-agent strings—rapidly, without relying on other teams to respond to data requests.
Next-level analytics
Machine learning—fueled with network evidence—delivers powerful insights so you can focus on the most critical detections. Corelight’s high-fidelity, correlated telemetry powers analytics, machine learning tools, and SOAR playbooks, improving efficiency and unlocking new capabilities so that you can make better decisions—faster.
Faster investigation
Correlate alerts, evidence, and packets so you can establish baseline network activity and integrate that context directly into your existing workflows. Reduce false positives and your alert backlog—with no redesign or retraining necessary. You get a full view of every incident so you can validate containment and remediation.
Expert hunting
Rich, organized, and security-specific evidence enables you to spot vulnerabilities, intruder artifacts, critical misconfigurations, signs of compromise and undetected attacks, further mitigating risk.
The evidence bank
Evidence is the currency cyber defenders use to pay down security debt, balancing the value equation between adversaries and the enterprise. Defenders can use evidence proactively, identifying and protecting structural risks within our zone of control.