Announcing The New Corelight for Splunk App
The Corelight for Splunk app is now available! Using the new app you can now monitor the health and performance of Corelight Sensors in Splunk and...
The Corelight App for Splunk provides the foundation for organizations to boost SOC effectiveness and productivity by using Corelight data in Splunk. In this blog, I’ll walk through how the Corelight App leverages Splunk’s Common Information Model (CIM) to enhance users' search experience when they are using Corelight data.
The Corelight App for Splunk optimizes the data streamed to Splunk using the Common Information Model. A quick aside—almost every vendor has, or supports one data model, but Corelight supports many natively. The Splunk CIM is implemented as an add-on Splunk app that contains a collection of data models, documentation, and tools that support the consistent, normalized treatment of data for maximum efficiency at search time. For those unfamiliar there are twenty four data models, and Corelight support these seven:
| Data Model | Corelight |
| Certificates |
|
|
|
| Intrusion Detection |
|
| Network Resolution (DNS) |
|
| Network Sessions |
|
| Network Traffic |
|
| Web |
|
This means that once you install the Corelight App for Splunk and configure Splunk’s CIM app, all of the data, field names, and values that are already correlated within Corelight’s context-rich alerts are normalized, validated and available within several Splunk data models. With this seamless process, Splunk users can accelerate their SOC workflows by being able to immediately access and action the data they need for investigations and long-term threat hunting. Ultimately, Corelight wants all security teams, regardless of the technology that they’re using, to have the opportunity to enhance their search experience and improve their overall effectiveness.
Configuring the CIM is as easy as clicking the “Apps” drop-down menu and then selecting “Manage Apps”.
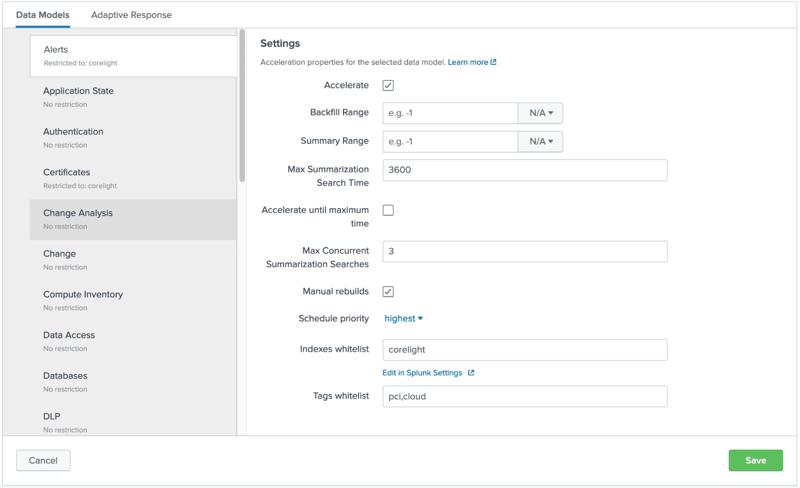
Next, select “Setup” from the Splunk Common Information Model app under the action column. You will be presented with a UI for each of the data models. In this example we have configured acceleration and an index whitelist.
Download the Corelight for Splunk and Splunk CIM apps and see for yourself how easy it is to get Corelight data into Splunk and quickly begin using accelerated data models within Splunk.
Stay tuned to our blog for updates! For guidance on threat hunting with Splunk and other security solutions, I also recommend visiting the Corelight YouTube channel.
For more about Corelight and Splunk’s strategic partnership, check out this page.
The Corelight for Splunk app is now available! Using the new app you can now monitor the health and performance of Corelight Sensors in Splunk and...
We are pleased to launch our newest installment of the Corelight App for Splunk (Corelight App) and the Corelight Technical Add-on (TA).
Here's how the new Corelight app for Splunk makes network-based threat hunting easier.